MODIFICATIONS IN PROXIMITY
BASED ACCESS CONTROL FOR
MULTIPLE USER SUPPORT
S. M. DIDAR-AL-ALAM
Department of Computer Science and Information Technology (CIT), Islamic University of Technology (IUT), Board Bazar, Gazipur-1704, Bangladesh
didar522@gmail.com HASAN MAHMUD
Department of Computer Science and Information Technology (CIT), Islamic University of Technology (IUT), Board Bazar, Gazipur-1704, Bangladesh
hasan@iut-dhaka.edu
PROF. DR. M. A. MOTTALIB
Department of Computer Science and Information Technology (CIT), Islamic University of Technology (IUT), Board Bazar, Gazipur-1704, Bangladesh
mottalib@iut-dhaka.edu Abstract:
Automated access control model is an emergency access control system that offers a security policy which allows automated secured access to resources without making the user aware of it. User relaxes from all security overheads while the system continues to provide security all the time. Thus it builds up an efficient working environment by ensuring timely response and much higher security. This paper presents some modification of a well known access control model named - “Proximity Based Access Control (PBAC) System”. In PBAC we have found some special cases where the system can’t perform well with its multiuser support mechanism. We have tried to make the model working with equal ability in all such situations, and proposed the following major modifications i) addition of a third layer in the proximity zone (A three tier architecture) and ii) multiuser supporting environment - where multiple resources can be assigned to multiple users at the same time, and iii) addition to the level of roles for the users- to work with more precision and security. We have simulated the proposed modifications and found that they will help the PBAC to achieve more security, invisibility along with higher utilization rate.
Keywords: Emergency access control; Proximity Zone; Proximity Based Access Control; Roles; Security; Authentication; Multiuser Support.
1. Introduction
only by an authenticated person, for our case the team leader of the fire fighter team. An automated access will provide full access to the team leader and limited access to the other members for the data depository and helps the system to run smoothly without bothering them to authenticate again and again for different issues. The system is preserving the security issues automatically by authenticating the members and providing the exact level of service. Users are using the system in a controlled environment while being unaware of the security matters. Thus automated access reliefs the workers from these security distractions and helps to serve with more concentration as described in [Taylor et al. (2000)].
Fig. 1. Key issues of PBAC.
Different mechanisms are available for automatic access control. In our paper we specially focused on PBAC system and proposed modifications. In PBAC the user will get himself authenticated by their proximity to a computer. Resources have their own established Proximity zone where the user is identified by his role and given privileges. System will automatically grant access to a resource according to the specified role of the user when he is willing to use it. Depending on different levels of privileges different roles are created using the Role Based Access Control (RBAC) System [Sandhu et al. (1996)]. Each of the users are assigned specific roles and thus given a specific level of privileges to resources. Under normal circumstances PBAC works well. But in some critical scenarios, like a multiuser environment the system has to be handled with extra care. In our paper we have tried to find a way to handle such multiuser critical scenarios using proposed three tier architecture and five levels of roles as a modification of the current PBAC system in [Gupta et al. (2006B)].
2. Motivation
PBAC System is not capable of finding out the exact solution in some of the critical cases that we mentioned before. Our main motivation behind this paper was to find out a better solution to overcome authentication problems in such critical scenarios using PBAC. In Emergency Departments PBAC has already proved itself greatly useful by reducing the load of repetitive administrative tasks from the caregivers. When PBAC was first introduced and tested some critical scenarios were reported. Suppose when a patient is coming he is waiting for getting himself registered to the system and being served by the doctor. If it is an emergency case may be the patient is directly admitted to the emergency ward and offered treatment from the very beginning. For a normal patient he is first checked for his problems and if there is any need for admission then he is registered under the hospital section and sent to a treatment zone with different facilities. Otherwise he is offered treatment and discharged. Whenever a patient is treated his medical records and other information must be observed by the doctor. Different level of employees will access different level of data. How the authentication would be done automatically? In PBAC when a user is present within a proximity zone of a resource then he would be given access to that resource according to his allocated role. But what would happen when multiple users are present? PBAC suggests that one user would be selected and he would be given access to the resources. User selection would be done either randomly or FCFS basis or by determining the user who is closest to the resource. What can be a better selection process in such a situation?
Another issue is the number of authentication levels. As there are three authentication levels for a hospital scenario the doctor and nurse may be allocated the same authentication level. But they should have different authentication privileges. If they have so then what would be the allocation criteria when multiple users of different levels like doctors and nurses are present at the same moment in a Proximity zone?
In the proximity area if there are three resources A, B and C may be the user Mr. X is using resource A other resources B, C are also occupied by Mr. X. Another user Mr. Y in the proximity zone willing to use resource B is waiting for Mr. X to logout. How can we ensure more usability of resources? These were the basic questions before us. In our paper we tried to provide solutions for these questions by proposing new modifications to the PBAC.
3. Multiple User Support In PBAC Environment
We are discussing about a multi-user supported PBAC system - an automated access control system that supports a multi-user environment using PBAC with more flexibility, usability and higher security. We have proposed some modifications for PBAC system. In figure-1 we have depicted all the basic key-issues of PBAC. Among them four specific issues are our concerns those are shown in the figure 1 in yellow. Mainly the modifications are proposed in the authentication structure, authentication level and the proximity zone layers. Some other changes might be needed with other issues of the PBAC as a reflection to the modifications proposed. Key-issues need to be described in details to understand how multiuser support works in PBAC.
3.1. Detecting proximity zones
doctor and User2 may be a nurse is present inside the proximity suppose Doctor is given access to all 4 resources. But he is using only the Resource B. What would happen if in the mean time the nurse use resource C with the doctor’s access? This is a security attack for the system. To find out a solution we have proposed modification in the architecture-the three tier architecture. Now definitely a third layer of proximity detection will cause more power consumption and more calculation. For a single user case the two tier architecture works fine. So suggest that for a single user we will not take the burden of this extra calculation or power consumption. So for a normal case shown in figure 2 (A) where there is only one user 1 in the proximity zone the third layer of the system will be deactivated. First two layers of proximity Zone1 and Zone2 are for all the resources. Individual resources do not have any proximity of their own. In the given case all the resources are given access to User1.
Fig.2. Supporting multiple users using PBAC (Three tier architecture)
Now an approaching user User2 come inside the outer zone Zone1 and the system is reported about his approach. But User1 continues to work. As User2 comes inside the inner zone Zone2 the system activated its third layer of proximity. As we can see in Figure 2 (B) this layer of proximity is a tiny proximity zone for each of the resources individually. And then each resource tries to find a user in its own proximity. Resource B finds out User1 and gives access to him. Until and unless other users are present other resources will remain free. So this ensures if another user tries to use another resource he will get his own privileges not User1 Privileges. So we can ensure better security here. Now User2 is coming inside the Zone3 for resource C and he gets access to it. But resource A and D still remain free. So in this way we can satisfy four users simultaneously with four resources as resource is allocated to a separate user. This is improving the utilization rate of the resources. As User1 is not hampered with the User2 entrance and User 2 is using resource C. User1 continues to work with resource B and not bothered about a new user entrance and pushed to log out. Thus the system is gaining more invisibility. More than one user of different levels can work simultaneously as they are allocated different levels of access. So a fully multiuser environment is supported. Like an environment shown in Figure2 (C) it will work perfectly. When a user comes out of Zone3 the resource becomes free again and search for a new user to give access. If the entire users leave Zone1 except one user it a single user scenario so again the third layer of proximity is deactivated. In the figure 2 (C) we can see how the three tier architecture helps in supporting a multiuser scenario.
3.2. User positioning mechanism
Context aware access control policies have been discussed in [Sampemane et al. (2002)]. In emergency department smart spaces supplies the necessary information [Black et al. (2004)] continuously and thus help to make the system
(A) (B)
automated. One of the most important parts of the whole system is to find out the exact location [Bardram et al. (2003)] of the user in the context area as much accurately possible. The success of the system is dependent upon the accuracy of the positioning mechanism. We have options like Radio Frequency Narrow Band, UWB and RF Ultrasound. We are talking about indoor scenarios. As UWB – Ultra Wide Band shows better performance especially in indoor environment and also serves us to find a user even with a smaller proximity [Gupta et al. (2006B)]. We are reluctant to change to any other mechanism. For user positioning we are using the same UWB as suggested in [Gupta et al. (2006B)]. Positioning mechanism using UWB works well even when the third layer of proximity activated.
3.3. Levels of authentication
Levels of authentications are one of the most crucial parts of the system as roles are defined here. Depending on the level of authentication different roles are created to have different privileges. To find out the roles and their privileges we use the RBAC [Sandhu et al. (1996)], [Moyer and Ahamad (2001)] in our system. But in our proposed version we have modified the levels of authentication. In spite of declaring three authentication levels we have given five levels of authentication to specify privileges accurately. Authentication levels will not work only for accessing data but also for controlling and regulating different equipments. Our proposed five levels of authentications and their privileges are briefly described here. From figure 3 we can easily visualize the scenario that which level is given how much privileges for information access and control
3.3.1. Non-user
Not a privileged user of the system. Very few privileges offered to a non-user. Access is restricted only to data that are publicly available. Non-user will not get access to any other private data or control over any equipment.
3.3.2. Monitoring-user
Monitoring users have privileges to access a limited domain of data. They have monitoring capabilities to different equipments. For example nurses may get this authentication level. They will be allowed to get limited information about the patient’s medical history, his diseases and doctors orders. He may also monitor the equipments to get the physical condition of the patient. But she will not be allowed to make any change. Only monitoring facilities are given.
3.3.3. Control-user
Control user1 has access to a larger domain of data along with control over the equipments. The basic difference with monitoring users is to gain control over the equipments. For example- Doctors may get this level to monitor the equipment, get access to past data and present treatments and make change in the equipments for new treatment conditions. These users can monitor and control at the same moment.
3.3.4. Control-user2
Fig. 3. Different authentication levels and their privileges.
3.3.5. Administrative user
Administrative user gets access to the data about the patient along with his past histories and present treatments. But they don’t have access to monitor the equipments or to control them. Administrative users are focused on the information and results of the patients, not with the procedures that how it is happening. Suppose the billing management system will get such an access on a patient.
3.4. Access control policies
The access control system mechanism can be divided into different parts. In this section we are briefly describing each steps of the system. There is a system administrator associated with the system to control the whole system. First of all, for the system to run perfectly we need new users attached to the system and their roles has to be specified perfectly. Then we are going to use the new modified algorithms to handle the access control.
3.4.1. Adding and removing users
A new user to the system needs to get registered to the system first. Already in [Gupta et al. (2006B)] details specifications are discussed along with the algorithm for adding and removing users. As with this section we don’t have any modification so it’s just a normal adding and removing of users. So we have not imposed any modification with the mechanism and algorithm proposed wit PBAC. At first the administrator checks the validity of the user. If the user is a valid one then we needs to find out a specified role that suits him most with all needed privileges. The user becomes a member of the access control system along with an associated role. Again for removing and user from the system, if at some point the user himself or any of his role or both are not valid any longer the user along with his associated role is discarded from the system. The whole operation of adding and removing users is done by the system administrator.
3.4.2. Adding and removing groups
3.4.3. Adding or removing user to a group
For assigning a group to user, the user must satisfy three conditions. As a valid member he should be a member of USER group, his roles should be valid under the user roles UROLE and the roles should be also a match with the group roles of I group in GROLE (i). Only then the user would become a member of the group i and listed under the GUSER (i) as a member. The algorithm for this purpose is given below.
GROUP=All valid user groups
GROLE (i) =All valid group associated with roles GUSER (i) = All valid users of a group
USER=All valid users
i Є GROUP
x Є All possible users r Є All possible roles
1. //Adding user to a group
2. If (x Є USER Λ {x, r} Є UROLE Λ r Є GROLE(i) ) then 3. GUSER(i) =GUSER(i) U {x}
4. end if
5. //Removing user from a group
6. If({x, r} UROLE V r GROLE(I) V {x} USER ) then 7. GUSER(i) =GUSER(i) - {x}
8. end if
3.4.4. Single User in the Proximity Zone
If we find only one active user in the Proximity Zone2 then there is no complexity. We will find out his group identity and depending on his role privileges we will allow him access to group of resources present within Zone2. There is no need to activate the Zone3. If we have an approaching user from Zone1 system will notify about him to the previous user but it will not activate Zone3 until and unless he enters Zone2. Following algorithm will be used for this case
GROLE (i)=All valid group associated with roles USER=All valid users
x, y Є All possible users
M = All equipment (m, n, q) within zone 2 1. //Single user in proximity zone2 2. If (x Є USER Λ active (x, zone2)) then 3. allocate(M,GROLE (Check group (x))) 4. end if
5. //Other user in zone 1 coming towards zone2 6. If (y Є USER Λ active (y, zone1)) then 7. Notify (x);
8. end if
9. //user exits proximity zone 2
10. If (x Є USER Λ exits (x, zone2)) then 11. allocate(M, ф);
12. end if
3.4.5. Multiple users in the proximity zone
scenario. The Zone3 authentication is activated. Now all three equipments within Zone2 use their own Zone3 layer to find out its own user. Suppose Resource m gets x and Resource n gets user y in its Zone3 proximity layer. It is allocated to that specific user whom the system founded in its Zone3. q Does not have any active user in its Zone3 so it is not allocated to anyone. A new user may get access to it. If someone request for occupied equipment he has to wait until the present user logs out. Then he will get access to the resource. The algorithm is given below for this case
GROLE (i) =All valid group associated with roles USER=All valid users
X, y Є All possible users
M = All equipment within zone 2
m, n, q Є M, All equipment within zone 2 1. //Single user in proximity zone2 2. If (x Є USER Λ active (x, zone2)) then 3. allocate(M, GROLE (Check group (x))) 4. end if
5. //Other user coming towards zone2 6. If (y Є USER Λ active (y, zone1)) then 7. Notify (x);
8. end if
9. //multi user comes to zone 2
10. If (y Є USER Λ active (y, zone2)) then 11. allocate(M, ф);
12. activate (zone3); 13. detect user(m,zone3); 14. If (active (x, m, zone3)) then
15. allocate(m, GROLE (Check group (x))) 16. end if
17. If (active (y, n, zone3)) then
18. allocate(n, GROLE (Check group (y))) 19. end if
20. If (active (ф, q, zone3))then 21. allocate(q, ф)
22. end if 23. end if 24. // user x exits
25. If (x Є USER Λ exits (x, m, zone3)) then 26. allocate(m, ф);
27. end if
4. Simulation
We have analyzed the performance of the modification for PBAC system stated earlier through a simulation. The simulation has done in java programming language. We have depicted all the algorithmic details of the system along with the modifications and tried to find out how the system acts in the stated critical scenarios. Here in this paper we have presented a few snapshots of the simulation window.
Fig. 4. Single user in Proximity Zone2
In figure 4 we can see the basic window of simulation with two tier architecture. We can see the details of the user management on the right panel of the window. In the proximity zone we can select the position of a user with a single mouse click. We can fix the role of the user.
Fig. 5. Multiple users in Zone2, Zone3 Activated
for a specific scenario. Here a default proximity area is given. We can also see the users in different proximity zone and the list of the users. It shows for each of the individual equipment who is the active user now. In this figure as there is only one user he is now occupying all three resources at the same time. And also the third layer still not activated as the system has not found any multiuser scenario.
In figure 5 we can see that there are two users in the zone 2 and thus the zone 3 is activated and each of the equipment is individually selecting its own user. As there is only one user using the resource at this moment the other two resources remain free.
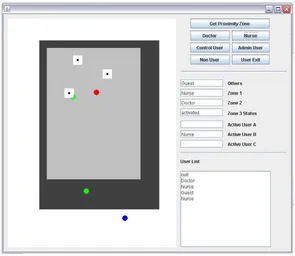
Fig. 6. Multiple user access using Proximity Zone3
In figure 6 we can visualize a full multiuser scenario where there are two users using two of the resources and one resource is free. And we also have a queue for the present users of the system. We have just presented a few snapshots of the simulation and from the simulation we found that the PBAC is performing better with the modifications in different critical scenario.
5. Discussion
In this paper our basic concern was to work with PBAC and find out a modified version where we can handle all kind of multiuser scenarios. So the basic modifications we did with the proximity zone architecture and the authentication level. We offered three tier architecture and a five level of authentication. Because of this modifications we found that the system becomes more flexible, robust, highly secured and more invisible. Moreover we achieve our primary goal that is creating a support for multiuser scenario. PBAC offers a two tier structure where a user gets the access to all the equipments inside the proximity region at the same time. When a second user comes inside proximity zone user is chosen and given access using FCFS or closest distant mechanism or random procedure. We have added one more layer of proximity to the structure to gain more flexibility in supporting multi user. More authentication levels are used for better security. Now how they help in different situations.
In a region if different types of user are present at the same time intend to use different equipments it can be handled. Because of introducing Zone3 different equipments in a zone can allow different user access. It of course offers higher security and more usability as one user is not occupying all the resources. Also for a temporary absence of the user it gives relief to the system. It can offer some time to be logged on if the user might come back. But if some other user is detected it logged out instantly.
Third layer of proximity is mostly deactivated. So it is not consuming power and creating complexity for calculation all the time. If a multi-user situation arises the Zone3 is activated and gives support to the system to handle multiple users perfectly.
Five level of authentication definitely offers much more secured data access and control to the system. We can have more specific role for each of the group and more robust accessing mechanism. Moreover the possibility of overlapping role is very minimal thus offers distinct roles for any type of system. It makes the decision easy to find out the privileges for a offered role.
6. Conclusion And Future Work
PBAC is one of the most popular and fastest mechanisms for automated access control. To make it more user friendly and perfect for a multi-user environment was a challenge for us. As the system itself offers solutions for multiuser environment we had to find out a better solution. Moreover the critical scenarios that we have already explained in the paper were not possible to manage properly using PBAC. We had to find out a solution that works well in those scenarios and in all other possibilities we applied different techniques to the system and found out the modifications that offers benefit to the system. At last we have come to a solution for our key problem issues. But there is always chance for improvement. Like supporting a very frequent repetitive change of users like in an operation theatre we need faster detection mechanism and more perfect positioning system. So finding out such an approach can be a future research direction related to this topic.
References
[1] Bardram J. E., Kjær R. E., and Pedersen M.. "Context-ware User Authentication – Supporting Proximity-Based Login inPervasive Computing," Proceedings of Fifth International Conference on biquitous Computing (Ubicomp), LNCS 2864, Springer, 2003, pp. 07-123. [2] Black J. P., Segmuller W., Cohen N., Leiba B., Misra A., Ebling M.R., and Stern E.. “Pervasive Computing in Health Care:Smart Spaces
and Enterprise Information Systems”. In Proc.ACM MobiSys, Workshop on Context Awareness, 6 pp. June 9 2004
[3] Gupta S.K.S., Mukherjee T. and Venkatasubramanian K. “Criticality Aware Access Control Model for Pervasive Applications”. In submission to IEEE Percom 2006A.
[4] Gupta S. K. S., Mukherjee T., Venkatasubramanian K., and Taylor T., "Proximity Based Access Control in Smart-Emergency Departments," Proceedings of 4th IEEE Conference on Pervasive Computing Workshops, First Workshop On Ubiquitous & Pervasive Health Care (UbiCare), 2006B, pp. 512-516.
[5] Moyer MJ, Ahamad M, "Generalized Role-Based Access Control," Proceedings of the 21st IEEE International Conference on Distributed Computing System, 2001, pp. 391-398.
[6] Radianse Indoor Positioning http://www.radianse.com
[7] Sampemane G., Naldurg P. and Campbell R. H.. “Access control for Active Spaces”. In Proc. of ACSAC, 2002
[8] Sandhu R., Coyne E.J., Feinstein H.L. and Youman C. E. “Role Based Access Control Models”. In IEEE Computer, Feb, 1996.pp 38-47. [9] Taylor T. B. “A View of the Emergency Department of the Future”. ACEP Section for Emergency Medical Informatics 2000, Dallas, TX. [10] The Aware Home Project.