International Journal of Research (IJR)
e-ISSN: 2348-6848, p- ISSN: 2348-795X Volume 2, Issue 09, September 2015Available at http://internationaljournalofresearch.org
A New Way of Data Security using image coordinates as
Password in AI
Subburu Mamatha
1& Dr. Shaik Abdul Muzeer
21M-Tech Dept. Of CSE Megha Institute of Engineering & Technology for Women
2Professor & principal Dept. Of CSE Megha Institute of Engineering & Technology for Women
Abstract
In this paper we conduct a comprehensive survey of subsisting CaRP techniques namely ClickText, ClickAnimal and AnimalGrid. We discuss the strengths and inhibitions of each method and point out research direction in this area. We withal endeavor to answer “Are CaRP as secured as graphical passwords and text predicated passwords?” and “Is CARP protective to relay attack?"Texts passwords are insecure for reasons and graphical are more secured in comparison but are vulnerably susceptible to shoulder surfing attacks. Hence by utilizing graphical password system and CAPTCHA technology an incipient security primitive is proposed. We call it as CAPTCHA as Graphical Password (CaRP). CaRP is an amalgamation of both a CAPTCHA and a graphical password scheme. Cyber security is a consequential issue to tackle. Sundry utilizer authentication methods are utilized for this purport. It avails to evade misuse or illicit utilization of highly sensitive data. Text and graphical passwords are mainly utilized for authentication purport. But due to sundry imperfections, they are not reliable for data security.
Keywords: Text passwords; Cyber security; CAPTCHA technology; Graphical passwords; CaRP
1.
Introduction
The notion of CaRP is simple but generic. CaRP can have multiple instantiations. In theory, any Catha scheme relying on multiple-object relegation can be converted to a CaRP scheme. We present exemplary CaRPs built on both text Captcha and image-apperception Captcha. One of them is a text CaRP wherein a password is a sequence of characters like a text password, but entered by clicking the right character sequence on CaRP images.
The discrete logarithm quandary is fundamental to the ElGamal encryption, the DiffieHellman key exchange, the Digital Signature Algorithm, the elliptic curve cryptography and so on. Utilizing hard AI (Artificial Astuteness) quandaries for security, initially proposed, is an exhilarating incipient paradigm. Under this paradigm, the most eminent primitive invented is Captcha, which distinguishes human users from computers by presenting a challenge, i.e., a
International Journal of Research (IJR)
e-ISSN: 2348-6848, p- ISSN: 2348-795X Volume 2, Issue 09, September 2015Available at http://internationaljournalofresearch.org
systems integrating Captcha technology, which we call CaRP (Captcha as gRaphical Passwords). CaRP is click-predicated graphical passwords, where a sequence of clicks on an image is utilized to derive a password. Unlike other click-predicated graphical passwords, images utilized in CaRP are Captcha challenges, and an incipient CaRP image is engendered for every authenticate endeavor.
CaRP offers auspice against online dictionary attacks on passwords, which have been for long time a major security threat for sundry online accommodations. This threat is widespread and considered as a top cyber security peril. Bulwark against online dictionary attacks is a more subtle quandary than it might appear. Intuitive countermeasures such as throttling authenticate on endeavors do not work well for two reasons: 1) It causes denial-of-serviceattacks (which were exploited to lock highest bidders out in final minutes of eBay auctions) and incurs extravagant helpdesk costs for account reactivation.
2) It is vulnerably susceptible to ecumenical password attacks whereby adversaries intend to break into any account rather than a concrete one, and thus endeavor each password candidate on multiple accounts and ascertain that the number of tribulations on each account is below the threshold to eschew triggering account lockout.
CaRP withal offers aegis against relay attacks, an incrementing threat to bypass Captchas bulwark, wherein Captcha challenges are relayed to humans to solve. Koobface was a relay attack to bypass Facebook’s Captcha in engendering incipient accounts. CaRP is robust to shoulder-surfing attacks if cumulated with dual-view technologies.
2.
Related Work
Graphical Password was pristinely defined by
Blonder (1996).In graphical passwords
techniques are relegated into two main categories: apperception-predicated and recall
predicated graphical techniques. In Apperception predicated techniques, a utilizer is presented with a set of images and the utilizer passes the authentication by apperceiving and identifying the images he culled during the registration stage. In recall predicated graphical password, a utilizer is asked to reproduce something that he/she engendered or culled earlier during registration phase [5].Existing System is predicated on apperception techniques in that A. Click Text and Animal Grid two method introduce. A. Click Text In this method 33 Capital Letters except I, J, O, and Z digits except 0 and 1, and three special characters #,@,and &.The last three characters is utilized to balance the security. Characters were arranged in 5 rows. Each character was desultorily rotate from -30 degree to 30 degree and scaled from 60% to 120%.Neighboring characters could overlap up to 3 pixels [1].
Fig 1: Click Text image with 20 characters. 2.1 Animal Grid:
In this method 10 animals used:
International Journal of Research (IJR)
e-ISSN: 2348-6848, p- ISSN: 2348-795X Volume 2, Issue 09, September 2015Available at http://internationaljournalofresearch.org
Fig 2: Click Animal images (left) and 6x6 grid (right).
The main disadvantage of above two methods is incrementing load on system. Click text letters overlap with each other so it is time consuming sometimes during authenticate process. In Animal grid 3d model is utilized and size of each animal is more minuscule. It does not bulwark from shoulder surfing attack. There is no theoretical model for this System.
2.2 Proposed System:
Our system is predicated on Apperception Technique. In this three different group of image is utilized in that 1.Famous Places 2. Famous People 3.Reputed Company Designation. Each group contains 25 images. Utilizer has to cull at least one image from each group during registration phase. During authenticate time utilizer has to click on that images which is culled during registration phase. This system provide auspice against shoulder surfing attack, dictionary attack, brute force attack utilizing text password as well as graphical password.
Fig 3: Architecture Diagram of System.
3.
Implementation
3.1 Graphical Password:
In this module, Users are having authentication and security to access the detail which is presented in the Image system. Afore accessing or probing the details utilizer should have the account in that otherwise they should register first.
3.2 Captcha in Authentication:
In this module we utilize both Captcha and password in a utilizer authentication protocol, which we call Captcha-predicated Password Authentication (CbPA) protocol, to contravene online dictionary attacks. The CbPA-protocol in requires solving a Captcha challenge after inputting a valid pair of utilizer ID and password unless a valid browser cookie is received. For an invalid pair of utilizer ID and password, the utilizer has a certain probability to solve a Captcha challenge afore being gainsaid access.
3.3 Surmounting Thwart Conjecturing
Attacks:
International Journal of Research (IJR)
e-ISSN: 2348-6848, p- ISSN: 2348-795X Volume 2, Issue 09, September 2015Available at http://internationaljournalofresearch.org
3.4 Security of Underlying Captcha:
Computational intractability in apperceiving objects in CaRP images is fundamental to CaRP. Subsisting analyses on Captcha security were mostly case by case or utilized an approximate process. No theoretic security model has been established yet. Object segmentation is considered as a computationally extravagant, combinatorially-conundrum, which modern text Captcha schemes rely on.
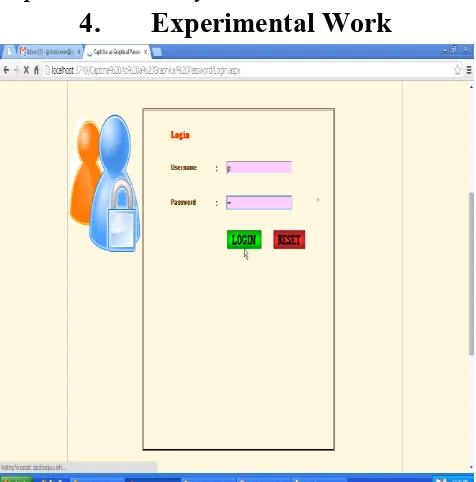
4.
Experimental Work
Fig 4: User Authenticated based on textual password.
Fig 5: User select coordinates before uploading.
Fig 6: Coordinates match data will download.
5.
Conclusion
We have suggested CaRP, an incipient security primitive depend on unsolved hard AI quandaries.A password of CaRP can be found only probabilistically by automatic online conjecturing attacks including bruteforce attacks, a culled security property that other graphical password arrangements lack.Hotspots in CaRP images can no longer be exploited to fortify automatic authentic time presaging attacks. Overall, our work is one step forward in the paradigm of utilizing hard AI quandaries for security. Of authentic security and usability and practical ameliorations, CaRP has good potential for modifications, which call for subsidiary future work.More importantly, we cerebrate CaRP to motivate incipient revelations of such AI predicated security primitives.
6. References
[1] R. Biddle, S. Chiasson, and P. C. van Oorschot,“Graphical passwords:Learning from
the first twelveyears,” ACM Comput. Surveys,
vol. 44,no. 4, 2012.
[2] (2012, Feb.). The Science
International Journal of Research (IJR)
e-ISSN: 2348-6848, p- ISSN: 2348-795X Volume 2, Issue 09, September 2015Available at http://internationaljournalofresearch.org
[3] I. Jermyn, A. Mayer, F. Monrose, M. Reiter, andA. Rubin, “The design and analysis of
graphical passwords,” in Proc. 8th USENIX
SecuritySymp.,1999, pp. 1–15.
[4] Liming Wang, Xiuling Chang, ZhongjieRen,
HaichangGao, XiyangLiu, UweAickelin,
“Against Spyware Using CAPTCHA in GraphicalPassword Scheme”
[5] Luis von Ahn, Manuel Blum, Nicholas J. Hopper, and John Langford,“CAPTCHA: Using Hard AI Problems For Security”
[6] XiaoyuanSuo, Ying Zhu, G. Scott. Owen, “Graphical Passwords: ASurvey”, Department of Computer Science Georgia State University
[7] S. Wiedenbeck, J. Waters, J. C. Birget, A. Brodskiy, and N.Memon, “PassPoints: Design and longitudinal evaluation of agraphical password system,” Int. J. HCI, vol. 63, pp. 102– 127,Jul. 2005.
[8] http://www.realuser.com
Author Profile
Dr.Shaik Abdul Muzeer
Professor & Principal
Megha institute of Engineering & Technology for
Women
Dr.S.A.Muzeer, at present working as a principal of
Megha institute of engineering & Technology has
completed his PG and P.HD in Electronics &
Communication Engineering and published
around 25 Papers in National & International
Journals. His area of research is Digital signal