SCEAMS: Secure Corporate Environment Adhered to
Mobile & Smartphones
David Samuel Bhatti
School of Electrical Engineering and Computer Sciences, National University
of Science & Technology, Islamabad, Pakistan
david.bhatti@seecs.edu.pk
Nazar Abbas Saqib
College of Electrical and Mechanical Engineering, National University of
Science & Technology, Islamabad, Pakistan
nazar.abbas@ceme.nust.edu.pk
Zahid Anwar
School of Electrical Engineering and Computer Sciences, National University
of Science & Technology, Islamabad, Pakistan
zahid.anwar@seecs.edu.pk
Abstract- Due to increased use of smartphones in enterprise setup several security threats have also been penetrated in it. Threats and risks become increased, especially when these smartphones get connected to enterprise network via GSM, GPRS, Bluetooth or Wi-Fi. Security researchers are also working on offering best security solutions against these threats and attacks. This area is less explored yet; that is why, we have carried out a survey to explore the latest, in-practice, state-of-the-art security policies, standards, solution and mechanisms for corporate environments. Study will help secure personal as well as enterprise information and applications on smartphones against latest threats and risks. Keywords- Smartphone; Malware; IDS; Android; iPhone; Apple; Symbian; Wi-Fi,
I.INTRODUCTION
Smartphone is basically a mobile-phone with advanced capabilities of computing, connectivity and storage. Latest advanced smartphones are enriched with GPS, Wi-Fi, Bluetooth, medial players, web browsers, Skype etc. These advanced smartphones are providing the user with all features a PC provides. Now, they have become indispensable part of our personal and official life [1] [2]. Michael Overlay in his report [3], addresses the information security in business-partner and vendor relationship. In his report, he suggests businessmen to appreciate certain common threads between information privacy and information security laws, through which the business run. The reader can go through these common threads given in his report. He suggests the integration of these common threads with the BYOD model (Bring Your Own Device) [4], and apply in real business scenarios to create new dimensions of secure business.
There are thousands of App developers, who are developing malicious Apps. These Apps seem benign, but contain malicious intentions for smartphone having sensitive corporate data and business Apps. If these issues are not addressed properly, users would have to pay a heavy price in terms of privacy loss, Id theft, money, denial of service etc. [5]. For example, through Bluetooth attacks like blueJacking, blueSnarfing and blueBugging can be launched [6]. Smartphones are out of IT control, cause data leakage and data loss in corporate environment, allure attackers for attack and proved to be overconsumption of bandwidth too [7]. The security of corporate network and smartphones itself becomes critical, because they are the end-points of corporate and GSM
network; connected to the corporate network through Wi-Fi and can bypass the corporate network security policies. Bruce Snell have reported 37 million out of 150 million mobile devices to be infected over the period of six month malware analysis [8]. Aim of this study is to unveil smartphone security threats, vulnerabilities, attacks and unleashing state of the art security solution and mechanism implemented in the form of software or hardware. The enterprises can use this research survey to identify their security threats and can deploy suitable security policies and solutions for their corporate environment. We hope, this survey will equally effective for the general smartphone-users as well to make their phones secure. Rest of the paper has been organized as ii-threats and attacks, iii-related work, ismartphone security survey, v-corporate security products, vi-BYOD model, vii-security products comparison, viii-conclusion and ix-future work.
II. THREATS & ATTACKS
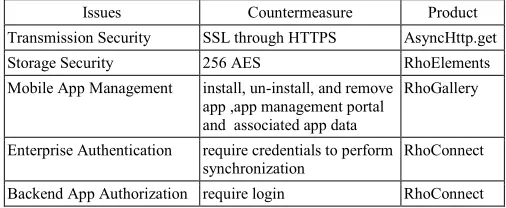
We believe that awareness of different security threats and vulnerabilities of smartphone in an enterprise environment will help in effective implementation of security solutions. Some of the vulnerabilities identified in [1] are system defects, insufficient API management, unawareness of users about smartphone terminologies and use of unsecure wireless channels etc. Usually, the attackers to compromise smartphones exploit these vulnerabilities. The reader is advised to study the work of Ashwini et al. [9] for getting in depth technical understanding of the attacks, their detection and prevention mechanisms. Authors of [10] identified smartphone security issues in an enterprise environment and gave respective counter measures, technical solutions given in table 1.
TABLE 1. SECURING SMARTPHONES IN MOBILE ENTERPRISE
Issues Countermeasure Product
Transmission Security SSL through HTTPS AsyncHttp.get
Storage Security 256 AES RhoElements
Mobile App Management install, un-install, and remove app ,app management portal and associated app data
RhoGallery
Enterprise Authentication require credentials to perform synchronization
RhoConnect
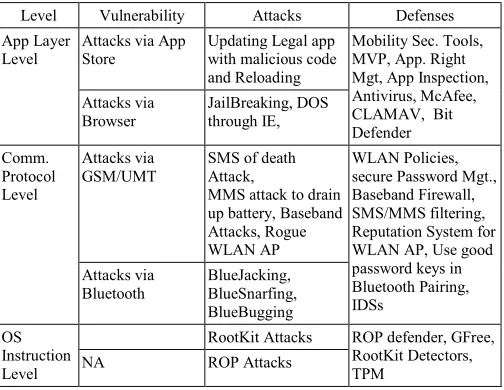
Westoff and Rajasekaran [5] discussed vulnerabilities at application level, at communication protocols level and at operating system instruction level. How these can be exploited to launch different attacks have also been brought into consideration by them. Awareness of these vulnerabilities helps enterprise to fix them effectively by using state of the art security products. A summary of these vulnerabilities, attacks, and defenses have been given in table 2.
TABLE 2. EFFECT OF COMPROMISED SMARTPHONE ON GSM
Level Vulnerability Attacks Defenses
App Layer Level
Attacks via App Store
Updating Legal app with malicious code and Reloading
Mobility Sec. Tools, MVP, App. Right Mgt, App Inspection, Antivirus, McAfee, CLAMAV, Bit Defender Attacks via
Browser JailBreaking, DOS through IE,
Comm. Protocol Level
Attacks via GSM/UMT
SMS of death Attack,
MMS attack to drain up battery, Baseband Attacks, Rogue WLAN AP
WLAN Policies, secure Password Mgt., Baseband Firewall, SMS/MMS filtering, Reputation System for WLAN AP, Use good password keys in Bluetooth Pairing, IDSs
Attacks via Bluetooth
BlueJacking, BlueSnarfing, BlueBugging OS
Instruction Level
RootKit Attacks ROP defender, GFree, RootKit Detectors, TPM
NA ROP Attacks
Work of Helen and Wenwu [11] describes how smartphones can be compromised and how these compromised smartphones can attack enterprise telecommunication business networks. This research study help telecom network to implement defense system against these compromised smartphones. Consequently, this will increase the reputation and business of not only the telecom network but also the general enterprises. Smartphones can be compromised from the internet during synchronization [12] that is transferring data from one device to another device. Smartphones can be infected in WPAN such as Bluetooth. Different attacks on telecommunication network because of compromised smartphones have been identified in [11] are DoS attack on BTS, attack on GPRS, DDoS attack on Call Centers, ID theft, Spoofing, and Remote wiretapping. The defense mechanisms proposed in this paper are smartphone hardening, internet side protection and telecommunication side protection. Smartphone hardening can be achieved by turning off PC part of the smartphone until not instructed; enabling the feature of callee’s number on LCD; combining STK with TCG’s TPMS module. Internet side protection can be obtained by forcing smartphones at BTS layer to be equipped with required patches. Telecommunication side can be protected by analyzing the abnormalities in the CallBlockingRate at BTS or Switch, by analyzing the call center load information and by analyzing the abnormal behavior of the end user. Furthermore, attack surface can be reduced, if telecommunication networks and internet exchanges have the knowledge of vulnerabilities and threats [11]. Attacks similar to [11] have also been identified by Mariantonietta et al. [13] along with state of the art security
products which will be discussed section V. Vulnerabilities like SYN-DOS attack, ARP spoofing, IP-Options attack in the network-stack of smartphone operating systems particularly Symbian and Windows Mobile have been detected by in [14] also.
III.RELATED WORK
Jiawen et al. [15] have carried out a very comprehensive study on memory attacks in smartphones. They have recommended storing sensitive information using the technology named SoC (System on Chip) instead of DRAM. For sensitive data protection, authors in this paper have given the idea of encrypted RAM and on chip AES schemes. Operating systems vulnerabilities have also been detected by Sang-Yong Choi and Jae-Kyung Park [16] in Android, where the protection guidelines are given by Ashwini et al. [9].
Survey by Mariantonieta et al. [13] addresses well known security threats, vulnerabilities and security solutions practiced from 2004-2011. Authors grouped mobile malwares into different categories viruses, worms, trojans, RootKits and botnets. Additional attack identified by them is break-in attack, where the attacker exploits the programming flaws e.g. buffer over flow to launch attack. The authors also propose counter measures against these malwares with respect to users, software developers, network operators and phone manufactures. They have enlisted state of the art mobile malwares, their adverse effects and latest security solutions and their features and supporting platforms.
Westoff and Rajasekaran in their research [5] describes the different attacks in vector form. They have categorized attack vectors into three classes, attacks via application layer, communication layer and via operating system layer. Authors discuss that how these layers can be exploited to launch different type of attacks on smartphone. Countermeasures discussed in this paper are App right management, virtualizations and system level safeguard, baseband firewall, ROP detection, implemented on the smartphone. App inspection and CFI (Control Flow Integrity) enforcement and RootKit detection are the proposed countermeasures implemented in the big internet cloud environment. In the small internet cloud environment, counter measure such as cooperative antivirus/RootKit detection, reputation system for WLAN Access Points and Bluetooth protection have been suggested. A few state of the art security products are explored and mostly the general security solutions are suggested.
smartphones. Technical report [7] discusses smartphone impacts on the network security and proposes certain tools and techniques to ensure controlled access of these devices to the corporate network. This report does not discuss the smartphone security itself. This report proposes 10 practices, if exercised properly, can induce security in corporate network husbanded with smartphone. SSL, VPN, next generation firewall, unified threat management firewall(UTM) and WPA2 network security solutions have been proposed in this article. It recommends the use of SonicWallTM [17] [7] solutions for smartphone security.
Study of [18] explores different state of the art smartphone virus and discusses them as families. Popular malware categories revealed in this paper are worm families (Lasco, Commwarrior, iPhone ikee), Trojan viruses (FlexiSpy, RedBrowser, and Skulls), Windows CE and CardTrap viruses. Different threats explored in this paper are compromising availability, integrity, confidentiality, draining resources and compromising network. Different solutions proposed for Android system are IDS/IPS, firewalls, selective android permissions, application certification, automated code analysis, access control (SE Linux), login, data encryption, remote management, resource management, VPN etc. In this paper, exploration and choice of security products has been left on user part.
The research of [19] focuses on enhancing the Linux-based android devices. Authors describe Linux file security, android development environment and ScratchBox cross compilation toolkit. In this paper, anti-virus, firewalls, RootKit detectors, IDS and some other tools explored for are Busy-box, Bash, Strace, Open SSH and NMAP. Authors have also discussed the compatibility requirements and the professional usage of these tools. Security and privacy of Android based messaging application has been well analyzed in [20].
IV.SMARTPHONE SECURITY SURVEY
Smartphone security surveys in enterprise network have shown that most the employers are unaware of the security risks of smartphone induction in corporate network for business use or personal use. IBM survey report [21] shows that 48% of organizations rely on employees common sense for ensuring security, whereas, currently 70% of employees are accessing enterprise network on their personal smartphone device. More than 40% of employees access email through unsecured Wi-Fi, which is a serious issue because number of smartphone users accessing the corporate network increasing very rapidly. KASPERSKY survey report by Paul Robert [22] reveals that 46% of organizations support non-company issued employee smartphone. The organizations which follow BYOD (Bring Your Own Device) are about 86% according to [21] which is a good sign of standardization. Further, survey identifies chain relationship among smartphones, enterprise employees and threats. It shows that 38% of organization employee’s smartphones have no security software. 85% of organizations allow employees to connect to public Wi-Fi even while traveling. 69% of organizations are not interested in security software on their employee’s mobile phones. 33% of
organization do not use any secure connection (e.g. VPN) to get connect their employees to corporate network. 66% of organizations are providing smartphones to their employees. 68% of organizations are not giving any security training to their employees. Thus, there is a great need to make organization aware about the security risks and threats [23]. Thus, a security survey which helps enterprise to select suitable smartphone for their employee to use in an enterprise environment, has been studied by Alexios Mylonas et al. [24]. Survey results have proved that a developer with bachelor degree can develop a malware for Android within a half day, for BackBerry in one day, for Windows in 2 days. Whereas, with master degree, a weak he would take to develop a malware for iOS platform. Ernst & Young [25] identifies different corporate security features provided by blackberry, iPhone and Android and third part security solution support by these devices which has been summarized in table 3.
TABLE 3. CORPORATE SECURITY FEATURES [25]
Feature Black
berry
iPhone Android Window Mobile
Capability of Remote Wipe
Encrypted Backup Files
Code Signing
Type Safe Programming Partial
Sandboxing Partial Partial
Enterprise Policy Enhancement Partial Partial
Full Disk and Memory Encryption Partial
End to End Data Encryption Partial
Support Corporate Security Features 100 81.25 50 75
We have introduced fourth platform that is Window Mobile to broaden the study. Tendency to support third-party security tools by Window found to be 66% as shown in table 4.
TABLE 4. THIRD-PARTY SECURITY SOLUTION SUPPORT [25]
Product Black berry iPhone Android Window
Microsoft Exchange Server
Novell GroupWise
Tangoe
Mobile Iron
Air Watch
Lotus Domino
Lotus Notes Traveler
Trust Digital
Good Mail
Mobile Active Defense
Sybase Management Mobility
Black Berry Enterprise Server
Third-Party Security Tools
Support 66% 91% 91% 66%
From table 3 and table 4 corporates can decide a suitable smartphone device for their employees according to their technical, operational and financial feasibility meeting the security model too.
V. CORPORATE SECURITY PRODUCTS
art security guidelines recommended by NIST [26], Ernst & Young [25] and Patrick Sweeney [7]. Definitely, these help enhance the enterprise security line. The purpose of exploring these solutions is that any organization following the state of the art security guidelines could develop their enterprise security models for smartphones. Once they have developed their security model, they may deploy suitable smartphones security solution in their corporate or enterprise environment.
A. Samsung KNOXTM [27]
Samsung KNOXTM is Android based state of the art enterprise smartphones security solution which is fully compatible with Google ecosystem. Salient features of KNOXTM have been summarized below.
a)Platform Security: Provides “Secure Booting” through secure boot loader, which proceeds only if provided with secure singed binaries. Kernel security is achieved by dividing memory and CPU resources into secure and unsecure world; TIMA(TrustZone-based Integrity Measurement Architecture) runs in non-secure world which removes the vulnerability of Linux kernel compromising. Security Enhancement for Android is additional security layer over top of Linux, which minimizes the risks of tampering and bypassing application security mechanisms.
b)Application Security: It runs each application in its own container separating data within the container from outside the container. Data within the container is encrypted with strong
algorithm AES-256. KNOXTM is complied with
containerization. KNOXTM container provides an enterprise with enriched set of policies for authentication, data security, VPN, email application blacklisting, white-listing etc. ODE (On-Device Data Encryption) provides enterprise user to encrypt data on entire device using AES-256. Password is required to gain access to container. Encryption can be achieved locally through settings and remotely using Exchange ActiveSync or MDM (Mobile Device Management Module). Encryption key is derived from passphrase using PBKDF2. KNOXTM VPN is very powerful provides an enterprise with IPSec suit, Triple-DES(56/168 Bit), AES(128/256-bit), Multiple VPN connections, support for Cisco VPN gateway etc.
c)Mobile Device Management: MDM [28] meets all those requirements which an enterprise expect from smartphone security solution for enterprises. Reader is advised to study [27] to know what KNOX-MDM feature supports which enterprise security need. Enhanced features of MDM include compliance with US DoD (Department of Defense) security requirements, VPN and Wi-Fi provisioning, screen lock configurations, support for management via Active Directory/Group Policy Manager and support of Samsung KNOXTM container.
d) Theft Recovery: KNOXTM provides solution for theft recovery. Solutions install mobile agent on smartphone where the “Persistence Service” in firmware becomes active on user subscription for this service. On smartphone theft, “Theft Recovery Customer Centre” issues commands to mobile agent to activate tracking and monitoring. “Persistence Service” ensures the availability of mobile agent even the smartphone is
set to factory setting. Samsung KNOX for Govt. and high security use is also featured with Boot Attestation, Smartcard CAS support, certification and validation.
B. McAfee EMM [29]
McAfee Enterprise Mobility Management Platform is one of state of the art multiplatform smartphone solutions for enterprise environment. It ensures security of employee smartphone to corporate business network security. Salient features of McAfee EMM are listed below.
a)McAfee EMM Device Management: It provides over-the-air (OTA) for users and results in reduction of IT workload; supports real-time smartphone access and reports log information, information about the status of the smartphone and pending actions information etc.
b)McAfee EMM Audit and Compliance Service: It provides visualization of the mobile assets detect and block crook devices and reports compliance status.
c)McAfee EMM Device Agents: This component has enriched support for password, public key infrastructure, encryption, remote deletion, two factor authentications, VPN and Wi-Fi configuration. It prevents iOS from backing up data on Apple iCloud means user can turn data and voice roaming.
d)McAfee ePO Software Integration: It provides centralized visibility and control for displaying data in charts, tables and graphs on McAfee ePO dashboard.
C. SONICWall® [17][7]
annual threat report [30] gives complete description of major attacks till 2015 and state of the security solution to combat these attacks through 2016. Analysis tools for Android and iOS have been suggested by Lori Flyn and Will Klieber [31]. They have recommended using DroidScop, DroidFuzzer for Android, PiOS and Xavus for iOS platforms for static and dynamic data flows. They have also studied Android and iOS security issues pragmatically. Daniel Fisher et al. [32] classifies software security solutions into six classes which are device management, data protection, access management, network protection, threat management and all-in-one-solution. Their research better answers the question like what solutions are available for smartphones, what measures are there for threats and which security measure mitigate which threat.
VI.BYOD MODEL
BYOD [33] stands for Bring Your Own Device; a model used in corporate environment, education and financial sectors for smartphone security. This model offers devices cost reduction and employee satisfaction, but also incurs new security and management issues for corporate IT. Current challenges [4], security issues [34], privacy concerns of employee and employer [35] to BYOD have been addressed through virtualization, containerization, smartphone remote management, SSL, VPN, and BYOD in phases etc. Thomas Shumate in [35] have identified different security risks to BYOD and have suggested different mitigation techniques. Samsung KNOXTM [27] and BlackBerry [36] supports BYOD model. We suggest the reader to read NIST guidelines [37] for BYOD security also.
VII. COMPARATIVE ANALYSIS
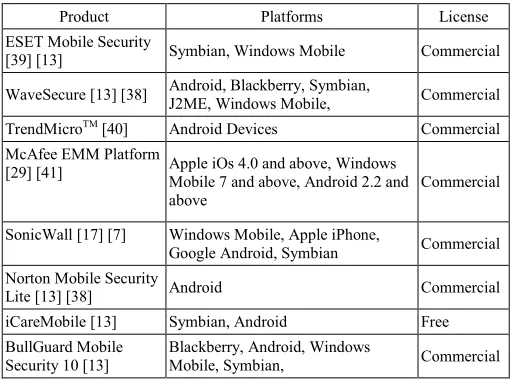
The comparison of different smartphone security solution for enterprises, has been given in this section, which will help an enterprise to select suitable security solution in easier way. Table 5 gives an over view of these solutions based upon the platforms and license. There are other worth seen tools enlisted in [38] which the enterprise can consider also. Features of these solutions can be seen from their respective references.
TABLE 5. SMARTPHONES SECURITY SOLUTION
Product Platforms License
ESET Mobile Security
[39] [13] Symbian, Windows Mobile Commercial
WaveSecure [13] [38] Android, Blackberry, Symbian, J2ME, Windows Mobile, Commercial
TrendMicroTM [40] Android Devices Commercial
McAfee EMM Platform
[29] [41] Apple iOs 4.0 and above, Windows Mobile 7 and above, Android 2.2 and above
Commercial
SonicWall [17] [7] Windows Mobile, Apple iPhone,
Google Android, Symbian Commercial
Norton Mobile Security
Lite [13] [38] Android Commercial
iCareMobile [13] Symbian, Android Free
BullGuard Mobile Security 10 [13]
Blackberry, Android, Windows
Mobile, Symbian, Commercial
Lookout Mobile
Security [13] [38] Android, iPhone Free
Kaspersky Mobile Security 8/9 [42] [13]
Android, Blackberry, Symbian,
Windows Mobile Commercial
VIII.CONCLUSION
Companies are offering their employees to stay connected with corporate business for continuous, seamless business functionality. Employees get access to enterprise network for performing business as well as personal operations, imposing high risks to business data integrity and network security. We have explored different threats and vulnerabilities, which can be exploited by attackers to cause heavy losses to enterprises. But, adopting state of the art security solution discussed in this paper organizations can save themselves from such losses.
IX.FUTURE WORK
Enterprise security is a wide domain and the applications using wireless devices like mobiles and smartphones are pushing corporate functions toward wireless networks seamlessly. One of the technologies to secure wireless networks is the cryptography. But, security of the cryptographic system lies in the encryption key. Since, encryption is being used extensively for data storage and data transmission, that is why, we shall explore state of the art mechanisms being used for encryption key generation in wireless networks.
ACKNOWLEDGMENT
We are thankful to anonymous reviewers whose suggestions and recommendation help us to improve the quality of this article.
REFERENCES
[1] G. He,X. LinX. shen Houngwei L., "Towards Hierarchical Security Framework for Smartphones," in First IEEE international Conference on Communications, China, 2012, pp. 214-219. [Online].
http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=6356880 [2] Darl Kolb, Judith MacCormick Kristine Dery, "Working with connective
flow: how smartphone use is evolving in practice," Eur J Inf Syst (2014), vol. 23, no. 5, pp. 558–570, 2014.
[3] Michael R. Overly. (2014) Information Security and Legal Compliance: Finding Common Ground in a Mobile Environment. [Online]. http://media.kaspersky.com/en/business-security/Kaspersky-Information-Security-Compliance-Whitepaper.pdf
[4] Jeffrey Saret, Peter Weed Lisa Ellis, "BYOD: From Company_issued to Employee_owned Devices," A Publication of the Telecommunications, Media and Tenchnology Practice, Recall No. 20, June 2012.
[5] D.Westoff, H. Rajasekaran Osman Ugus, "A Leaky Bucket Called Smartphone," in 2012 IEEE International Conference on Pervasive Computing and Communications Workshops (PERCOM Workshops), Lugano, 2012, pp. 374 - 380. [Online].
http://ieeexplore.ieee.org/stamp/stamp.jsp?tp=&arnumber=6197513 [6] J. Padgette K. Scarfone, "Guid to Bluetooth Security(Rev. 1)," vol. Special Publication 800-121, no. Revision 1, pp. 1-10, June 2012. [Online]. http://csrc.nist.gov/publications/drafts/800-121r1/Draft-SP800-121_Rev1.pdf
[7] Patrick Sweeney, "10 Best Practices: Controlling Smartphone Access to Corporate Networks," network security business unit, SonicWall Inc., White Paper 2010. [Online].
http://www.cso.com.au/whitepaper/370162/10-best-practices- controlling-smartphone-access-to-corporate-networks/?type=other&arg=0&location=featured_list
[8] Bruce Snell, "Mobile Threat Report," McAfee Labs, Intel Security, Santa Clara, CA, McAfee Mobile Security Analysis 2016. [9] Ashwini Jayawant, Geetanjali Kale Poornima Mahesh, "Smartphone
Security: Review of Attacks, Detection and Prevention," International Journal of Advanced Research in Computer Science and Software Engineering, vol. 5, no. 3, pp. 141-145, March 2015.
[10] Motorolla, "Securing Smartphones in the Mobile Enterprise," Motorola, USA, Technical Brief 2012. [Online].
https://www.zebra.com/content/dam/msi-new/assets/web/Business/Products/Software%20and%20Applications/R hoMobile_Suite/RhoStudio/_Documents/_Staticfiles/Securing-Smartphones-TB-0812.pdf
[11] Helen J. Wang, Wenwu Zhu Chuanxiong Guo, "Smart Attacks and Defences," in in Proc. ACM SIGCOMM , Dec, 2004, pp. 125-130. [12] Ammar Alazab, LynnBatten Moutaz Alazab, "Smartphone Malware
based on Synchronization Vulnerabilities," in The 7th INternational Confereence on Information Technology and Application(ICITA 2011), Sydney, N.S.W. , 2011, pp. 18-13.
[13] Fabrio M.,Deniel Sgandurra Mariantonieta L. Polla, "A Survey on Security for Mobile Devices," in IEEE Communications Survey & Tutorials, 2013, p. Vol.15 N01.
[14] Divya Lal, Kunal Gandhi, Kshitij Salariya Bhavya Chojar, "Study of Smartphone Attacks and Defenses," International Journal Of
Engineering And Computer Science, vol. 2, no. 4, pp. 1018 -1022, April 2013. [Online].
http://www.ijecs.in/ijecsissue/wp-content/uploads/2013/04/1018-1022ijecs.pdf
[15] Jiawen Zhang, James Gleeson, Sahil Suneja,Eyal de Lara, Himanshu Raj,Stefan ,Saroiu, and Alec Wolman Patrick Colp, "Protecting Data on Smartphones and Tablets from Memory Attacks," in ASPLOS ’15, Istanbul, Turkey, March 2015.
[16] Sang-Yong Choi Jae-Kyung Park, "Study Security Weaknesses of Android System," International Journal of Security and its Applications, pp. Vol.9 , No3, pp 7-12, 2015.
[17] Benjamin W. Fortenberry, Kevin Lynn, Daniel H. Bendell, Joshua Reed Chris Lathem, Configuring SoinicWALL Firewalls, 1st ed., Brad Dinnerman, Ed. Rocklanf, Plymouth, Massachusetts, USA: Syngress Publishing, Inc., 2006.
[18] Y. Fledel,U. Kanonov, Y. Elovici , S. Dolev Asaf Shabtai, "Google Android: State of the Art Review of Security Mechanisms," arXiv preprint arXiv:0912.5101, 2009.
[19] Hanc G. Schmidt, J. Clausan,A. Campete, S. Albayrak Aubrey D. Schmidt, "Enhancing Security of Linux-based Android Devices," in 15th International Linux Kongress, Hamburg Germany, 2008.
[20] Sebastian Schrittwieser , Peter Fruehwirt , Peter Kieseberg , Edgar Weippl Robin Mueller, "Security and privacy of smartphone messaging applications," International Journal of Pervasive Computing and Communication, vol. 11, no. 2, pp. 132 - 150, 2015.
[21] Vijay Dheap Darren Argyle, "Accelerating the Deployment of a Secure Mobile Enterprise," IBM, USA, Technical Report on Secure Mobile Enterprise October 2012. [Online].
ftp://public.dhe.ibm.com/software/uk/pdf/infosec/Accerating_the_deplo yment_of_a_secure_mobile_enterprise.pdf
[22] Paul Robert. (2010, December) usa.kaspersky.com. [Online].
http://usa.kaspersky.com/sites/usa.kaspersky.com/files/Enterprise%20M obile%20Survey.pdf
[23] Nokia Threat Intelligence Laboratories, "Nokia Threat Intelligence Report –H1 2016," Nokia Security Center, Berlyn, Mobile Security Report 2016.
[24] S.Dritsas, Bill Tsoumas, D. Gritzalis Alex Mylonas, "Smart Security Evaluation-the malware attack case," in in Procceeding of International Conference on Security & Cryptography(SECRYPT 2011), Spain, July 2011, pp. 25-36.
[25] Ernst & Young. (2012, january) www.ey.com. [Online].
http://www.ey.com/Publication/vwLUAssets/Mobile_Device_Security/$
FILE/Mobile-security-devices_AU1070.pdf
[26] Karen Scarfone Murugiah Souppaya, "Guidelines for Managing and Securing Mobile Devices in the Enterprise," National Institute of Standards and Technology, USA, Draft June 17, 2013. [Online]. http://nvlpubs.nist.gov/nistpubs/SpecialPublications/NIST.SP.800-124r1.pdf
[27] Samsung Research America, "White Paper: An Overview of Samsung KNOX Platform," Samsung KNOX Platform, pp. 1-25, August 2016. [Online].
https://www2.samsungknox.com/en/system/files/whitepaper/files/An%2 0Overview%20of%20the%20Samsung%20KNOX%20Platform_V1.15. pdf
[28] "The Future of Mobile Enterprise Security," Pique Solutions, San Francisco, Canada, White Paper August 2014. [Online].
http://www.oracle.com/us/products/middleware/identity-management/mobile-security/mobile-ent-security-future-2283375.pdf [29] McAfee. (2014) McAfee Enterprise Mobility Management Platform
Secure, easy and scalable enterprise mobility. [Online]. http://download.mcafee.com/products/manuals/en-us/MMS_DataSheet_2014.pdf
[30] Dell, "2016 Dell Security Annual Threat Report," Dell, USA, White Paper 2016. [Online]. https://www.sonicwall.com/docs/dell-security-annual-threat-report-2016-white-paper-19757.pdf
[31] Wil Kelieber Lori Flynn, "Smartphnoes Security," IEEE Pervasive Computing, vol. 14, no. 4, pp. 16-21, October 2015.
[32] B. Markschyeffel and T. Seffarth D. Fisher, "Smartphone Security: Overview of Security Software Solution," in 8th International Conference for Internet Technology and Secured Transactions(ICITST), London, 2013, pp. 288-289.
[33] Santhosh Reddy Aala, "Making BYOD Work for Your Organization," New Jearsy(USA), Technical Report 2012.
[34] Maryam Var Naseri , H. Hashim , N. M. Tahir Meisam Eslahi, "BYOD: Current state and security challenges," in 2014 IEEE Symposium onComputer Applications and Industrial Electronics (ISCAIE), Penang, April,2014, pp. BYOD: Current state and security challenges. [35] Mohammed Ketel and Thomas Shumate, "Bring Your Own Device:
Security technologies," in SoutheastCon, Fort Lauderdale, FL, 9-12 April 2015, pp. 1 - 7.
[36] Colin Steele, Lisa Phifer Robert Sheldon. (2014) www.techtarget.com. [Online]. http://media.techtarget.com/digitalguide/images/Misc/EA-Marketing/NetSec_CTD/MobileApplicationDeliveryTheNextFrontier_h b_final.pdf
[37] Karen Scarfone Murugiah Souppaya, "Guide to Enterprise Telework,Remote Access, and Bring Your Own Device (BYOD) Security," NIST, USA, Draft March 2016. [Online].
http://csrc.nist.gov/publications/drafts/800-46r2/sp800_46r2_draft.pdf [38] Raju PP. (2014, October) http://www.techpp.com/. [Online].
http://techpp.com/2010/12/30/android-security-apps/ [39] ESET, "ESET: Secure Business," Data Sheet 2014. [Online].
http://d1q82mpda228xr.cloudfront.net/Files/Product-Ovrview/ESET-Bundles-Secure-Business.pdf
[40] Trend Micro, "Worry-Free Business Security," Trend Micro, Tokyo,Japan, Data Sheet 2015. [Online].
https://www.trendmicro.com/cloud-content/us/pdfs/business/datasheets/ds_worryfree_family-new.pdf [41] McAfee, "McAfee Mobile Security," Canada, Data Sheet 2015.
[Online]. http://download.mcafee.com/products/manuals/en-us/MMS_DataSheet_2015.pdf
![TABLE 3. CORPORATE SECURITY FEATURES [25]](https://thumb-us.123doks.com/thumbv2/123dok_us/259872.2021764/3.612.315.566.454.624/table-corporate-security-features.webp)