International Journal of Innovative Technology and Exploring Engineering (IJITEE) ISSN: 2278-3075, Volume-8 Issue-11, September 2019
Abstract: By and by days the market of PDA is creating at a quick. Everyone has a versatile, tablet, fablet (tablet with calling office). Flexible customer will accomplish 6.5 billion preceding the completion of 2012,6.9 billion preceding the completion of 2013.Together with a perilous improvement of the convenient applications and ascending of appropriated figuring thought, compact disseminated registering (MCC) has been familiar with be a potential development for adaptable organizations. MCC consolidates the disseminated figuring into the flexible condition and beats obstacles related to the execution (e.g., battery life, amassing, and information transmission), condition (e.g., heterogeneity, flexibility, and openness), and security (e.g., steadfastness and insurance) discussed in compact enlisting. This paper gives an information about adaptable disseminated figuring application security, issues . The issues, existing plans and procedures are discussed.
Index Terms: About four key words or phrases in alphabetical order, separated by commas.
I. SCOPEOFTHEWORK
Compact disseminated registering is one of flexible advancement floats later on since it solidifies the upsides of both convenient figuring and circulated processing, thusly giving perfect organizations to versatile customers. The essential of movability in appropriated registering delivered Mobile disseminated figuring. MCC gives increasingly potential results to get to organizations in accommodating manner. It is typical that after specific years different adaptable customers will going to use dispersed processing on their mobile phones. As shown by a progressing report by ABI Research, a New York-based firm, more than 240 million businesses will utilize cloud benefits through mobile phones by 2015.That traction will drive pay of flexible disseminated processing to $5.2 billion. With this prominence, this manuscript has given a framework of adaptable appropriated processing in which its definitions, security, problems and inclinations are displayed. Prevalently it deliberated dataset security away in cloud and hugeness of data security. This manuscript has researched different parts
Revised Manuscript Received on September 03, 2019
Dr.A.Sai Hanuman, Professor, Dept of CSE, Gokaraju Rangaraju Institute of Engineering and Technology, Bachupally, Hyderabad, Telangana.
Dr.P.S.V.Srinivasa Rao, Professor, Dept of CSE, Vignan’s Institute of Management & Technology for Women, Ghatkesar, Medchal Dist, Telangana.
Dr. J.Sasi Kiran , Principal &Professor, Dept of CSE, Farah Institute of Technology, Chevella, Rangareddy, Telangana.
Dr.G.Charles Babu, Professor, Dept. of CSE, Malla Reddy Engineering College(Autonomous), Maisammaguda, Secunderabad, Telangana.
Dr.B.Sankara Babu, Professor, Dept of CSE, Gokaraju Rangaraju Institute of Engineering and Technology, Bachupally, Hyderabad, Telangana.
for giving data security so Mobile Cloud Computing might be comprehensively recognized by different customers in future. It moreover suggested an instrument to give arrangement, get the opportunity to control similarly as uprightness to versatile customers. The handling capacity of convenient structures is improved by Cloud enlisting. Mobile phones can rely upon conveyed processing to perform computationally genuine exercises, for instance, looking data mining, etc. The use of flexible circulated registering vanquishes execution related tangles for instance exchange speed, amassing point of confinement and battery life, similarly as condition related issues for instance openness, flexibility and heterogeneity. Dispersed registering is changing the Internet handling establishment. Since by far many organizations are access from cloud over Internet, MCC has been introduced. The security hazard has pushed toward getting to be obstruction in the brisk improvement and generous usage of flexible conveyed processing perspective. The security perils have advanced toward getting to be catches in the quick flexibility of the versatile appropriated figuring perspective. Basic undertakings have been submitted in research affiliations and the insightful network to build secure versatile appropriated processing circumstances and systems. This paper reviews the possibility of adaptable conveyed figuring similarly as problems of security normal inside the setting of convenient application & disseminated registering. The standard vulnerabilities in structures with possible game plans are discussion about here.
Mobile phone contraptions are commonly used in our step by step lives. Regardless, these devices show obstructions, for instance, short battery lifetime, confined computation control, little memory gauge and unordinary framework arrange. As such, different courses of action have been proposed to alleviate these obstructions and widen the battery lifetime with the usage of the offloading system. In this manuscript, a new framework is suggested to offload genuine count endeavors from the mobile phone to the cloud. This framework uses a headway model to choose the offloading decision logically subject to four essential parameters, to be explicit, essentialness use, CPU use, execution time, and memory use. Additionally, another security layer is given to guarantee the moved data in the cloud from any attack. The preliminary outcomes showed that the structure can pick a sensible offloading decision for different sorts of adaptable application assignments while achieving colossal execution improvement. Also, not exactly equivalent to past methodologies, the structure can shield application data from any peril.
Objectives of the work
An Efficient and Secured Framework for Mobile
Cloud Computing
•
To plan Mobile Cloud Computing: Issues, Security, Advantages, and Trends• To ponder Privacy and Security of Mobile Cloud Computing (MCC)
• To structure Mobile Cloud Computing Issues and Solution Framework
• To look at An Efficient and Secured Framework for Mobile Cloud Computing
• To ponder secure data planning framework for versatile appropriated processing
II. LITERATUREREVIEW
C. Erway, A. Kupcu, C. Papamanthou, and R. Tamassia (2009) In versatile conveyed processing, phones can rely upon appropriated figuring and information storing resource for perform computationally thought exercises, for instance, looking, data mining, and media dealing with. Despite giving ordinary estimation organizations, compact cloud moreover improves the assignment of standard uniquely delegated framework by seeing mobile phones as organization center points, e.g., identifying organizations. The identified information, for instance, territory encourages, prosperity related information, should be arranged and set away in a sheltered style to guarantee customer's security in the cloud. To this end, we present another adaptable cloud data taking care of framework through trust the board and private data separation. Finally, a use pilot for improving youngsters' driving prosperity, which is called FocusDrive, is acquainted with demonstrate the game plan.
A. Fiat and M. Naor (1994) Cloud preparing is another and promising advancement that is changing the perspective of ordinary Internet enrolling and no doubts the whole IT industry. Dispersed figuring is foreseen to stretch out in the versatile condition using on the fast advances in remote access developments. These adaptable applications are worked around compact circulated registering frameworks and models. In the Mobile Cloud condition, customers might remotely store their data similarly as acknowledge high gauge on-demand cloud applications without the hindrances of getting and keep up their own one of a kind neighborhood hardware and programming. In any case, data security is up 'til now a vital concern and is the standard block shielding circulated figuring from being even for the most part grasped. This stress begins from the manner in which that sensitive data set away in the open fogs is administered by business expert centers that most likely won't be totally dependable. In that limit, there are a couple of security and assurance issues that ought to be tended to. This segment gives an outline on the appropriated processing thought sought after by a portrayal on convenient dispersed registering and the various security issues important to the flexible circulated figuring condition.
L. Cheung, J. Cooley, R. Khazan, and C. Newport (2007) Mobile gadgets (e.g., tablet, wireless, pcs, etc) are dynamically transforming into a fundamental bit of human life. These Mobile devices still need in resources diverged from a standard information taking care of contraption, for instance, PCs and workstations. The response for thrashing of these challenges is Mobile Cloud Computing. We propose another adaptable framework that enables direct use of cloud resources for increment the capacity of advantage obliged
PDAs. The basic features of this model join the package of a singular application into different fragments. Compact applications can be executed in the PDA or offloaded to the cloud clone for execution. The results exhibits that the execution of execute application on adaptable or cloud the extent that memory exhausted using unmistakable detachment and number of centers are shut. Most of benefits ate up on convenient mobile phone will decrease around to the half of memory used for running application on the adaptable so to speak. On the contrary side, Although Cloud Computing is an unprecedented headway in the domain of preparing, there moreover exist disadvantages of dispersed registering, for instance, security of data. As such, there is a remarkable need of encryption procedure with a lot of security and with immaterial key size. There for, the principal center for ensuring security is to developed new cross breed cryptography show. Along these lines, new cross breed cryptography show is created for achieving security in Mobile Cloud Computing. The results exhibit the power of new computation. The rule duty of our investigation is to develop a safe flexible cloud establishment that will enable wireless applications that are passed on both with respect to data and figuring.
D. Boneh, X. Boyen, and E.J. Goh (2005) Smartphone devices are commonly used in our step by step lives. Regardless, these contraptions show confinements, for instance, short battery lifetime, compelled estimation control, little memory measure and surprising framework organize. Thusly, different courses of action have been proposed to direct these confinements and expand the battery lifetime with the usage of the offloading technique. In this paper, a novel structure is proposed to offload genuine figuring endeavors from the phone to the cloud. This framework uses a streamlining model to choose the offloading decision logically subject to four central parameters, to be explicit, imperativeness use, CPU use, execution time, and memory use. In addition, another security layer is given to guarantee the moved data in the cloud from any strike. The test outcomes showed that the framework can pick a fitting offloading decision for different sorts of adaptable application assignments while achieving basic execution improvement. Additionally, not exactly equivalent to past strategies, the structure can shield application data from any risk.
International Journal of Innovative Technology and Exploring Engineering (IJITEE) ISSN: 2278-3075, Volume-8 Issue-11, September 2019
we suggest an Attribute Based Data Storage (ABDS) structure as a cryptographic access control system. The ABDS reaches the data theoretical optimality to the extent restricting estimation, accumulating & correspondence overheads. Especially, ABDS bounds cloud organization charges by reducing correspondence overhead for data organizations. Our implementation assessments display the quality of security & efficiency of the showed course of action similar to computation, correspondence, and limit.
G. Ateniese, R. Expends, R. Curtmola, J. Herring, L. Kissner, Z. Peterson, and D. Tune (2007) Cloud enlisting is a promising development that is changing regular Internet figuring perspective and industry of IT. With progression of remote access developments, appropriated processing is depended upon to develop to flexible circumstances, where PDAs and sensors are utilized as data gathering center points for cloud. In any case, customers' stresses over data security are the essential preventions that hinder appropriated processing from being comprehensively gotten. These stresses are begun from the manner in which that sensitive data lives in open fogs, which are worked by business pro associations that are not trusted by owner of data. Therefore, new secure organization structures are relied upon to address security stresses of customers for utilizing disseminated registering methods.
III. METHODOLOGY
The MCC will be essentially the interconnection of appropriated registering, flexible handling and remote frameworks to influence mind blowing computational resources for versatile customers, to orchestrate directors, similarly as conveyed processing providers. This openness enables adaptable customers to utilize cloud structure to vanquish the confines of compact development. A complete aim of MCC is to empower execution of rich convenient applications on phase of PDAs, with a rich customer experience. The MCC gives business chances to versatile framework managers similarly as the providers of cloud. Even more thoroughly, MCC might be described as a rich adaptable figuring development that keep up uprightness among resources of contrasted fogs and framework propels toward that give, indefinable limit, and transportability to get countless telephones wherever. The central designing is produced using the sections: adaptable customers, compact managers, organize get to providers (lSP), and cloud expert communities, independently. The building is showed up in Figure. Flexible customers, convenient customers are the end customers that send diverse organizations through accommodating cell phones, tablets that are in developments.
Figure: Mobile Cloud Computing Architecture
MOBILE OPERATOR
The adaptable director are remote authority association that has the rights to offer access to customer to organizations like radio range, billings, remote system, retail ,customer care & giving spine organizations. A basic typical for a convenient framework head is that it should guarantee or control access to a radio range license from an authoritative or government component. A second most portraying typical for a MNO is control the parts of the framework establishment imperative to offer organizations to endorsers over the approved range.
Figure 1:Layered architecture of MCC
The layer configuration is showed up in Figure 1. The spine layer builds up security perception on the physical structures of cloud. These helpers in checking the machines &servers in cloud establishment. The structure layer screens VMs in cloud. Distinctive activities, for instance, Storage check, VM isolation, VM development, audits Cloud Service Monitoring&Risk Evaluation are done in this layer to confirm cloud have organizations. Application layer executes works out, for instance, customer the officials, key organization, approval, endorsement, encryption and data blend. To pull in clients, the cloud authority center (CSP) wants to concentrate on all the security problems to provide an exceedingly secure condition.
Security risks
1. Protection as cloud condition incorporates immense no. of customer to give organization, constructs far reaching no. of ways of adaptable customers and applications. Each customer's data should be secure and covertly directed. Simply affirmed customer has rights to get to endorsed data. 2. Security Privacy is need of a person to control customer’s near and dear information. In cloud various potential results like insider customer threats, outside attacker risks, data spillage, etc can hurt security of cloud customer.
3 .Multi-inhabitance in multi-residency of cloud, social affair of customer shared organization given by single programming or application.
each convenient customer's data is separated and remains imperceptible to other flexible customer.
4. Thing reusability-A model prepared for making cloud based applications with reusability by recouping the parts from the cloud section vault by using configuration organizing counts and distinctive recuperation procedures. 5. Data remanence-It is the remaining depiction of data that have been some way or another or another apparently annihilated or ousted. Data protection could be broken inadvertently, in light of data remanence.
6. Programming Confidentiality-It is suggests trusting that particular application or strategies will keep up and handle the customer's near and dear data in secure manner.
7. Genuineness Integrity in cloud insinuates protected from unapproved abrogation, change, theft. The data genuineness in direct terms is upkeep of soundness of any data in the midst of trades like trade, recuperation or storage. The deletion, alteration might be accidentally or intentionally.
8. Endorsement: It is the segment by which a system makes sense of what measurement of access a certain affirmed customer must need to confirm resources compelled by structure.
IV. RESULTS Performance Evaluation
Computation Performance of PP-CP-ABE:
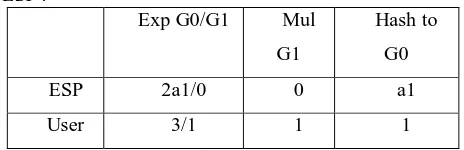
To estimate the execution of showed PP-CP-ABE plan, we survey the count overhead of master associations &customers subject to both speculative examination and preliminary outcomes. Directly off the bat, we examination the amount of expensive cryptographic exercises over G0 and G1, i.e., coordinating, exponentiation, duplication, performed by master centers and customers' contraptions. In our examination we acknowledge that the passage course of action TESP has a1 characteristics related by an AND reasonable entryway and TDO simply has 1 property. Additionally, the root center point is an AND gateway. In the going with table, we considered the amount of exponentiations, increments and hash to G0 exercises realized on customer side& ESP side in encryption re-appropriating, where a1 is the amount of properties in TESP :
Exp G0/G1 Mul
G1
Hash to
G0
ESP 2a1/0 0 a1
User 3/1 1 1
We additionally give an examination of the quantity of exponentiations, duplications, reversal, and matching activities caused by decoding redistributing on client side &DSP side as appeared in the accompanying table, where a1 is the quantity of characteristics in TESP.
Exp
G1
Mul
G1
Inv
G1
Pairing
ESP a1 2a1 a1 2a1+1
User 1 2 1 0
From above examination, we might observe that count overhead is immediate for pro associations (DSP& ESP) and consistent for the customer. Among all exercises, mixing will be more computationally focused.
Beside the speculative examination, we in like manner performed exploratory estimations. In perspective on CP-ABE open source adventure, we completed &surveyed the PP-CP-ABE on PC with 1.6GHz Intel Atom processor running Linux2.6.32. The calculation time is evaluated with the use of clock ticks returned by clock_t clock(void) work in standard C library. To depict that a substantial part of estimation overhead will be re-appropriated to authority associations, we run server &customer on a comparative stage and recorded the amount of clock ticks.
[image:4.595.52.284.559.634.2]In Figure 2, we took a gander at count overhead achieved on authority associations and customers in encryption and unscrambling re-appropriating. The computation overhead is resolved similar to 10 based logarithms, i.e., log10, of thousands (K) timekeepers ticks. As ought to be clear from figure, over 90% of encryption &over 99% of unscrambling estimation are executed by expert associations.
Storage Performance of ABDS:
We examine limit execution of ABDS and differentiation it and a couple of related cryptographic access control game plans: impart encryption plans (Subset-Diff), BGW broadcasting encryption, get the chance to control polynomial (ACP) plot. The execution is assessed the extent that figure content accumulating overhead, key amassing overhead (structure parameters and open/private keys set away on the customers & TA). We mean full scale number of customers in framework with N and a customer needs to share a record to some irregular plan of beneficiaries in the structure. The close outcomes are shown in Table 2. The Ciphertext Storage Overhead in Subset-Diff scheme, the degree of ciphertext is O(t 2 • log2 t • log N), with t as most prominent no. of interesting customers to deal the cipher text. For BGW plot, the cipher text gauge is O(1) or O(N 1 2 ) as uncovered. In ACP plot, degree of message relies upon the dimension of access control polynomial, those reciprocals to the amount of present recipients. Consequently, the message measure is O(N). To control a great deal of recipients S utilizing ABDS, the range of cipher text relies upon the amount of thing terms in f min S. In the makers construed lower bound& upper bound on typical no. of thing terms in a constrained SOPE. Likely, the typical no. of message required is ≈ log(N).
[image:4.595.325.538.618.706.2]V. CONCLUSION
Figure 2: Graph Performance evaluation of the encryption and decryption outsourcing
International Journal of Innovative Technology and Exploring Engineering (IJITEE) ISSN: 2278-3075, Volume-8 Issue-11, September 2019
storing organizations to check data board in open fogs. Particularly, our answer engages lightweight remote gadgets to securely store and recuperate their data in open cloud with unimportant cost. To this end, we suggested a novel Privacy Preserving Cipher Policy Attribute-Based Encryption (PP-CP-ABE) to verifyencoded data customer. Using PP-CP-ABE, light-weight gadgets might be securely redistribute heightened encryption &unraveling exercises to cloud authority communities, without revealing data & utilized keys. Furthermore, we suggested an Attribute Based Data Storage (ABDS) structure as a cryptographic access control framework. ABDS achieve information theoretically perfect the extent that constraining figuring, storing and correspondence overheads. Especially, ABDS limit the costs o cloud charged by cloud pro communities similarly as correspondence overhead for data organizations. Our execution assessments determine the security quality &profitability of our answer in regards to figuring, correspondence and limit.
REFERENCES
1. G. Ateniese, R. Burns, R. Curtmola, J. Herring, L. Kissner, Z. Peterson, and D. Song. Provable data possession at untrusted stores. In Proceedings of the 14th ACM conference on Computer and communications security, pages 598–609. ACM, 2007.
2. G. Ateniese, K. Fu, M. Green, and S. Hohenberger. Improved proxy re-encryption schemes with applications to secure distributed storage. ACM Trans. Inf. Syst. Secur., 9(1):1–30, 2006.
3. J. Bethencourt, A. Sahai, and B. Waters. Ciphertext-policy attributebased encryption. In SP ’07: Proceedings of the 2007 IEEE Symposium on Security and Privacy, pages 321–334, Washington, DC, USA, 2007. IEEE Computer Society.
4. D. Boneh, X. Boyen, and E.J. Goh. Hierarchical identity based encryption with constant size ciphertext. Advances in Cryptology– EUROCRYPT 2005, pages 440–456, 2005.
5. D. Boneh, C. Gentry, and B. Waters. Collusion resistant broadcast encryption with short ciphertexts and private keys. In Advances in Cryptology–CRYPTO 2005, pages 258–275. Springer, 2005. 6. D. Boneh, A. Sahai, and B. Waters. Fully collusion resistant traitor
tracing with short ciphertexts and private keys. pages 573–592, 2006. 7. D. Boneh and B. Waters. Conjunctive, subset, and range queries on
encrypted data. pages 535–554. Springer, 2007.
8. I. Chang, R. Engel, D. Kandlur, D. Pendarakis, D. Saha, I.B.M.T.J.W.R. Center, and Y. Heights. Key management for secure lnternet multicast using Boolean functionminimization techniques. INFOCOM’99. Eighteenth Annual Joint Conference of the IEEE Computer and Communications Societies. Proceedings. IEEE, 2, 1999.
9. L. Cheung, J. Cooley, R. Khazan, and C. Newport. Collusion-Resistant Group Key Management Using Attribute-Based Encryption. Technical report, Cryptology ePrint Archive Report 2007/161, 2007. http://eprint. iacr. org.
10. L. Cheung and C. Newport. Provably secure ciphertext policy abe. In CCS ’07: Proceedings of the 14th ACM conference on Computer and communications security, pages 456–465, New York, NY, USA, 2007. ACM.
11. C. Delerablee, P. Paillier, and D. Pointcheval. Fully collusion secure dy- namic broadcast encryption with constant-size ciphertexts or decryption keys. Pairing-Based Cryptography–Pairing 2007, pages 39–59. 12. S. D. C. di Vimercati, S. Foresti, S. Jajodia, S. Paraboschi, and P.
Samarati. Over-encryption: management of access control evolution on outsourced data. In VLDB ’07: Proceedings of the 33rd international conference on Very large data bases, pages 123–134. VLDB Endowment, 2007.
13. C. Erway, A. Kupcu, C. Papamanthou, and R. Tamassia. Dynamic provable data possession. In Proceedings of the 16th ACM conference on Computer and communications security, pages 213–222. ACM, 2009.
14. A. Fiat and M. Naor. Broadcast Encryption, Advances in CryptologyCrypto93. Lecture Notes in Computer Science, 773:480–491, 1994.
15. A. Fiat and M. Naor. Broadcast Encryption, Advances in CryptologyCrypto93. Lecture Notes in Computer Science, 773:480–491, 1994.
AUTHORSPROFILE
Dr.Akundi Sai Hanuman, Professor of Computer Science and Engineering, completed his Ph.D. from Acharya Nagarjuna University, Guntur in 2012. He has over 22 years of experience in Academic, Industry and Research. Dr. Akundi Sai Hanumans Research interests include Data Clustering, Data Sciences, Machine Learning, OptimizationTechniques and Distributed Systems. Currently Dr.Sai Hanuman is acting as Dean of Academics in GRIET.
Dr.P.S.V.Srinivasa Rao , Working as a Professor, Department of Computer Science and Engineering in Vignan’s Institute of Management & Technology for Women. He has about 30 years of Teaching experience in reputed engineering colleges in Telangana & Andhra Pradesh. He has published about 40 research papers in International Journals and Conferences. His research interests are Image Processing, Data Mining and Cloud Computing.
Dr. J. Sasi Kiran ,B.Tech from JNTUH, M.Tech from Bharath University and received Ph.D degree in Computer Science from University of Mysore. He is working as Principal & Professor in CSE in Farah Institute of Technology, Chevella, Telangana ,India. His research interests include Image Processing, Cloud Computing and Network Security. He has published research papers till now in Conferences, Proceedings and Journals
G.Charles Babu , Presently working as a Professor in Dept. of CSE in Malla Reddy Engineering College(Autonomous) – Main Campus , Secunderabad, Telangana Since 5 Years and Total Teaching experience of 20 Years. Completed B.Tech (CSE) in 1997 from KLCE, M.Tech(SE) in 1999 from JNTUH and Ph.D(Data Mining) from ANU. Published more than 50 Research Papers in Data Mining, Cloud Computing