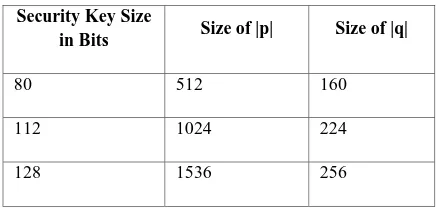
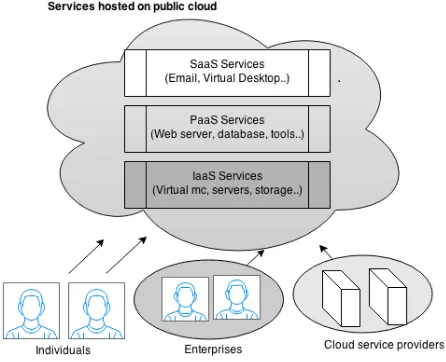
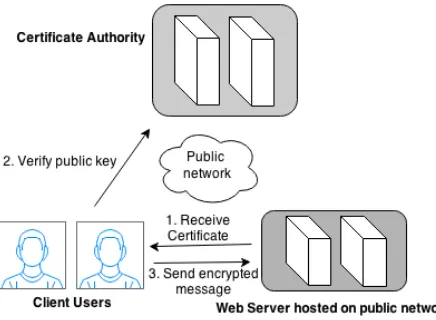
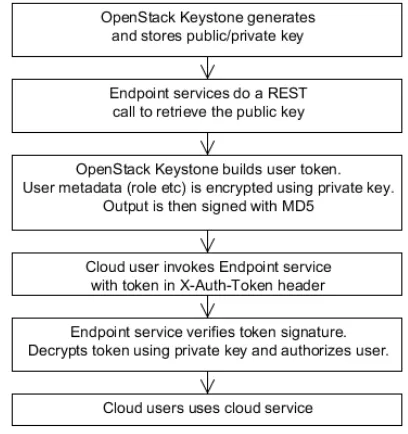
Data Confidentiality in Public Cloud: A Method for Inclusion of ID PKC Schemes in OpenStack Cloud
Full text
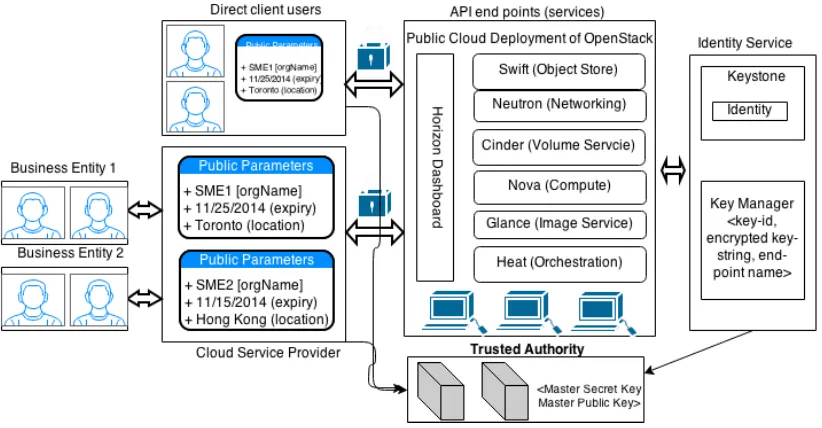
Figure
Related documents
investigated for damage separately. For rapid impact assessment, remote sensing data sets can provide important information since they can map the extended areas quickly and in
In the risk evaluation details page, you can compare the transaction to transactions that have been registered with the same card number, BIN, IP address, email
that all Traditions should be regarded as fictitious until their authenticity is objectively established. Taking for granted the mechanics of "back projection" of
‘We were impressed with the way Huntsman® integrated into our data infrastructure,’ the Security Team Manager makes the point, ‘and how well it works with our other security
That the data contain information on each person for 2 years after the potential point of diversion is particularly important for this sample because, unlike pre-booking diversion,
The deviation of clustering coefficient C of the graph from the overall mean of the four groups as a function threshold T at three frequency bands..
• Other top municipalities in 2007 thus far are Atlantic City with $151.4 million of work, Newark with $130.7 million (both of these figures are mentioned above – do you want to
PCA analysis supports the concept that caries risk is divisible into patterns attributable to distinct risk factors that work in accord: in the total sample two different