Network challenges with IOT with TCP/IP Architecture
Dolly Dave
Assistant Professor, MCA, Aravali Institute of Technical Studies Rajasthan Technical University Kota, Udaipur (Raj.), India
Email – davedolly13@gmail.com
1. OVERVIEW:
Internet of Things" (IoT) is now of defined as an interconnection of various kind of registering gadgets to help different sorts of checking and control applications. To oblige the heterogeneity of gadgets and applications from different sellers, present day IoT frameworks have received the open principles of TCP/IP convention suite, which was created for the wired worldwide Internet a very long while prior, as the systems administration arrangement. Nonetheless, IoT systems differ from conventional wired PC arranges in essential courses as we expound beneath. Those differences present significant difficulties in applying TCP/IP advancements to the IoT condition, and tending to these difficulties will have an expansive effect on the system design. This dad per means to efficiently distinguish the difficulties presented by the IoT condition, and to explain the future course to handle the difficulties. IoT arranges frequently contain a substantial number of low-end, asset compelled gadgets. The structure of those gadgets is for the most part determined by low assembling and operational expense. Therefore, the IoT gadgets are ordinarily furnished with restricted processing force and required to mesh over long timeframes (e.g., a year) on battery. Because of the power constraints, the IoT organizes regularly utilize low-vitality Layer-2 advancements, for example, IEEE 802.15.4, Bluetooth LE and low-control Wi-Fi, which more often than not mesh with a lot littler MTU and lower transmission rate contrasted with conventional Ether-net connections. Hence a quick test for the IoT organize convention configuration is to adjust the bundle size to the compelled connections (talked about in Section 2.1). To spare vitality, IoT hubs may not be dependably on as in wired systems. Progressively more than, an IoT framework might be sent in conditions without wired system foundation (e.g., woodlands, submerged, battle fields) and therefore needs to depend on remote mesh innovations to convey. This conveys more difficulties to the TCP/IP convention engineering: First, mesh organizes ordinarily embrace the multi-connect subnet demonstrate which isn't sup-ported by the first IP tending to design (talked about in Section 2.2); second, communicate and multicast are expensive on a battery controlled system as a solitary multicast will include a progression of multi-bounce sending and possibly wake up many resting hubs (examined in Section 2.3); third, an adaptable directing instrument is presently fundamental for IP communications to occur over the mesh systems (talked about in Section 2.4); and in conclusion, the TCP-style dependable and all together byte stream conveyance is frequently ill suited for applications that require tweaked control and prioritization of their information (examined in Section 3). Most IoT applications cooperate with loads of sensors and actuators to perform different checking and control undertakings on the surrounding condition. Their structure designs intrinsically require efficient and versatile help for naming configuration and revelation, security insurance on the information air conditioning quisition and incitation tasks, and an asset situated correspondence interface, for example, Representational State Transfer (REST). Tragically, existing answers for those problems, a large number of which are broadly utilized by the present Web technologies, don't fulfill the imperatives of the IoT environments. For instance, the customary DNS-based naming ser-indecencies are unsatisfactory in numerous IoT organization situations that need infrastructural bolster for devoted servers (see Section 4.1). The application-layer content reserves and intermediaries are frequently inefficient in unique system situations with irregular network (examined in Section 4.2). In promotion edition, the channel-based security conventions, for example, TLS and DTLS, which are utilized to anchor the REST
Abstract: Internet of Things" (IoT), collectively (conceivably) a substantial number of asset obliged devices, is increasing prevalentily as of late. The present IoT frameworks are to a great extent dependent on the utilization of the TCP/IP conventions (IPv6 specifically). Nonetheless, the perceptions so far recommend that the TCP/IP convention stack, as initially planned, is certainly not a decent t to the IoT condition. Throughout the most recent quite a long while the IETF has spent significant measure of effort in altering the convention stack to IoT organization situations. These efforts have brought about expansions to existing conventions in the TCP/IP convention suite and in addition improvement of various new start protocols. However new issues ceaselessly happen. In this paper we break down the specialized difficulties in applying TCP/IP to the IoT condition and survey different arrangements proposed by the IETF. We contend that current IP-based arrangements are either inefficient or insufficient in supporting IoT applications, and that a more effective arrangement would grasp the Information Centric Network design.
communications, force high overhead on the IoT gadgets regarding convention activities and asset utilization (talked about in Area 4.3).
Whatever remains of this paper talks about each of the aforementioned issues in detail. We try to recognize the structural reason that causes the difficulties while applying TCP/IP to the IoT world. We likewise overview the present answers for those issues that have been institutionalized or under dynamic improvement at the IETF, and break down why they are regularly insufficient to take care of the focused on issues. The objective of this paper is to offer bits of knowledge and call attention to headings for the structure of future IoT arrange models.
2. PROBLEMS AT NETWORK LAYER:
IP, particularly IPv6, is built for the present Internet environment with mesh areas and mesh stations as end gadgets communicating with wire-associated servers. In this segment we examine which properties of the hosts and the systems currently expected by IP never again exist in the IoT world, and what have been done to tailor IP and its sidekick proto-cols to t them into the IoT condition.
2.1 Small MTU
The obliged low-vitality interfaces in IoT organizes frequently have little MTUs. For instance, the greatest physical layer outline measure for IEEE 802.15.4-2006 is only 127 bytes. This is in clear stand out from the present IP systems which ordinarily expect a base MTU of 1500 bytes or higher. Created for the customary Internet amid 1990s (some time before the view of IoT), the IPv6 specification incorporates two plan choices that are hazardous for little MTU joins. In the first place, IPv6 utilizes a 40-byte fixed length header with discretionary augmentation headers, which cause a major convention overhead for little bundles. Second, the IPv6 specification necessitates that all IPv6-fit systems bolster a base MTU size of 1280 bytes, which is implausible for the con-stressed connections.
To fit IPv6 into 802.15.4 systems, 6LoWPAN introduces, between the connection layer and the system layer, an adjustment layer that actualizes two instruments to handle the previously mentioned issues: header pressure and connection layer discontinuity . Header pressure permits the evacuation of unused fields (e.g., flow mark and traffic class) and repetitive data (e.g., the interface identifier in the IPv6 address can be gotten from L2 MAC address and subsequently omitted). It additionally defines the pressure plot for augmentation headers and UDP header, the two of which are frequently utilized in IoT (see Sections 2.4 and 3), so as to leave more space for application payload. Connection layer fragmentation shrouds the genuine MTU size of 802.15.4 and gives the system layer the figment that it is running over a standard-agreeable connection fit for supporting 1280-byte MTU. How-ever, few IoT applications are relied upon to send parcels that achieve as far as possible.
The fundamental motivation behind having fixed length header in IPv6 is to enhance convention handling speed. Setting a little mum MTU is to dodge in-arrange discontinuity (which is generally accepted to cause execution issues ) and reduce the switch's remaining task at hand. Then two are expected for execution streamlining in the present Internet, without the thought of obliged IoT condition with little MTU sizes. The expansion of the adjustment layer fixes up the jumble between the old structure and the new utilization prerequisite, which unavoidably presents additional intricacy and overhead.
2.2 Multi-link subnet
The current subnet model of IPv4 and IPv6 considers two sorts of Layer-2 systems: multi-get to connect, where different hubs share a similar access medium, and point-to-point interface, where there are actually two hubs on a similar connection. Then two expect that the hubs in the equivalent subnet can achieve each other inside one jump. An IoT meshs arrange, then again, contains an accumulation of Layer-2 joins consolidated with no Layer-3 gadget (i.e., IP switches) in between. This basically makes a multi-connect subnet display that isn't foreseen by the first IP tending to architecture.
RFC 4903, “Multi-Link Subnet Issues", records the reasons why the IETF people group chose to desert the multi-connect subnet display for 1:1 mapping between Layer-2 connections and IP subnets. The primary concerns are around the one-jump" reach ability demonstrates that many existing genius protocols as of now rely upon. To start with, sending crosswise over multiple connects inside the subnet makes issue with TTL/Hop-Limit dealing with. In IP systems usually practice to restrain the extent of correspondence to a solitary subnet by set-ting the TTL/Hop-Limit to 1 or 255 and check that the esteem remains the equivalent upon receipt. The multi-interface subnet model will break any convention that pursues such practice be-cause the hubs that perform IP sending over different connections will essentially decrement the TTL/Hop-Limit esteem. The second issue is that connect checked multicast does not take a shot at multi-interface subnets without appropriate help for multicast directing (which is regularly debilitated even in the present Internet). Thus, heritage conventions that rely upon connection perused multicast (e.g., ARP, DHCP, Neighbor Discovery, and many steering conventions) will likewise be broken on multi-interface subnets.
fragments), or segment the mesh arrange into different subnets with different prefixes. The rest approach requires some type of intra-subnet steering capacity, which will be talked about in Section 2.4. The second methodology introduces new multifaceted nature in system configuration as the pre-x allotment must be engendered over the mesh organize (e.g., by means of pre x designation) and the arrangement of the connections in a mesh may change after some time in a dynamic situation.
2.3 Multicast efficiency
A great deal of IP-based conventions makes substantial utilization of IP multi-cast to accomplish one of the two functionalities: telling every one of the individuals in a gathering and making a question without knowing precisely whom to inquire. Be that as it may, supporting multicast parcel conveyance is a major test for obliged IoT mesh systems. To begin with, most remote MAC conventions impair connect layer ACK for multicast; thusly lost bundles are not recouped at connection layer. Second, multicast beneficiaries may encounter different information transmission rate because of the conjunction of different MAC conventions (e.g., different variants of Wi-Fi) or potentially the connection layer rate adjustment; in this manner the sender needs to transmit at the most reduced basic connection speed among all collectors. Third, IoT hubs may change to resting mode every now and then to ration vitality, in this way may miss some multicast bundles. Ultimately, when hubs are connected through a mesh organize, a multicast parcel should be sent over numerous bounces along numerous ways, potentially awakening many dozing hubs and over-burdening the effectively rare system asset.
To get around the difficulties in multicast support, the legacy protocols have to be redesigned to minimize the use of IP multicast before they can be applied to constrained IoT environments. When IoT nodes need to send out notifications to multiple recipients, instead of multicasting the packets, they can buffer those packets temporarily at some well-known location and wait for the recipients to carry the packets over unicast on required demand (based on their sleeping schedule). When they want to make queries to a group, instead of flooding the network with multicast, they can send the queries to some designated nodes that are pre-configured to answer queries by collecting the information a prior. These new approaches replace multicast with on-demand unicast pulling, to get around the difficulties in supporting multicast and also to accommodate sleeping nodes.
To get around the difficulties in multicast bolster, the inheritance conventions must be updated to limit the utilization of IP multicast before they can be connected to compelled IoT conditions. At the point when IoT hubs need to convey notifications to numerous beneficiaries, rather than multicasting the packets, they can bu er those parcels briefly at some outstanding area and trust that the beneficiaries will pull the bundles over unicast on-request (in light of their dozing plan). When they need to make questions to a gathering, rather than flooding the system with multicast, they can send the inquiries to some assigned hubs who are pre-configured to answer inquiries by gathering the data a prior. These new approaches supplant multicast with on-request unicast pulling, to get around the difficulties in supporting multicast and furthermore to oblige dozing hubs.
One case of such convention adjustment is the IPv6 Neighbour Discovery (ND) enhancement for 6LoWPAN. The first IPv6 ND depends on multicast to learn default passage switches, resolve neighbour’s IPs to MAC addresses, and perform copy address discovery. While adjusting ND functionalities to 6LoWPAN, rather than having the switches multicast Router Advertisements intermittently (which will either awaken the resting hubs or be missed by those hubs), the improved convention enables the compelled hubs to invigorate Router Advertisement data on interest with Router Solicitation messages.1 Another augmentation is to keep up a library of host addresses on the switches, making the switches equipped for noting address goals and du-plicate address discovery asks for the benefit of the end has, so the questioning hubs basically send their inquiries to the default switches by means of unicast messages.
An elective arrangement called MPL, proposed by the IETF move WG, in a general sense changes the sending semantics of multicast over compelled systems. MPL disseminates multicast bundles over the whole multicast space through synchronization among MPL forwarders (i.e., hubs that take an interest in MPL) utilizing controlled flooding, without requiring any multicast directing convention to keep up the topology data. Each multicast bundle is identified by the parcel generator id and an arrangement number in order to permit duplication location. Likewise, ongoing parcels are buffered by the MPL forwarders in a sliding-window mold (i.e., FIFO buffer), which can be utilized for retransmission later on. This new multicast sending convention has been received by the current ZigBee IP specification.
2.4 Mesh network routing
Mesh arranges steering can be upheld at either the connection layer or the system layer. The connection layer approach, called mesh under in the IETF phrasing, depends on Layer-2 forwarders to join various connections into a solitary “one -IP-bounce" subnet. The system layer approach, brought course finished, in-stead depends on IP switches to forward bundles over numerous bounces. In whatever remains of this subsection, we portray the current arrangement in every one of these two classifications.
The IEEE has created the 802.15.5 standard to sup-port connection layer steering for mesh systems framed by IEEE 802.15.4 connections. The fundamental methodology is to first build a traversing tree over the mesh arrange for L2 address assignment: the base of the crossing tree distributes continuous connect layer deliver squares to its kids, which further assign sub-squares to its descendents. Such tending to approach ensures that the connection layer address of hubs under a similar precursor fall into a similar range. When the addresses are allocated, the hubs begin to trade nearby connection state data with their quick neighbors and every one of them manufactures its own 2-jump neighbor table containing the neighbors' location square range, tree level and bounce remove. When sending bundles to a goal past 2-bounce separate, the sending hub applies a basic heuristic to pick a next jump that is near the crossing tree root (and thus find out about the system topology) yet not very far from the sending hub. One disadvantage in this solution is that, as new hubs progressively join the system, the location allotment process may must be re-performed so as to adjust to the topological changes.
The IETF handles the mesh organize directing issue by means of the course over methodology and has created RPL (IPv6 Rout-ing Protocol for Low-Power and Lossy Networks) as the present standard arrangement. RPL shares a similar soul with IEEE 802.15.5 in that it displays a bunch of hubs as a traversing tree called Destination-Oriented DAGs (DODAG), with every coordinated way ending at the root. At the point when two hubs inside a DODAG speak with one another, their parcels cross up to either the root hub or a typical a cestor, at that point pursue a Down Link to the goal. Be that as it may, not at all like IEEE 802.15.5 which dispenses topology-subordinate L2 address, RPL does not make any supposition about IP address designation. This effectively precludes directing section conglomeration past the sharing of normal prefixes. Maintaining such a steering table turns out to be very testing at the hubs close to the root, which in the most pessimistic scenario need to continue directing passages for each gadget in the subnet. RPL likewise master vides an option “Non-Storing" mode, where just the root hub keeps up the steering table. When sending parcels along Down Link ways, the root hub needs to insert full source course data into the bundle headers. While it lessens memory use on the non-root hubs, the \Non-Storing" mode builds the header size of the down-ward bundles, which is hazardous for little MTU systems (see Section 2.1).
We should take note of that the crucial test of defeating in IoT mesh systems originates from the necessity of keeping up steering data for each host in a multi-connect condition. This isn't an issue in conventional IP net-works where switches or self-learning extensions can be sent to give infrastructural support to steering and forwarding. Be that as it may, in compelled IoT situations, the per-have courses are either kept up by each hub in the mesh utilizing steering conventions, which devours heaps of memory, or carried with the IP bundle as source courses amid sending, which conflicts with the little MTU confinement from the connection layer. Because of IP's host-arranged correspondence semantics, steering will remain a noteworthy test in IP-based IoT mesh advances.
3. PROBLEMS AT TRANSPORT LAYER:
The transport layer in the TCP/IP design gives blockage control and solid conveyance, the two of which are actualized by TCP, the prevailing transport layer protocol on the Internet. TCP has been built for a long time to efficiently convey an expansive greater part of information over an enduring point-to-point association without stringent inactivity requirement. It shows the correspondence as a byte stream among sender and recipient, and implements dependable all together conveyance of each and every byte in the stream.
Be that as it may, IoT applications for the most part confront an assortment of communication designs which TCP can't bolster efficiently. To start with, because of the vitality limitations, gadgets may every now and again go into rest mode, accordingly it is infeasible to keep up a seemingly perpetual association in IoT applications. Second, a ton of IoT correspondence includes just a little measure of information, making the overhead of setting up an association inadmissible. Third, a few applications (e.g., gadget incitation) may have low-idleness prerequisite, which may not endure the postponement caused by TCP handshaking. When meshing inside lossy remote systems, the all together conveyance and retransmission instrument of TCP may likewise cause head-of-line blocking, this presents superfluous postponement. Additionally, most wire-less MAC conventions likewise actualize interface layer programmed re-peat ask for (ARQ), which may additionally debilitate the performance of TCP if the L2 retransmission delay is longer than the TCP RTO.
efficiently with in-organize reserving, and so forth. Tragically, current TCP/IP design does not enable applications to implant application semantics into system level parcels, subsequently neglecting to give sufficient support to application level encircling.
4. PROBLEMS AT APPLICATION LAYER
Most IoT applications execute the asset situated demand reaction correspondence show. For instance, monitoring applications ask for information created by the sensors; and control applications ask for tasks on the physical articles through the actuators. These applications look like the present Web benefits that have received REST (Representational State Transfer) desig for application-layer correspondence. Influenced by the enormous accomplishment of Web, the
IoT people group has been taking a shot at bringing the REST design into IoT applications. For instance, the IETF center WG has defined “Constrained Application Protocol" (CoAP) standard, a UDP-based information exchange convention redid for compelled condition, to control REST-style correspondence for IoT applications. The requirement for actualizing REST at the application layer features the missing help of critical functionalities at the lower layers of the TCP/IP design, including asset discovery, storing, and security. In this segment, we look at how current IoT applications connect those holes and the limitation of their answers.
4.1 Resource discovery
The asset situated correspondence show as a rule re-quires an asset disclosure system, whereby the applications can ask for or summon activities on the assets. The answer for asset disclosure in conventional IP network is DNS-based Service Discovery (DNS-SD). How-ever, this arrangement has a few constraints in supporting IoT applications.
Above all else, DNS-SD intends to help benefit disclosure, where the administration more often than not alludes to a running project (e.g., a printing administration running on some printer). Conversely, the assets with regards to IoT covers a more extensive degree: other than administrations, it might likewise allude to IoT gadgets, sensor information, and so forth.. In this way, the IoT asset revelation requires a progressively broad way to deal with recognize heterogeneous assets. For instance, rather than utilizing DNS records, CoAP receives a URI-based naming plan to recognize the assets (like in HTTP). In light of that, the IETF center WG has created CoRE-RD , a CoAP-based asset revelation mechanism that depends on less compelled asset catalog (RD) servers to store the met info about the assets facilitated on different gadgets.
Furthermore, conventional administration disclosure regularly depends on multicast when committed administrations, for example, DNS and CoRE-RD are not accessible in the nearby condition. For instance, DNS-SD utilizes Multicast DNS (mDNS) as the transporter of correspondences for administration revelation and name goals inside the neighborhood organize. Be that as it may, as we dissected in Section 2.3, interface nearby multicast has efficiency issues in IoT environments. An elective answer for utilizing multicast is to synchronize the asset meta info over the system in a distributed manner (which is comparable in soul to the MPL multicast sending convention we examined in Section 2.3). For instance, the IETF home net WG is creating the Home Networking Control Protocol (HNCP) [28] to appropriate home system configurations utilizing a synchronization component defined by the Distributed Node Consensus Protocol (DNCP).
It is advantageous to take note of that the need of those solutions is because of the way that the system and transport layers in TCP/IP can't find the assets defined by the application-layer names. For instance, the Neighbor Discovery convention for IPv6 can just find configurations at the system layer and beneath; while the SRV records in DNS-SD ordinarily distinguish the administrations by the IP locations and port numbers. Given the widespread interest for asset disclosure in the IoT applications, an efficient IoT organize engineering ought to incorporate that as one of its center functionalities and free the applications from actualizing their own custom arrangements.
4.2 Caching
The TCP/IP correspondence show necessitates that both the customer (asset requester) and the server (asset holder) are online in the meantime. Be that as it may, in IoT situations, the compelled gadgets may as often as possible go into dozing mode for vitality sparing. In addition, the dynamic as well as discontinuous system condition more often than not makes it di clique to keep up stable associations between conveying parties. Consequently, the IoT applications frequently depend on reserving and proxying to accomplish efficient information spread. The selected intermediary hub can ask for the assets for the resting hubs and store the reaction information briefly until the asking for hubs wake up. The stored substance can likewise be utilized to serve comparative solicitations from different hubs who share a similar intermediary, which spares arrange transfer speed and decreases reaction idleness. The asset beginning server may likewise name some intermediary hubs to deal with the solicitations for its benefit (called turn around intermediary) so it can diminish the customer traffic and may go offline when it have to.
the con-tent storing ability. Those pre-configured storing focuses may not be ideal for all the customer hubs. The customers may use the asset revelation system to find close-by intermediaries on interest. In any case, such arrangement acquaints additional complexity with the entire framework. Second, in unique system situations where the availability is discontinuous, the pre-chosen intermediary point may turn out to be absolutely inaccessible. At the point when the system topology changes, the customers need to re-configure or re-find the intermediaries, or generally quit utilizing reserves and intermediaries by any stretch of the imagination. Third, the reserves and intermediaries break the start to finish associations expected by the present security conventions (which we will talk about in Section 4.3), making it significantly harder to ensure the application information.
To make the reserving usefulness efficient and flexible in the IoT condition, the system engineering need to give astute stores inescapably inside the system and enable the applications to use them without bringing about configuration and correspondence overhead. This further requires the system layer to know about the application-layer assets and incorporate the reserving into the sending procedure with the goal that each system parcel can investigate the stores as it navigate the system. It likewise requires an essential change to the security display so as to make the in-organize stores secure and reliable.
4.3 Security
Security is basic to IoT applications because of their nearby communication with the physical world. The standard security model of IP-based applications is channel-based security (e.g., TLS and its datagram variation DTLS), which gives a safe correspondence channel between the re-source server and the customer. The anchored channel arrangements, notwithstanding, don't t into the IoT conditions for a few reasons.
The first issue with channel-based security is the over-head of setting up a safe channel. The two TLS and DTLS require at least two rounds of security handshake to authenticate a channel and arrange the security parameters, before the first application information is conveyed.
The second issue is that the two finishes of a channel need to keep up the conditions of the channel until the point that it is shut. This may force a high weight on memory use when a de-bad habit needs to speak with numerous friends all the while in a thickly fit system. Note that this issue, together with the first one, prompts a difficult tradeoff. The e ort of moderating one issue (e.g., diminishing memory utilization by establishing short-lived channels on-demand) may deteriorate the other (e.g., each new short-lived channel will have its own handshake overhead).
Last yet not the slightest, channel-based security does not ensure the security of demand reaction once the application information escape the channel. This is most inconvenience some when the middle boxes (e.g., stores and intermediaries) are sent to reserve the application information. The asset proprietors need to trust the middle boxes to authorize the entrance control arrangements effectively, while the asset requestors need to trust the middle boxes to give credible information without altering.
The restrictions above feature the requirement for a different security display for IoT applications. An elective model that has been proposed at the IETF is object-based security, which anchors the application information unit specifically instead of the channel through which the information is transmit-ted. Every datum article should convey essential confirmation data (e.g., advanced marks) with the goal that anybody receiving the information can check its legitimacy paying little respect to how the information is recovered. At the point when information confidentiality is the worry, the originator of the information can scramble the substance so just the expected beneficiaries can decode the information. Comparable thoughts utilizing the article based security have additionally showed up outside the IoT territory, for example, the progressing e orts at the IETF jose WG to anchor JSON objects.
5. RETHINKING THE ARCHITECTURE
The well known standard of indirection says that \all issues in software engineering can be explained by another dimension of indirection". Yet, one issue it doesn't illuminate is the presence of such a large number of dimensions of indirection, which unequivocally portrays the circumstance of the current IoT arrange design.
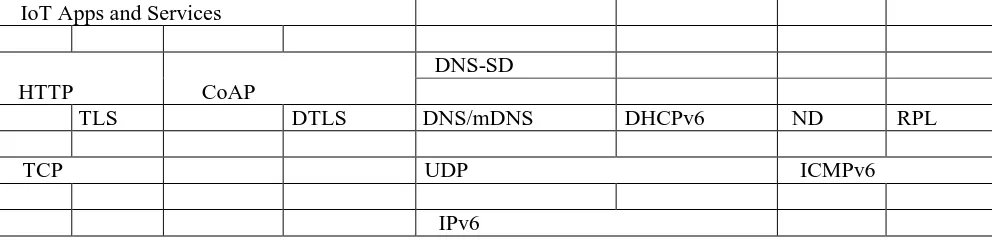
Figure 1 demonstrates the layered structure of an IP-based IoT stack. To help the REST interface, IoT applications ordinarily embrace CoAP or HTTP as the informing convention. Typically the applications additionally need to connect with regular administrations over the informing layer, (for example, the CoAP Re-source Directory and article security bolster). Ideal over the vehicle layer, TLS and DTLS are added to anchor the correspondence channel. What's more, there are numerous infrastructural administrations that are important to encourage the IP arrange correspondences, for example, ICMP, DHCP, Neighbor Discovery (ND), DNS and RPL.
the current stack reflects the profound established befuddle between the desires from the IoT applications and the design truth of TCP/IP.
IoT Apps and Services
HTTP CoAP
DNS-SD
TLS DTLS DNS/mDNS DHCPv6 ND RPL
TCP UDP ICMPv6
IPv6
Link Layer (Ethernet/WiFi/Bluetooth/802.15.4/…)
with optional adaptation sub-layer
Figure 1: A typical architecture for IoT systems
IOT Applications
Naming Config Discovery Sequencing Reliability
REST(CoAP/HTTP)
URI UR
Data Channel (TCP/UDP....)
Figure 2: An IoT stack from the application's perspective
The REST layer contains a few sub-modules that implement basic functionalities:
o a URI-based correspondence instrument that can de-liver application-layer information to arrange goals;
o a storing system for efficient information spread;
o an article security system for ensuring the integrity and confidentiality of individual ADUs;
o a blockage control module that may execute multiple calculations for different organize situations;
o naming configuration and asset disclosure for helping the application tasks;
o a sequencing system for slashing expansive information that can't t into a solitary ADU;
o an unwavering quality system that bolsters bundle retransmission and requesting as per the application's demand.
Right now each one of those functionalities (counting the REST interface itself) is executed by the application layer conventions. Nonetheless, a portion of those functionalities could have been more effective whenever moved into the center system. For ex-sufficient, the blockage control could benefit from the feed-backs of system and connection layers to settle on more astute choices. Reserving could be more efficient if the stores are pervasive inside the system, as opposed to depending on committed caching proxies. To use in-arrange reserving, URI-based forwarding, REST interface and item security ought to likewise be sup-ported at the system layer so the stored substance can be effortlessly found, recovered and confirmed. This protocol stacks improvement in the end lead to an easier and more efficient design that intently looks like the Information-Centric Network (ICN) vision.
The ICN designs, for example, NDN [16, 31] not just expert vide local help for the functionalities that IoT applications inherently request, yet additionally address the lower-layer organize difficulties. It applies the equivalent ADU crosswise over layers and gives the parcel flow control back to the applications. It doesn't have artificial necessities on least MTU; the simplified stack really decreases the extent of bundle headers. It is naturally multicast cordial since
URI Based
unavoidable reserving al-lows information to be reused by different buyers efficiently. Its information situated correspondence dodges the issue of tending to and steering to countless hubs and opens the open door for adaptable directing and sending over application layer names. The information driven security stays away from the overhead involved by the channel-based security solutions and better suits the IoT gadgets with restricted assets and discontinuous availability. The building straightforwardness prompts littler code estimate for the application programming, bring down vitality and memory impression for the gadget, and better utilization of the system asset contrasted with the present IP-based IoT stack. The possibilities of IoT over ICN have officially drawn consideration at the IRTF icnrg [32] and we expect it to wind up a functioning examination theme as the enthusiasm for the IoT innovations keeps on developing.
6. CONCLUSION:
At the point when the TCP/IP convention stack was rst created in the mid 1980s, the objective was to interface centralized server computers through the wired network. In spite of the fact that the convention stack continued advancing after the IP specification was distributed, the central supposition behind the engineering configuration has not changed. IoT systems speak to another sort of utilizations where the IP engineering can only with significant effort t in without significant modification to the convention stack.
In this paper, we talked about the difficulties of applying TCP/IP to IoT systems that emerge from the system and transport layers. We likewise talked about how the application layer conventions like CoAP give their very own answers for the ideal functionalities that the lower layers neglect to sup-port. The bungle was made increasingly obvious by contrasting the current IoT stack and the ideal design from the application's perspective. We proposed a structural change that moves the REST-related segments into the center system layer and in the end touched base at a more efficient engineering to the current application layer arrangements. This new IoT stack would grasp the ICN plan and actualize the required functionalities locally and more efficiently in-side the system.
REFERENCES:
1. BAC net - A Data Communication Protocol for Building Automation and Control Networks, Mar. 2013. 2. ZigBee IP Speci cation Revision 34. ZigBee Document 095023r34, Mar. 2014.
3. R. Barnes. Use Cases and Requirements for JSON Object Signing and Encryption (JOSE). RFC 7165 (Informational), Apr. 2014.
4. S. Cheshire and M. Krochmal. DNS-Based Service Discovery. RFC 6763 (Proposed Standard), Feb. 2013. 5. S. Cheshire and M. Krochmal. Multicast DNS. RFC 6762 (Proposed Standard), Feb. 2013.
6. D. D. Clark and D. L. Tennenhouse. Architectural Considerations for a New Generation of Protocols. SIGCOMM Comput. Commun. Rev., 20(4):200{208, Aug. 1990.
7. S. Deering and R. Hinden. Internet Protocol, Version 6 (IPv6) Speci cation. RFC 2460 (Draft Standard), Dec. 1998. Updated by RFCs 5095, 5722, 5871, 6437, 6564, 6935, 6946, 7045, 7112.