Volume-7 Issue-2
International Journal of Intellectual Advancements
and Research in Engineering Computations
Secure Data Sharing and Verification in Public Clouds
Mrs.K.Kavitha
1, S.Meenalosini
2, J.Akshaya
2, S.Kavitha
2, P.Loganathan
21
Assistant Professor Department of Computer Science Engineering ,Nandha Engineering College
2UG-Students, Department of Computer Science Engineering ,Nandha Engineering College
ABSTRACT
In our front line and age, numerous endeavours are getting a handle on appropriated registering. In any case, one of the genuine worries regarding circulated processing has reliably been security. Encryption in cloud is still in a state of transition and beginning times. A couple of shippers give encryption, while others don't. There are different sorts of encryption gets ready for verifying data in the cloud, every so often organized inside a structure. At whatever point an association picks it move its applications to the cloud, it thinks about a couple of preferences and burdens before doing all things considered. In existing, Multi keyword Ranked Search(MRSE) without using coordinating tasks deals with the key escrow issue in character based encryption and confirmation disavowal issue visible to everyone scratch cryptography. This work upgrades the profitability of encryption at the data owner. In any case, It has Certificate less encryption. So data owner can't affirm the move record status in cloud. To deal with this present issue, we proposed An Efficient Certificate less Encryption with HmacSHA1 signature for Secure Data Sharing and check in Public Clouds. We execute our proposed contrive and the general cloud based structure, and survey its security and execution.
Keywords:
Cloud computing, Certificate less encryption, Multi key word search algorithm.INTRODUCTION
Distributed computing has changed the manner in which affiliations approach IT, engaging them to twist up unmistakably progressively capable, present new plans of activity, give more organizations, and abatement IT costs. Circulated registering progressions can be completed in a wide combination of structures, under different organization and course of action models, and can exist together with various advances and programming setup approaches. Data confirmation bests the summary of cloud concerns today. With respect to open private, and mutt cloud game plans, the probability of exchanged off information makes tremendous nervousness.
Affiliations envision that outcast providers will manage the cloud establishment, yet are much of the time uneasy about giving them detectable quality into tricky data. Guaranteeing your data in the cloud is done by executed to get the
opportunity to control records to portray the assents. Associated with the data objects. Limit encryption to guarantee against unapproved access at the server ranch (especially by vindictive IT staff).
Hardening of the servers to verify against known, and cloud, vulnerabilities in the working system and programming. Physical security to guarantee against unapproved physical
access to data. Due to the upsides of open dispersed capacity, affiliations have been getting open cloud organizations, for instance, Microsoft Skydrive and Dropbox to manage their data.
methodology is to encode the data before exchanging it to the cloud. Since the cloud does not know the keys used to scramble the data, the grouping of the data from the cloud is ensured. Nevertheless, a similar number of affiliations are required to maintain fine-grained get the chance to control to the data, the encryption framework should moreover have the ability to reinforce fine-grained encryption based get the opportunity to control.
An ordinary methodology used to reinforce fine-grained encryption based get the opportunity to control is to scramble assorted courses of action of data things to which a comparable get the chance to control technique applies with different symmetric keys and give customers either the relevant keys or the ability to decide the keys. Regardless of the way that the key enlistment based philosophies decline the amount of keys to be administered, symmetric key based frameworks when in doubt have the issue of high costs for key organization. With a particular ultimate objective to decrease the overhead of key organization, a choice is to use an open key cryptosystem.
Disregarding the way that their arrangement relies upon CL-PKC to deal with the key escrow issue and confirmation organization, it relies upon mixing tasks. Despite late advances in execution methods, the computational costs required for coordinating are still fundamentally high stood out from the costs of standard activities, for instance, estimated exponentiation in constrained fields. Moreover, their arrangement just achieves Chosen Plaintext Attack (CPA) security.
The security center individual goes about as a plan prerequisite point as well and reinforces quick revocation of exchanged off or malicious customers. What's more, appeared differently in relation to symmetric key based instruments, our methodology can adequately manage keys and customer refusals. In symmetric key structures, customers are required to manage different keys identical to in any occasion the logarithm of the amount of customers, while in our methodology, each customer simply needs to keep up its open/private key match.
It is basic to see that in case one explicitly applies our crucial MRSE plan to circulated processing and if various customers are endorsed to get to comparable data, the encryption costs at the data owner can end up being high. In such case, the data owner needs to encode comparative data encryption key distinctive conditions, once for each customer,
using the customers' open keys.. Our increased MRSE scheme requires the data owner to encode the data encryption key just once and to give some additional information to the cloud with the goal that affirmed customers can unravel the substance using their private keys.
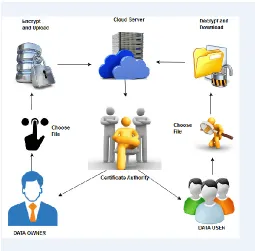
Fig 1. Cloud Computing Architecture
Related work Security Mediated CL-PKE
In 2003, Al-Riyami and Paterson introduced a Certificateless Public Key Cryptography (CL-PKC). Since each customer holds a blend of KGC conveyed partial private key and an additional customer picked riddle, the key escrow issue can be settled.
Since the presence of PKC [2], various CL-PKE designs have been proposed in perspective on bilinear pairings.
The computational cost required for coordinating is still widely high appeared differently in relation to standard tasks, for example, estimated exponentiation in restricted fields. To improve capability, Sun et al. presented a solidly secure CL-PKE without mixing activities. In any case, past CL-PKE designs couldn't deal with the key repudiation issue. In open key cryptography, we should consider circumstances where some private keys are bartered. In case the private keys are dealt, at that point it is never again secure to use the contrasting open keys
The crucial thought of the intervened cryptography is to utilize a security go between (SEM) which can control security capacities with regards to each trade. When the SEM is informed that a customer's open key should be disavowed, it can speedily stop the customer's help in a trade.
Functional Encryption
Useful encryption licenses one to encode an abstract complex get the opportunity to control approach with the encoded message. The message would then be able to be unscrambled just by the customers satisfying the encoded methodology. In predicate encryption with open rundown, the system under which the encryption is performed is open.
Not in the slightest degree like open key cryptosystems, the open key isn't a self-assertive string but instead some uninhibitedly known qualities, for instance, ID that difficulty to customers. Trademark based encryption (ABE) exhibited by Sahai and Waters is an increasingly expressive predicate encryption with an open record. It very well may be considered as a hypothesis of IBE. In ABE, individuals when all is said in done keys of a customer are depicted by a course of action of identity properties the customer has.
some critical disservices. At whatever point the social event dynamic changes, the rekeying activity requires to overhaul the private keys given to existing people remembering the ultimate objective to give backward/forward secret. Help, the ABE plan encounters the key escrow issue. Predicate encryption designs without open rundown, for instance, Anonymous IBE , Hidden Vector Encryption and Inner thing predicate shield the security of the get the opportunity to control procedures. Regardless of the way that they ensure the security of the methodology, they have limited expressibility appeared differently in relation to the past plans moreover experience the evil impacts of a vague requirements from the past plans.
Symmetric Key Based Systems
In push-based systems data things are encoded with different keys, which are given to customers at the beginning. The mixed data is then imparted to all customers. In any case, such philosophies necessitate that all or some keys be appropriated early in the midst of customer selection arrange. This need makes it difficult to ensure forward likewise, in invert key puzzle when customer get-togethers are dynamic then again the ACPS change. Advance, the rekey methodology isn't clear, as such moving the heaviness of increasing new keys to customers. Shang et al. proposed an approach to manage disentangle such issue. It builds up the structure to make rekey clear to customers and secure the insurance of the customers who get to the substance.
Secure Cloud Storage
Some late research attempts [have been proposed to create security protecting access control systems by joining incognizant trade and puzzling capabilities. The goal of such work resembles our very own yet we recognize thegoing with imperatives. Each trade tradition licenses one to get to only a solitary record from the database, while our methodology does
not have any requirement on the amount of records that can be gotten to immediately since we segregate the get the chance to control from the endorsement.
Thusly CPA is too much delicate to be seen as appropriate for certifiable applications.
In show up diversely in connection to Lei et al's. plan, our proposed contrive achieves CCA (Chosen Cipher content Attack) security. Under CCA, the limit of an enemy is more successful than the limit of the adversary under CPA. Despite the open key, the adversary under CCA is offered access to an "unscrambling prophet" which disentangles emotional figure writings at the foe's interest, giving back the plaintext. Also, our.
PROPOSED ALGORITHM
Cloud Set Up
The KGC in the cloud runs the SetUp task of the MRSE scheme and creates the expert key MK and the structure parameters params. It should be seen that this setup task is a one-time task.
User / Client Registration
Every customer first delivers its very own private and open key match, called SK and PK, using the SetPrivateKey and SetPublicKey activities independently using our MRSE plot. The customer at that point sends its open keys and its character (ID) to the KGC in the cloud. The KGC along these lines produces two midway keys and an open key for the customer. One deficient key, suggested as SEM-key, is secured at the SEM in the cloud.
The open key, implied as KGC-key, contains the customer made open key and likewise the KGC delivered open key. The KGC-key is used to scramble data. The SEMkey, U-key, and SK are used together to decipher mixed data. We imply the mostly private key and individuals by and large key for useri as SEM-keyi, U-keyi, KGC-keyi exclusively.
Information encryption and transferring:
customers. The mixed data close by the get the opportunity to control summary
is exchanged to the cloud. The encoded substance is secured in the limit advantage in the cloud and the get the chance to control list, set apart by the data owner, is secured in the SEM in the cloud.
Data / Information Retrieval and Decryption:
At the point when a customer needs to examine a couple of data, it sends an interest to the SEM to get the not entirely decoded data. The SEM first checks if the customer is in the get the chance to control list and if the customer's KGC-key mixed substance is open in the appropriated stockpiling.
In the event that the check is compelling, the SEM recuperates
the encoded substance from the cloud and not entirely unscrambles the substance using the SEM-key for the customer.
The customer uses its SK and U-key to totally unravel the data. To upgrade the adequacy of the system, when the fundamental fragmentary unscrambling for each customer is
played out, the SEM stores back the to some extent decoded data in the circulated stockpiling. On the off chance that a customer is disavowed, the data owner updates the get the opportunity to control list at the SEM with the objective that future get to requests by the customer are denied.
Fig 2.Data Encryption and Decryption
PSEUDO CODE
Encrypt
Alongside C1 = gr, where r is prepared as in the second step of Encrypt activity of the basic MRSE plot, the data owner figures the transitional key INT -Keyi for each
Client Decrypt
A useri having INT-Keyi (= grzozi) can enlist UOr using its private key, zi, as takes after and play out the unscrambling using this regard and individuals by and large key of the data owner. (grzozi)1/zi =
UOr. See that the learning of UOr licenses useri to disentangle the message mixed using the data owner's open key after the methods in the UserDecrypt activity in the essential MRSE plan
SIMULATION RESULT
Fig3. Performance comparison
For execution measure we analyze the computational overhead that is consolidated in transferring and after that honesty checking. Figure 3 demonstrates that for checking uprightness less time is required when contrasted with that of transferring consequently our proposed framework enables clients to check for information trustworthiness without downloading subsequently sparing parcel of assets as yet giving client status of archive effectively.
CONCLUSION AND FUTURE WORK
In this paper we have proposed the An Efficient Certificateless Encryption with HmacSHA1 signature for Secure Data Sharing and affirmation in Public Clouds. Our MRSE deals with the key
REFERENCES
[1]. M. Abdalla et al., “Searchable encryption revisited: Consistency properties, relation to anonymous be, and extensions,” J. Cryptol., 21(3), 2008, 350–391.
[2]. S. Al-Riyami and K. Paterson, “Certificateless public key cryptogr aphy,” in Proc. ASIACRYPT,C.-S. Laih, Ed. Berlin, Germany: Springer, LNCS 2894, 2003, 452–473.
[3]. M.Bellare, A. Desai, D. Pointcheval, and P. Rogaway, “Relations among notions of security for public-key encryption schemes,” in Proc. Crypto ’98, H. Krawczyk Ed. Springer-Verlag, LNCS 1462.
[4]. E.Bertino and E. Ferrari. “Secure and selective dissemination of XML documents,” ACM TISSEC, 5(3), 2002, 290–331.
[5]. J.Bethencourt, A. Sahai, and B. Waters, “Ciphertext-policy attribute-based encryption,” in Proc. IEEE Symp. SP, Taormina, Italy, 2007, 321– 334.
[6]. D.Boneh, X. Ding, and G. Tsudik, “Fine-grained control of security capabilities,” ACM Trans. Internet Technol., 4(1), 2004, 60–82.
[7]. D.Boneh and B. Waters, “Conjunctive, subset, and range queries on encrypted data,” in Proc. 4th TCC, Amsterdam, The Netherlands, 2007, 535– 554.
[8]. J.Camenisch, M. Dubovitskaya, and G. Neven, “Oblivious transfer with access control,” in Proc. 16th ACM Conf. CCS, New York, NY, USA, 2009, 131–140.
[9]. S. S. M. Chow, C. Boyd, and J. M. G. Nieto, “Security mediated Certificateless cryptography,” in Proc. 9th Int. Conf. Theory Practice PKC, New York, NY, USA, 2006, 508– 524.
[10]. S.Coull, M. Green, and S. Hohenberger, “Controlling access to an oblivious database using stateful anonymous credentials,” in Irvine: Proc. 12th Int. Conf. Practice and Theory in PKC, Chicago, IL, USA, 2009, 501–520.