© 2017, IRJET | Impact Factor value: 5.181 | ISO 9001:2008 Certified Journal
| Page 215
AN EFFICIENT VLSI DESIGN OF AES CRYPTOGRAPHY BASED ON DNA
TRNG DESIGN
Vikas J
1, Sowmya Sunkara
21
MTech. in VLSI Design and Embedded Systems, BMSCE, Bangalore.
2
Asst. Professor, Dept. of ECE, BMSCE, Bangalore, Karnataka, India.
---***---Abstract -
This paper shows the design of AdvancedEncryption Standard (AES), focused on improving the security and reducing the area and delay. In AES-128 there will be 10 round of operations which requires 10 different set of keys that are generated using process called key expansion. The key expansion used is a manual process and also very complicated which occupies more area and delay. In embedded design, the speed and area are the major factors. The Key material which is used in cryptography is critical, the security of the entire framework will be dependent on it. Many recent attacks are made by learning the key patterns. So to improve the security and to optimize the design, in this approach, the round keys which are required for encryption process will be generated using Random Number Generation unit (TRNG). As a further advancement, DNA encoding is used along with the TRNG design. A partial key of fewer bits is generated from the TRNG block and given to DNA encoder which will produce the complete 128-bits of key required. This approach will further strengthen the security and optimizes our design with reduced area and delay. The proposed design is implemented using Verilog coding, simulated by ModelSim 6.4 c and Synthesized using Xilinx 13.2 IDE with Virtex 5 FPGA as the target device. A comparison table is made for the standard approach, TRNG based AES approach and TRNG and DNA based AES.
Key Words: AES-128, TRNG, DNA encoding, Post
processor, Pre-processor.
1. INTRODUCTION
In the current digital era securing the data generated and transmitted over the web via cryptography is vital. Cryptography, normally called encryption is a process where the user data is encrypted into an unreadable format so that it can be protected from unwanted users. The intended recipients can access or read the data by decrypting it with proper calculations and keys. The National Institute of Standards and Technology called NIST section of the US government in the year 1977 needed an alternative for DES abbreviated as Data Encryption Standard which were then prone to attacks and also because of advances in processing power of the systems. Among many algorithms proposed and reviewed Joan Daemen and Vincent Rijmen, Belgium cryptographer’s algorithm was chosen and named it as Rijndael algorithm. Later in the year 2000, it was formally adopted with the name Advanced Encryption Standard (AES)
and was published as FIPS-197 under the federal standards [1].
AES operation uses symmetric key which implies that it will use the key that is same for both encryption and decryption process. There is flexibility in this algorithm to choose the size of input and key size among 128, 192 or 256-bit. In AES we keep the 128 bit as fixed size of input block while varying the size of key among 128, 192 or 256-bits. AES-128 name for the algorithm with 128 bit key, similarly 192 and AES-256 are the standard names used [1].
1.1 AES Algorithm
In the AES implementation, the 128-bits of input will be made into a group of 16 bytes block. The arrangement of the blocks will be in a matrix form consisting of four rows and columns. AES will do the calculations on these bytes of data instead on bits. For encrypting a block of data the number of rounds or iterations are not fixed as in DES, it relies on size of the key used. AES with 128-bit key uses 10 rounds, for key size of 192-bits 12 rounds, 14 rounds for AES with key of 256-bits [1]. Every iteration during encryption gets a new set of keys called round keys which is calculated using the initial given key and previous generated key as we go on. Here “rounds” imply that the AES algorithm will perform the mixing of input data re-encrypting it 10 to 14 times on the basis of key size. The process of decryption is simply an inverse of encryption process, all the steps which are done for encryption process is done in reverse order to decrypt the cipher data. The final round inversion is done first then the nine main rounds inversion and then the initial round inversion.
In the AES algorithm, the first round of operation is the Add round key where the input plain text block is XORed with the given cipher key. Then we have nine main rounds of calculations which have four stages in each round and the final round will have only three stages, this is same for decryption also, but it will just be the inverse operation of encryption. The 4 stages of operation are:
© 2017, IRJET | Impact Factor value: 5.181 | ISO 9001:2008 Certified Journal
| Page 216
For the nth final round Mix column operation is not done [1].Fig -1: AES Encryption Process
2. TRULY RANDOM NUMBER GENERATOR
Random Number Generators are computational devices or physical device that will generate a series of numbers which will not have any dependencies or a visual patterns, such a series of numbers can be considered as random numbers. Such capacities might be portrayed as "True Random Number Generators” (TRNGs). Random numbers frame an essential piece of most security frameworks. Their most evident utilization is in the era of cryptographic keys for information encryption, the key which are generated here cannot be guessed or calculated even when we can get the previous keys or part of the key also - the more arbitrary the key, the more secure the framework. This is an ideal application for a fantastic TRNG. There are two stages which the RNG’s include, a True Random Number generator that creates the entropy, and cryptographic post-handling, used to get a specific level of security even on account of an undetected disappointment of the basic TRNG.
Fig -2: Random Number generator Block
Here a pre-scalers is made use of to implement the oscillator required to get clock pulses of different frequencies in the pre-processor stage. A 4/5 pre scaler is used to get two different clock pulses. A mode control bit MC controls the output depending on its value.
Fig -3: 4/5 Pre scaler circuit
In the preprocessor block the two outputs from the pre scalers are xored and inverted and given as a seed to the sampler which is a D-Flip flop. The output of this is given to a post processor as a clock which implements a LFSR circuit to increase the randomness of the output [3].
The TRNG includes random seed generator pre block and a post processor producing the final output. An important function of the post-digital processor is to give robustness of the statistical properties of the TRNG output sequence. The post digital processor is realized by 128-bit Linear Feedback Shift Register (LFSR) [3].
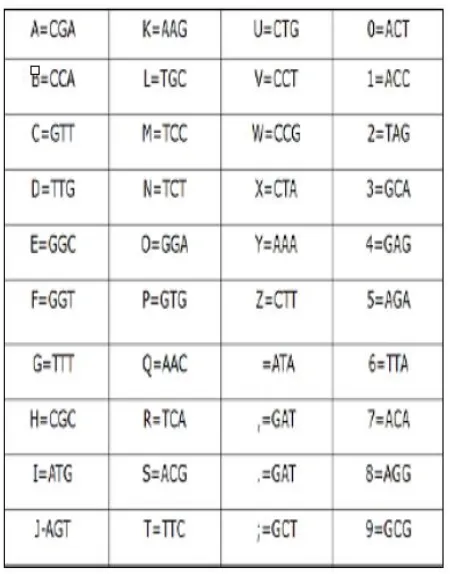
3. DNA ENCODING
DNA cryptography is one of the fast improving innovation which takes a shot at ideas of DNA processing. Another procedure for securing data was shown utilizing the cellular structure of DNA called DNA Computing. DNA can be utilized to store and transmit information. The idea of utilizing DNA computation in the fields of cryptography has been distinguished as a conceivable innovation that may present another desire for unbreakable algorithms.
DNA Strands are long polymers of a million number of connected nucleotides. These nucleotides comprise of one of four nitrogen bases, a five carbon sugar and a phosphate gathering. The nucleotides which make up these polymers are named after the nitrogen base that it comprises of; ACGT Adenine, Cytosine, Guanine, and Thymine [11].
[image:2.595.42.281.119.297.2] [image:2.595.41.278.570.668.2]© 2017, IRJET | Impact Factor value: 5.181 | ISO 9001:2008 Certified Journal
| Page 217
Fig -4: DNA Encoding Table4. PROPOSED WORK
[image:3.595.48.273.104.391.2]The design of a truly random number generator (TRNG) macro-cell to get the random keys of 128 bits, suitable to be integrated into AES Cryptographer, is done. The round keys are generated using this block instead of the Key Expansion process. The round keys obtained from the TRNG block will be stored in memory simultaneously performing the Encryption and decryption
Fig -5: TRNG based AES Design
The complex process of the key expansion which include sub-byte, word rotation and Xor with R-Con is replaced with simple, efficient TRNG block. This proposed design will increase the security level as the key process will be fully random without any relation between the keys generated. The area and delay of the proposed system will be reduced.
[image:3.595.319.550.329.483.2]Another approach proposed is to generate the round keys with the help of TRNG block and DNA encoding. In this approach to make sure that the keys obtained are fully random and impossible to guess we make use of the DNA encoding. Here we generate only partial bits from the TRNG block since the DNA encoding will produce triplet code for each input. The required 128 bits of key can be obtained by just giving 24 bits of input to DNA encoding. So the TRNG block can be made smaller for just producing 24 bits of output. This will further reduce the area and delay of the entire system.
Fig -6: TRNG and DNA based AES Design
5. SIMULATION RESULTS
The system is designed in Verilog and simulated using ModelSim 6.4 c, various simulation outputs are shown below.
[image:3.595.69.272.551.720.2]© 2017, IRJET | Impact Factor value: 5.181 | ISO 9001:2008 Certified Journal
| Page 218
Fig -8: TRNG Block outputFig -9: TRNG based AES
Fig -10: DNA Code Block
Fig -11: TRNG and DNA based AES
6. SYNTHESIS RESULTS
The design is synthesized by Xilinx tool 13.2 IDE with Virtex 5 XC5vlx110t-1ff1136 FPGA as the target device.
[image:4.595.309.555.255.388.2]
Fig -12: RTL Schematic of Top Module Design
[image:4.595.310.556.420.579.2]Fig -13: RTL Schematic of Inner Modules
Fig -14: Device utilization summary of TRG based AES
[image:4.595.309.556.615.752.2]© 2017, IRJET | Impact Factor value: 5.181 | ISO 9001:2008 Certified Journal
| Page 219
Fig -16: Device utilization summary of TRNG and DNAbased AES
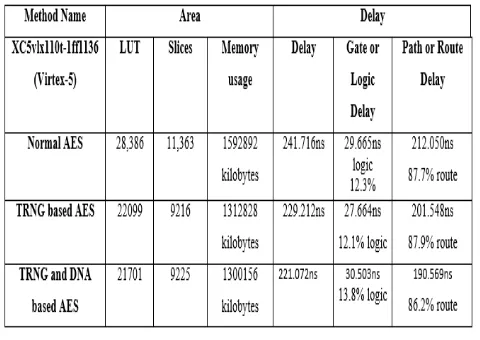
Fig -17: Comparision Results
6. CONCLUSION
The design of AES with TRNG which is used for generation of the round keys required for encryption and decryption process, also DNA based TRNG module is implemented to increase the security level further is implemented. The Implementation is based on mathematical properties of Rijndael algorithm where the key expansion part relies on DNA Coder and TRNG. Encryption Design using Shit rows, Mixed Column, Add Round Key is done, and Design of Decryption Part is also done. Genetic Algorithm based Encoding for Key Generation is used for Encryption and Decryption Process. The new design permits the construction of efficient area and speed characteristics, while still keeping a very high protection level. We conducted relevant AES Implementation with DNA TRNG for Key Generation Method. With this novel approach of generating the random keys which is purely random and cannot be guessed and also the key entry process will no
longer be a manual process. All the set of 128-bit keys required will be generated randomly. The level of security against various attacks will be increased using this method. Also, from the comparison table we can see that the area and the delay when compared to the conventional AES implementation has been reduced. The design has an enormous scope of improvement; the TRNG block can be implemented using various other methods. A true source of randomness can be added also there are a variety of true sources of randomness are available and which may help in further optimizing the design.
REFERENCES
[1] Announcing the Advacned Encryption Standard (AES), Federal Information processing Standards Publication 197,http://nvlpubs.nist.gov/nistpubs/FIPS/NIST.FIPS.1 97.pdf.
[2] Practical Implementation of Rijndael S-Box Using Combinational Logic, Edwin NC Mui Custom R & D EngineerTexcoEnterprisePtd.Ltd.http://www.xess.com/ static/media/projects/Rijndael_SBox.pdf.
[3] Liu Dongsheng, Liu Zilong, Li Lun*, Zou Xuecheng “A Low-Cost Low-Power Ring Oscillator-Based Truly Random Number Generator for Encryption on Smart Cards”, IEEE Transactions on Circuits and Systems II: Express Briefs (Volume: 63, Issue: 6, June 2016) [4] Apostol Vassilev,Timothy A. Hall, “The Importance of
Entropy to Information Security”, IEEE COMPSAC 2014. [5] Differential powerAnalysis: A serious threat for FPGA security, M. Masoumi, Int. J. Internet Technol. Secured Trans., vol. 4, no. 1, pp. 12–25, 2012.
[6] Naveen Jarold K, “Hardware Implementation of DNA Based Cryptography”,Proceedings of 2013 IEEE Conference on Information and Communication Technologies (ICT 2013).
[7] https://en.wikipedia.org/wiki/Affine_transformaton [8] https://en.wikipedia.org/wiki/Cryptography [9]
https://www.designreuse.com/articles/27050/true-randomness-in-cryptography.html
[10] http://securityaffairs.co/wordpress/33879/security/d na-cryptography.html
[image:5.595.41.281.343.513.2]