FRAUD DETECTION IN CARD NOT PRESENT TRANSACTIONS BASED ON BEHAVIORAL PATTERN
Full text
Figure
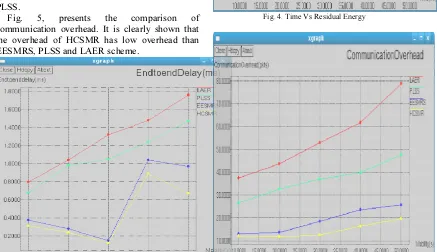
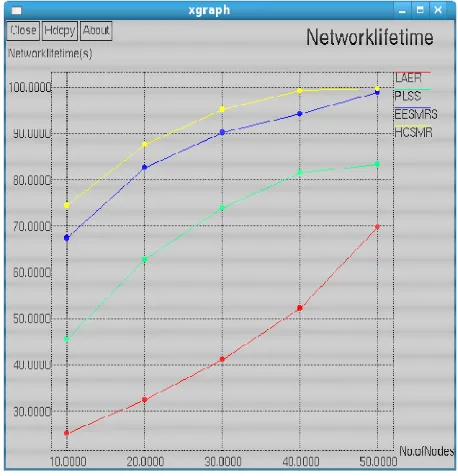
Related documents
As in the case of the scalar Helmholtz dark soliton [26], W has the physical interpreta-. tion of velocity summation in the unscaled
In particular, we demonstrate that Helmholtz-Kerr dark solitons (strictly speaking “solitary waves”), which are exact analytical solutions of a non-integrable wave equation,
We discussed the classification of congestion control algorithms based on the network awareness, various media content aware congestion control protocols with its pros
tradition of the social sciences (Schwandt, 2000), there are actually fundamental epistemological differences between doctrinal analysis and all styles of scientific
The research method adopted is a literature review, which has focused on two main themes: a) the understanding of the ancient method of analysis and synthesis; b) the current concept
synchronisation between the transient laser pulse and the RGA mass scan results in variable partial pressure readings when analysing both neutral and ionic species.. LAMS is able