secure Audio Data Transfer Over Internet Using Steganography
Full text
Figure
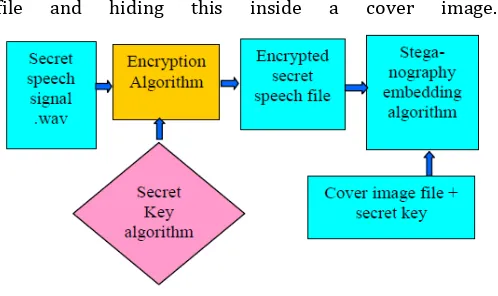
Related documents
Conservation of gene order: The six putatively fused chromosomes for which we positionally mapped new markers (Figure 2) had a combined map length of 627 cM, in comparison with
The objective of this study is to develop a rapid, sensitive, and real-time reverse transcription loop-mediated isothermal amplification (RT-LAMP) method for the detection of
Adapun manfaat dari penelitian ini adalah sebagai sumber informasi mengenai tingkat pencemaran logam berat Timbal (Pb), Tembaga (Cu), Kromium (Cr), Kadmium (Cd), Besi
As with the international news media, Oromo social media activists, Human Rights Watch, and Amnesty International, violence was a major theme of government officials’. discussion
symbiotic; without teaching and research, good practice becomes lost to future generations of learners; and without good links to practice, professional higher education
Genistein may inhibit the growth of human mammary epithelial (HME) cells by augmenting transforming growth factor beta (TGF beta) signaling. Structure of the ligand-binding domain
The main advantage of the project is to guide the student to achieve more in their career by connecting them with the former students who are currently working
Because antidumping laws do not assure indigents access to private hospi- tals for nonemergency medical care, public hospitals must provide a high proportion of