Available online:
https://edupediapublications.org/journals/index.php/IJR/
P a g e | 1762
Location Privacy Using Dynamic Grid Systems on
Location-Based Services
vemulapalli Venkataramana
M-Tech, Dept. of CSE, JNTU, Hyderabad,
Mail Id: - vvramana25@gmail.com
Abstract
Area predicated housing (LBS) expect
clients to interminably report their area to a
possibly untrusted server to acquire
facilities predicated on their area, which
can open them to security risks.
Infelicitously, subsisting security protecting
systems for LBS have a few restraints, for
example, requiring a planarity-trusted
outsider, offering hindered security
certifications and bringing about high
correspondence overhead. In this paper, we
propose an utilizer-characterized security
network framework called dynamic matrix
framework (DGS); the main all
encompassing framework that fulfills four
basic essentials for protection saving
preview and never-ending LBS. (1) The
framework just requires a semi-trusted
outsider, in charge of completing basic
coordinating operations effectively. This
semi-trusted outsider does not have any data
about a client's area. (2) Secure preview and
interminable area protection is guaranteed
under our characterized foe models. (3) The
correspondence cost for the utilizer does not
rely upon the client's coveted security level;
it just relies upon the quantity of pertinent
purposes of enthusiasm for the region of the
utilizer. (4) Albeit we just focus on range
and k-most proximate-neighbor questions in
this work, our framework can be effortlessly
lengthened to invigorate other spatial
inquiries without transmuting the
calculations keep running by the
semi-confided in outsider and the database
server, gave the required hunt region of a
spatial inquiry can be dreamy into spatial
locales. Trial comes about demonstrate that
our DGS is more productive than the best in
class protection saving system for
interminable LBS.
Key words: - Dynamic grid systems,
location privacy, location-based services,
spatio-temporal query processing,
cryptography
INTRODUCTION
In this day and age of versatility and
Available online:
https://edupediapublications.org/journals/index.php/IJR/
P a g e | 1763
number of individuals utilize area predicated
facilities (LBS) to ask for data relevant to
their present areas from an assortment of
settlement suppliers. This can be the look for
close-by purposes of intrigue (POIs) (e.g.,
eateries and lodgings), area cautious
promoting by organizations, movement data
custom-made to the thruway and course an
utilizer is peregrinating et cetera. The use of
LBS, in any case, can uncover considerably
more about a man to conceivably deceitful
settlement suppliers than many individuals
would be arranged to reveal. By following
the solicitations of a man it is conceivable to
assemble a kineticism profile which can
uncover data about a client's work (office
area), restorative records (visit to authority
centers), political perspectives (going to
political occasions), and so forth. By the by,
LBS can be extremely important and in that
capacity clients ought to have the capacity to
make use of them without giving up their
area security. Various methodologies have
as of late been proposed for safeguarding the
utilizer area security in LBS. When all is
said in done, these methodologies can be
consigned into two fundamental
classifications. (1) Plenarily-trusted outsider
(TTP). The most famous security
safeguarding procedures require a TTP to be
put between the utilizer and the convenience
supplier to obnubilate the client's area data
from the settlement supplier (e.g., [1]–[8]).
The principle undertaking of the outsider is
monitoring the correct area of all clients and
obscuring a questioning client's area into a
shrouded territory that incorporates k − 1
different clients to accomplish
k-namelessness. This TTP show has three
disadvantages. (an) All clients need to
never-endingly report their correct area to
the outsider, yet they don't subscribe to any
LBS. (b) As the outsider kens the correct
area of each utilizer, it turns into a charming
focus for attackers. (c) The k-obscurity
predicated strategies just accomplish low
provincial area security in light of the fact
that shrouding a locale to incorporate k
clients practically speaking generally brings
about humble shrouding territories. (2)
Private data recovery (PIR) or neglectful
exchange (OT). But PIR or OT strategies
don't require an outsider, they bring about a
considerably higher correspondence
overhead between the utilizer and the
convenience supplier, requiring the
transmission of significantly more data than
the utilizer truly needs (e.g., [9]–[10]). Just a
couple of security protecting strategies have
Available online:
https://edupediapublications.org/journals/index.php/IJR/
P a g e | 1764
These procedures depend on a TTP to
ceaselessly extend a shrouded range to
incorporate the at first doled out k clients.
These methods not just acquire the
downsides of the TTP demonstrate, however
they withal have different circumscriptions.
(1) Inefficiency. Unendingly growing
shrouded ranges considerably expands the
inquiry handling overhead. (2) Privacy
spillage. Since the database server gets an
arrangement of back to back shrouded
regions of an utilizer at various timestamps,
the relationship among the shrouded regions
would give backup data to surmising the
client's area. (3) Accommodation end. An
utilizer needs to end the convenience when
clients at first allocated to her shrouded
range leave the framework.
2. RELEGATED WORK 2.1Existing System
Spatial shrouding systems have been
generally used to save utilizer area security
in LBS. [3]The majority of the subsisting
spatial shrouding procedures depend on a
plenarily-trusted outsider (TTP), expectedly
named area anonymizer that is required
between the utilizer and the settlement
supplier. When an utilizer subscribes to
LBS, the area anonymizer [4]will obscure
the client's correct area into a shrouded zone
to such an extent that the shrouded range
incorporates in any event k – 1 different
clients to slake k-namelessness. In a
framework with such local area protection it
is strenuous for the utilizer to assign
customized security imperatives. The
inclination predicated approach reduces this
issue by finding a shrouded range predicated
on the quantity of its guests that is in any
event as prominent as the client's assigned
open district. Though some spatial timing
strategies can be connected to shared
situations, these procedures still depend on
the k-obscurity protection imperative and
can just accomplish provincial area security.
Furthermore, these systems expect clients to
believe each other, as they need to uncover
their areas to different companions and
depend on other associates' areas to obscure
their areas, another disseminated strategy
was suggested that does not expect clients to
believe each other, [5]but rather despite
everything it utilizes numerous TTPs.
Another group of calculations utilizes
incremental most proximate neighbor
inquiries, where an inquiry begins at a "stay"
area which is not quite the same as the real
area of an utilizer and iteratively recovers
more purposes of enthusiasm until the point
Available online:
https://edupediapublications.org/journals/index.php/IJR/
P a g e | 1765
require a trusted outsider, the rough area of
an utilizer can even now be found out;
henceforth just local area security is
accomplished.
2.2 Proposed System
In this paper, we propose an
utilizer-characterized protection lattice framework
called dynamic matrix framework (DGS) to
give security safeguarding preview and
never-ending LBS. The principle origination
is to put a semi trusted outsider, named
question server (QS), between the utilizer
and the settlement supplier (SP). [6]QS just
should be semi-trusted on the grounds that it
won't collect/store or even approach any
utilizer area data. Semi-trusted in this setting
assigns that while QS will attempt to decide
the area of an utilizer, it still accurately
completes the straightforward coordinating
operations required in the convention, i.e., it
doesn't alter or drop messages or cause
nascent messages. An untrusted QS would
discretionarily change and drop messages
and also infuse fake messages, which is the
reason our framework relies upon a
semi-confided in QS. The primary origination of
our DGS. In DGS, a questioning utilizer
initially decides an inquiry territory, where
the utilizer is agreeable to uncover the way
that she is some place inside this question
region. The inquiry region is isolated into
rise to measured framework cells predicated
on the dynamic network structure assigned
by the utilizer. At that point, the utilizer
encodes an inquiry that incorporates the data
of the question range and the dynamic lattice
structure, and scrambles the character of
every network cell converging the required
pursuit territory of the spatial inquiry to
incite an arrangement of scrambled
identifiers. Next, the utilizer sends a demand
including (1) the encoded inquiry and (2) the
scrambled identifiers to QS, which is a
semi-trusted gathering situated between the
utilizer and SP. QS stores the scrambled
identifiers and advances he encoded
question to SP assigned by the utilizer. SP
unscrambles the question and winnows the
POIs inside the inquiry region from its
database.
Available online:
https://edupediapublications.org/journals/index.php/IJR/
P a g e | 1766
Fig 1 Architecture Diagram 3.1 Utilizer Enrollment Module
Enlistment Module In the enlistment module
is auxiliary for the early utilizer to enroll
themselves by giving their substantial points
of interest, for example, email id, utilizer
assignment, Phone number, and so forth.
The utilizer needs to fill every one of the
points of interest else message is shown to
the utilizer. When every one of the fields are
filled the utilizer clicks Register catch,
which presents the information to the
database. Here it checks the utilizer table,
regardless of whether the subtle elements to
the utilizer table. On the off chance that all
subtle elements are veridical the clients see
the fundamental page. After consummate the
enrollment procedure, utilizer validate to the
framework.
3.2 Pursuit Query Module
In this module the utilizer looks through the
question. A questioning utilizer initially
decides an inquiry zone, where the utilizer is
agreeable to uncover the way that she is
some place inside this question region. The
inquiry zone is partitioned into framework
cell predicated on the dynamic network
structure assigned by the utilizer.
3.3 Inquiry Server
Inquiry Server Module QS is a semi-trusted
gathering put between the versatile utilizer
and SP. The portable utilizer sends a
demand that incorporates the character of an
utilizer-assigned SP, a scrambled question
(which incorporates data about the
utilizer-characterized dynamic framework structure),
and an arrangement of encoded identifiers
(which are figured predicated on the
utilizer-characterized dynamic network structure) to
QS. QS Store the encoded identifiers and
advances the scrambled inquiry to the
utilizer-assigned SP. SP decodes the
question and finds a consistent arrangement
of POIs from its database. It at that point
scrambles the POIs and their comparing
identifiers predicated on the dynamic lattice
structure assigned by the utilizer and sends
them to QS. QS Returns to the utilizer each
encoded POI whose scrambled identifier
matches one of the scrambled identifiers at
first sent by the utilizer.
3.4 Settlement Provider
Area predicated settlement suppliers assume
the part of spatial information maintainers
and spatial inquiry processors in our
framework. So as to deal with security
bulwarked spatial inquiries, area predicated
convenience suppliers actualize protection
forfended inquiry processors in their
databases. convenience supplier is a spatial
Available online:
https://edupediapublications.org/journals/index.php/IJR/
P a g e | 1767
stores the area data of a specific kind of
static POIs, e.g., eateries or lodgings, or the
store area data of a specific organization,
e.g., Starbucks or McDonald's. SP does not
speak with portable clients
straightforwardly, but rather it gives housing
to them in a roundabout way through the
inquiry server (QS)
Algorithm for DGS
Input: User location (x, y), POI data P Output: User's POI Query data U(P). Initialization:
i. User Select POI Type P(t), QS Query
Server, SP Service Provider.
ii. User set location, defined x, y (Current
exact Location).
let xu,yu ∈ U,
Map.getBounds(xu,yu)
return( xb,yb ), ( xt,yt ) where
b- bottom, t- top
Key Derivation Function KDF()
returns k (random key)
Enc(query) = IBE(P(t), k, ( xb,yb ), ( xt,yt ))
// At User side
Enc(query), User data of U fwd to QS.
Create ID for Query and fwd
Enc(query) to SP
Decrpt(query) at SP,
get (xc,yc)= Map.getCenter(( xb,yb
), ( xt,yt ));
while data != nulll
get POI P ∈ P(t),
sort based on dist,
create Query Set U(p).
end while
return Query Set U(p) to QS
At QS, fwd Query Set to User
Decrpt(query set U(P)) at USer,
4. EXPERIMENTAL RESULTS
Fig 2 Add POI (points of interest)
Available online:
https://edupediapublications.org/journals/index.php/IJR/
P a g e | 1768
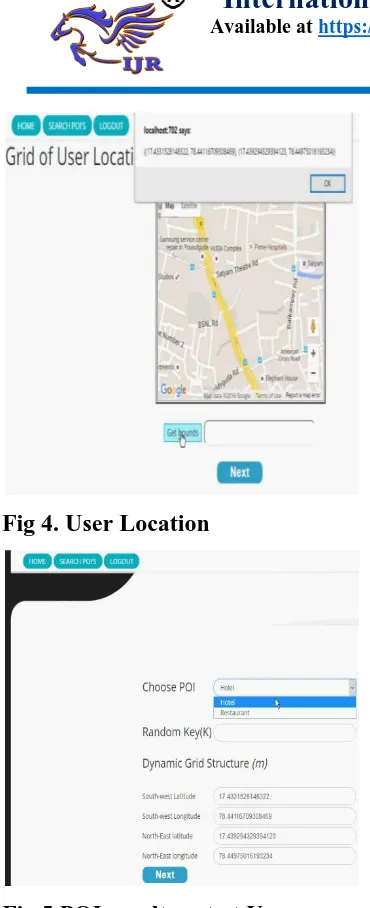
Fig 4. User Location
Fig 5 POI results got at User
5. CONCLUSION
In this paper, we proposed a dynamic lattice
framework (DGS) for giving protection
saving never-ending LBS. Our DGS
incorporates the question server (QS) and
the convenience supplier (SP), and
cryptographic capacities to isolate the entire
inquiry handling errand into two segments
that are performed discretely by QS and SP.
DGS does not require any plenarily-trusted
outsider (TTP); rather, we require just the
significantly more impuissant set of no
conspiracy amongst QS and SP. This
divergence furthermore moves the
information exchange stack far from the
utilizer to the cheap and high-data transfer
capacity connect amongst QS and SP. We
also planned proficient conventions for our
DGS to strengthen both never-ending
k-most proximate-neighbor (NN) and range
questions. To assess the execution of DGS,
we contrast it with the cutting edge
procedure requiring a TTP. DGS gives
preferable protection ensures over the TTP
conspire, and the test comes about
demonstrate that DGS is a request of
greatness more productive than the TTP
plot, as far as correspondence cost. As far as
calculation cost, DGS withal dependably
outflanks the TTP plot for NN inquiries; it is
commensurable or barely more indulgent
than the TTP conspire for extend questions.
6. REFERENCE
[1] B. Bamba, L. Liu, P. Pesti, and T.Wang,
“Supporting anonymous location queries in mobile environments with PrivacyGrid,” in
WWW, 2008.
[2] C.-Y. Chow and M. F. Mokbel,
Available online:
https://edupediapublications.org/journals/index.php/IJR/
P a g e | 1769
[3] B. Gedik and L. Liu, “Protecting location
privacy with personalized kanonymity:
Architecture and algorithms,” IEEE TMC,
vol. 7, no. 1, pp. 1–18, 2008.
[4] M. Gruteser and D. Grunwald,
“Anonymous Usage of Location-Based
Services Through Spatial and Temporal
Cloaking,” in ACM MobiSys, 2003.
[5] P. Kalnis, G. Ghinita, K. Mouratidis, and
D. Papadias, “Preventing location-based
identity inference in anonymous spatial
queries,” IEEE TKDE, vol. 19, no. 12, pp.
1719–1733, 2007.
[6] M. F. Mokbel, C.-Y. Chow, and W. G.
Aref, “The new casper: Query processing
for location services without compromising
privacy,” in VLDB, 2006.
[7] T. Xu and Y. Cai, “Location anonymity
in continuous location-based services,” in
ACM GIS, 2007.
[8] “Exploring historical location data for
anonymity preservation in location-based
services,” in IEEE INFOCOM, 2008.
[9] G. Ghinita, P. Kalnis, A. Khoshgozaran,
C. Shahabi, and K.-L. Tan, “Private queries
in location based services: Anonymizers are
not necessary,” in ACM SIGMOD, 2008.
[10] M. Kohlweiss, S. Faust, L. Fritsch, B.
Gedrojc, and B. Preneel, “Efficient oblivious
augmented maps: Location-based services