International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 3, Issue 5, May 2013)
536
Recursive Information Hiding in Threshold Visual
Cryptography Scheme
Lekhika chettri
1, Sandeep Gurung
2M-tech Student, Associate Professor
Department of Computer Science & Engg., Sikkim Manipal Institute of Technology, India
Abstract-- This paper attempts to explain hiding of secret information recursively in threshold visual cryptography scheme for black and white image. The threshold visual cryptography scheme used is based on three per one pixel expansion for (2, 3) visual cryptography scheme. In this paper we propose a new way to hide n number of secrets recursively in the original image, to explain this we hide four secrets recursively irrespective of the size of the secret messages to be hidden. At each level a new secret is hidden into the previously generated share. Decoding of the recursively hidden shares can be done by first extracting the secret share image at each recursive level. There is no image size restriction and so there is no limitation to numbers of image that can be hided into the original image shares.
Keywords-- Secret message, shares, extraction, threshold, hidden message, constructed image.
I. INTRODUCTION
Visual Cryptography refers to a secret sharing method that will encrypt the secret message into a number of shares and does not require any computer or calculations for decrypting the secret image rather the secret message will be reconstructed visually by overlaying the encrypted shares the secret image will become clearly visible. Therefore it makes use of the HVS (Human Visual System) to decrypt the information thus making it advantageous for situations where we do not have complex machines to retrieve the final information. This Scheme was originally introduced by Naor and Shamir in the year 1994. Visual Cryptography encrypts written material (text, notes, pictures, etc.) in such a way that encrypted secret is totally secured [1]. The VCS generates shares of the secret image. The shares are a random collection of noise. The decoding can be done visually by overlaying all the defined or defined threshold number of shares. An expert cryptanalyst even cannot decode the secret with lesser than the threshold values of shares.
Threshold Visual cryptography scheme also called as “k out of n” allows secret enhancement with lesser than “n” number of shares. Decoding in “k out of n” VCS can be done by overlaying the “n” number of shares. Lesser than “n” number of shares reveals no information [2].
II. (2,3)THRESHOLD VISUAL CRYPTOGRAPHY SCHEME Threshold VCS allows a predefined numbers of shares to decode the secret. Stacking any k numbers of shares out of n numbers can construct the encoded message but k-1 number of shares discloses no information. The (2, 3) threshold VCS decrypts a secret message into three shares and to construct the secret message any combination of two shares is to be overlaid. It is based on the basic VC model as introduced by Athi and Shamir adding the threshold value factor. For a (2, 3) threshold VCS with m=3 (m = number of sub pixels) the white and black pixel to its sub-pixels combinations relation can be shown as below [3].
We construct here black sub pixel on 1/3 basis i.e. one out of three black sub pixel is black which in (2, 3) VCS gives 2 black pixel and one white sub pixel for a black pixel in the original image giving a 2/3 valued black pixel in the share combination. To get a complete black pixel in the share combination process we can even form a 2/3 black sub pixel for one share and the same for other two shares. Same is done for white pixel.
The important parameters that govern the idea are
Pixel expansion: This criteria indirectly affects the contrast and the aspect ratio of the final overlaid image. Pixel expansions of 2 by 2 are normally used to preserve the aspect ratio.
International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 3, Issue 5, May 2013)
537
Fig1: Black pixel combination
In general there are m! Permutation of {1, 2, ….,m} where m represents the number of pixels expanded to generate the shares. In case m=3 and therefore there are six permutations of {1, 2, 3}. The various permutations generated are as listed below:
α1= (1, 2, 3) α2= (1, 3, 2)
α3= (2, 1, 3) α4= (2, 3, 1)
α5= (3, 1, 2) α6= (3, 2, 1)
Examples of three shares generated for a black and white pixel are given in Fig1 and Fig 2.
Fig2: White pixel combination
To understand share combinations permutation let us assume Mo represents white pixel and M1 represents a black pixel. In 2 out of 3 scheme for m=3 we have,
M0= [1 0 0 ; 1 0 0 ; 1 0 0;] & M1= [1 0 0 ; 0 1 0 ; 0 0 1]
We can choose a random permutation of {1, 2, 3}. Suppose we want to encode a pixel valued 1 and we randomly select the fourth permutation. Then we have
α = α4 = {2, 3, 1}
Then we construct Np (new permuted pixel share combination) by taking column 2 of M1 and then column 3 of M1 and at last column 1 of M1. Thus we obtain,
M1= [0 0 1; 1 0 0; 0 1 0]
Thus the pixel P will be encoded as below and the same is followed for the pixel valued 0.
From below combination we can see that the stacking of all the three shares gives a complete black pixel and stacking of any two shares results in a dark grey image.
A.Encryption pixel algorithm
1. START
2. For input = 0 or 1;
3. Choose a random permutation α of (1, 2, …m), 4. Construct Np by permuting the columns of Mp
using the permutation α,
5. For 1<= i <=n, take row i of Np to be m sub-pixels of P on the share
6. Repeat step 2 to 5 until end of pixel 7. STOP
B.Decryption pixel algorithm
1. START
2. Stack defined number of shares i.e. „k‟
International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 3, Issue 5, May 2013)
538 III. RECURSIVE INFORAMTION HIDING
Recursive information hiding allows us to hide several information in the shares of the original secret message. It increases the efficiency and usability of the basic visual cryptography scheme. Unlike basic VCS which encrypts only one information in its generated shares with recursive information hiding we can add and hide more than one information to Visual Cryptogrpahy shares. Thus adding recursive information hiding techniques to novel VC method enables increase the use and efficiency of the novel VC approach.
The secret image that are to be hidden are taken in increase in size. All the additional secret messages is hide to the one of the shares of the original image. The smallest secret image is encrypted into two random collection of shares. These shares are placed below or beside each another (concatenated), and they now are taken to constitute the first share of the secret image. The second share is obtained in such a manner that if the two shares are overlaid, the secret under consideration is disclosed. The additional message to be hidden is in the multiple of two with respect to size of the original secret message. For example if the size of the original image is 4 x 4 than the first secret image size is 2 x 2 and that of the second secret image is 4 x 2. The share of the original image contains all the shares of the last hidden image [4]. Share1 of the original image holds all the secret image shares i.e. in case share1 is in false hand the smaller secret message can be easily broken.
The first small secret image is divided into different shares. These shares are placed in the next level to create the shares of larger secret information. The original secret image under consideration is of size 5 × 5 and the first secret image is of size 1 × 1. There are totally five shares obtained for the first secret image based on the basic idea of visual cryptography. The second secret image is of size 5 × 1. To obtain the second secret image the shares of first secret image are placed in different levels (level 1-5) one after the other in five different shares. Now the shares of second secret image are designed by seeing the shares of first secret image and the original second secret image. The share 1 of the first secret image is placed on share 1 of the second secret image (level 1).
This process is recursively repeated for all the shares. By doing this the information of original second secret image is obtained by combining any 3 shares. This is then processed for the shares of the original image in the same way [5]. The secret images should be smaller in size as compare to the original image, this restricts the number of secrets messages to be hidden and also the transparency alignment to obtain the second and first secret image is to be perfectly known otherwise some pixel information may lose.
IV. PROPOSED METHOD
In this paper we we modelled a new method to perform recursion. The basic method is same as the novel recursive method accepted in [4] but the algorithm is differently featured.If in case we have four secrets in total to hide then the shares of the 3rd secret message are hidden in the fourth secret message irrespective of the secret message size, and now the combined secret message shares generated from this level further hides the shares of the second level secret message and now this shares with the hidden shares of the 3rd and 4th secret message is hide in the shares of the original secret message i.e. in combine we have only n number of shares of that of original message at the last level. The encryption flow is shown below in Fig 3. This paper enables hiding of n number of secret message shares in the original message shares irrespective of the size of the secret message. Bit shifting method is used to hide the shares of the secret message in another share message.
Its clears the first shares last two LSB bits
Then move the second shares MSB bits to the LSB bits.
It then clears the second image's MSB and inserts the second to first file.
International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 3, Issue 5, May 2013)
[image:4.612.52.300.115.451.2]539
FIG 4: Block Diagram of the Encryption Process Recursive Encryption Algorithm
1. START
2. Perform threshold VCS to original image and to all the „n‟ numbers of secrets ,
3. Generate shares of the original image, 4. Generate shares of all the secret shares,
5. Hide shares1 of n secret image to the share1 of n-1 secret image,
6. pest step 5 for all the other shares 7. If step 5 & step 6 completed, then
a. Hide the combined shares generated after step 5 & step 6 to n-2 secret image,
8.
Perform step 7.1
9. epeat step 5 to step 7 for all n, UNTILL a. shares of original image reached
10.STOP
A.Recursive Decryption Algorithm
1. Start
2. Extract shares from original image,
3. further extract shares from the shares from step 2 4. repeat step 3 untill n==1,
5. STOP
Fig 5 summarises the generation of the shares using the above mentioned algorithm.
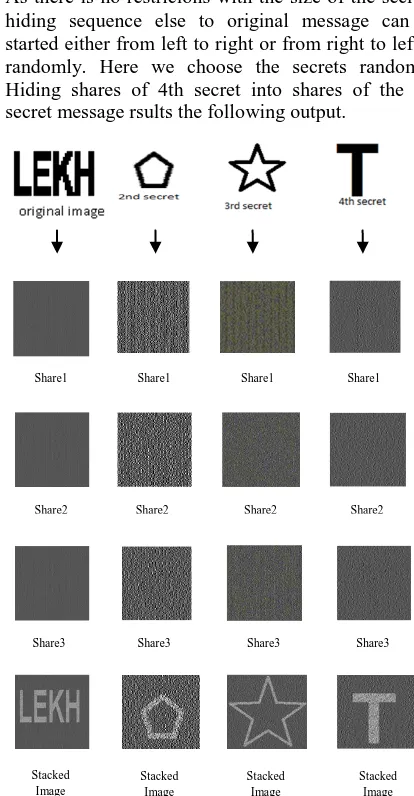
III. EXPERIMENTAL RESULTS A.Steps: Encoding Sequence
1. Generating and storing all the three shares of all the four original and secret messages
.
[image:4.612.343.550.294.692.2]2. As there is no restricions with the size of the secrets, hiding sequence else to original message can be started either from left to right or from right to left or randomly. Here we choose the secrets randomly. Hiding shares of 4th secret into shares of the 3rd secret message rsults the following output.
FIG 5: Generation of shares of Secret messages using Recursive (2, 3) VCS
Share1 Share1
1
Share1
1
Share2
1
Share1
1
Share2
1
Share2
1
Share2
1
Share3
1
Share3
1
Share3
1
Share3
1
Stacked Image
1
Stacked Image
1
Stacked Image
1
Stacked Image
1
ORIGINALIMAGE
FIRST SECRET IMAGE
SECOND SECRET IMAGE
THIRD SECRET IMAGE
FOURTH SECRET IMAGE
International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 3, Issue 5, May 2013)
540 B.Hiding 2nd secret into 4th
2.2. Hiding of shares generated in Fig 6 in the third secret
2.2 Hiding of shares generated in Fig 7 to the original message shares
This completes the encryption process yeilding only three shares for the total tweleve shares.
A.Steps: Decoding
Once the encryption process is over the extraction of the shares is obtained by backtracking the steps followed while encryption i.e. passing Share1 from Fig 8 to the decoder which gives two shares hidden in the Share1 from Fig 8. Save the images and further pass the share with hidden images to the decoder and it gives the hidden images and process once more and the final share will be decoded.
For example:
Taking Share1 as an input from Fig 8 to the decoder will generate two shares i.e. share1 from Fig1 itself and the hidden share1 from Fig 7 (share1 from Fig 7 further needs to be extracted as it hides more information in it).
Now pass the share generated from above to the decoder and it will give Share1 from Fig 7 itself and the hidden share in it i.e. Share1 from Fig 6.
This way all the shares of share1 for all the secret messages and the original message is generated. And the same is processed for the final shares2 and Share 3 from Fig 8.
Now combine any two shares out of the three shares to its respective shares and the information is revealed.
The stacked image after completion of extraction of all the images looks like the stacked images from Fig 5.
V. CONCLUSION
As this recursion technique does not imposes one secret image necceserily to be smaller in size than that of the former secret images, we can conclude that this technique of recursive information hiding using Visual Cryptography permits succesive numbers of information hiding. The additional secrets to be hidden could be of any size
VI. FUTURE SCOPE
The same recursive method proposed here can also be extended to any number of images with any size either for (k,n) or (k,k) visual ryptography scheme. It can further be extended to color images.
REFERENCES
[1] Naor, M., and Shamir, A. (1995), Visual cryptography, in „„Advances in Cryptogoly Eurocrypt ‟94‟‟ (A. De Santis, Ed.), Lecture Notes in Computer Science, Vol. 950, pp. 1 12, Springer-Verlag, Berlin.
[2] Chandramathi S., Ramesh Kumar R., Suresh R. and Harish S., “An overview of visual cryptography”, International Journal of Computational Intelligence Techniques, ISSN: 0976–0466 & E-ISSN: 0976–0474, Volume 1, Issue 1, 2010, PP-32-37
[3] Abhishek Parakh and Subhash Kak ,‟ A Recursive Threshold Visual Cryptography Scheme”, Oklahoma State University
[4] Gnanaguruparan, M. and Kak, S, “Recursive Hiding of Secrets in Visual Cryptography. Cryptologia”, 26: 68-76, . 2002.
[image:5.612.65.227.150.239.2]Share1 Share2 Share3
FIG 8: 3rd level of encryption
Share3 Share2
[image:5.612.70.225.295.360.2]Share1
[image:5.612.87.251.435.512.2]FIG 7: 2nd level of encryption FIG 6: 1st level of encryption
Share1
1
Share2
1
Share3