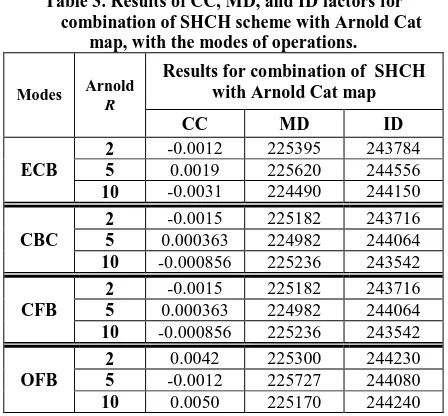
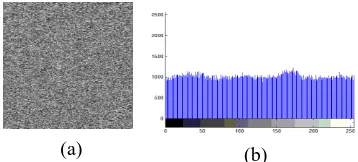
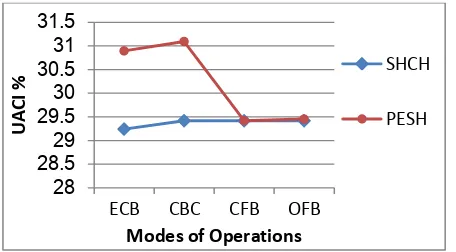
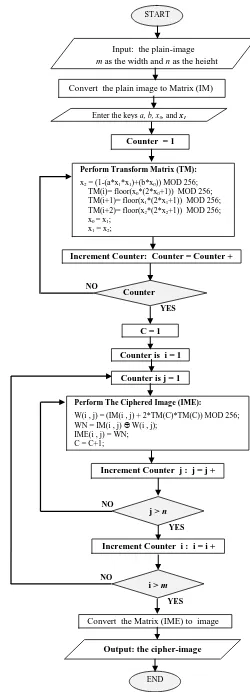
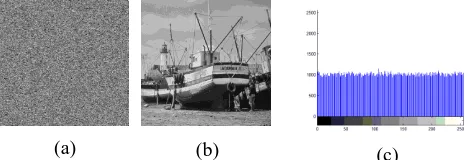
A Proposed Encryption Scheme based on Henon Chaotic System (PESH) for Image Security
Full text
Figure


Related documents
Based on the Web query assigned by the user’s analysis the goal, the goal identification is used to improve quality of search results.. In existing system with use
An analytic center cutting plane method for solving semi-infinite variational inequality problems. Merit functions for complementarity and related prob- lems:
We examine relationships between fame and premature mortality and test how such relationships vary with type of performer (eg, solo or band member) and nationality and whether cause
Eingeschlossen wurden Patienten, die im Sinne dieser Studie positiv für eine Lumbopelvine Bewegungsstörung waren, also bei Vorliegen eines
As mentioned before, an advantage of our approach over the pairwise model is that it is not “edge-factored.” Each greedy decision can rely on all of the information contained in
Table 3 and Fig. 4 illustrate the temporal evolution of the different networks at the term level. The communication networks aggregated in the second and third terms are very
EURASIP Journal on Applied Signal Processing 2004 12, 1886?1898 c? 2004 Hindawi Publishing Corporation Design of Farthest Point Masks for Image Halftoning R Shahidi Electrical &
The main focus of this study is to analyze a high input majority voter based on 3 to 8 decoder for reliability using Bayesian network at a circuit level.. The