Quality of Service Management for Service
Oriented Applications in a Cloud Architecture
Mohamed-K Hussein
Mohamed-H Mousa
Faculty of Computers and Informatics, Suez Canal University, Ismailia, Egypt
Abstract -- The cloud computing technology proliferate the IT infrastructures with plethora of services ranging from software services to hardware services. The service oriented application is based on the composition of a set of aggregated web services offered by the cloud as Software as a Services (SaaS). The SaaS provider requires the cloud hardware services, known as the Infrastructure as a Service (IaaS), to host the SaaS. The SaaS provider is either using internal data centers as private IaaS infrastructure or rented from a public IaaS provider. The shared computing resources of the public IaaS provider impact the Quality of Services (QoSs) of the web services, such as response time, which are defined in the Service Level Agreement (SLA). The SLA management of aggregated set of web services is a non-trivial and a challenging problem, called Service Consolidation Problem (SCP).
In this paper, an efficient service consolidation algorithm is proposed for SLA management in a cloud environment. The proposed algorithm is a scheduling algorithm for the SaaS provider which aims to: (1) reduce the cost of the SaaS provider resulting from renting computing resources from public IaaS provider by effectively utilizing the number of the initiated virtual machines, (2) minimize the response time of web services by effectively mapping the web services to the required virtual machines which do not violate the SLA. Extensive evaluations is conducted on the CloudSim simulation using various configurations, scales and workloads. Further, empirical comparisons with various algorithms from the literature are performed to prove the effectiveness and robustness of the proposed algorithm. Simulation results show that the proposed algorithm outperform the reference algorithms, up to 15% improvement.
Keywords: Cloud computing, Service Oriented Architecture, Web services, service aggregation, Software as a Service, Infrastructure as a Service.
I. INTRODUCTION
Web service is a web-based software which is available over the internet. The web services uses
standard protocols, including XML, Web Service Definition Language (WSDL) for service description, Simple Object Access Protocol (SOAP) for intercommunication, and Universal Description Discovery and Integration (UDDI), for publishing, describing, describing and executing a distributed, abstracted loosely coupled software functionality [1, 2].
Service Oriented Computing is a popular paradigm to develop complex distributed Service Oriented Applications (SOA) which are designed and composed from a different web services. This is an outstanding engineering approach to develop a reliable complex business application by loosely coupling a number of distinct, diverse and replicable web services which advertised, discovered and accessed over the internet. Representational state transfer (REST) is a popular lightweight protocol for building distributed applications from disparate web services using JSON, a lightweight data interchange format protocol [3]. Service oriented computing enables complex distributed SOA design based on two well-known design patterns, namely service composition and service aggregation. Service composition deals with developing a complex SOA functionality which is based on the composition of a number of web services. The business functionally workflow depends on the order of the web service composition. On the other hand, Service aggregation deals with bundled services which do not necessarily depend on each other.
related costs such as software licensee, upgrade, or infrastructure. The Infrastructure as a Service (IaaS) cloud provides the VMs images and dispatches the images to run on the physical resources in order to create the instances required by the SaaS provider.
The SaaS provider is either using internal data centers as private IaaS infrastructure or rented from a public IaaS provider in order to save the cost of the hardware infrastructure, maintenance and administration. However, the shared computing resources of the public IaaS provider impact the Quality of Services (QoSs) of the accessed web services, such as performance, which are defined in the Service Level Agreement (SLA). The Service Level Agreement (SLA) is a contract between the service provider and the service consumer where both providers and consumers have to comply with the specified constrains. SLA management of aggregated set of web services is a non-trivial and a challenging problem, called Service Consolidation Problem (SCP). SLA formally defines functional properties and the non-functional properties of the aggregated web service. Functional properties describe the business operations of the service, the service access description, and the supported protocols. The Non-functional properties deal with the Quality of Services (QoSs) properties such as availability, reliability, and performance [5, 6]. Contracts can be set statically or dynamically created as a result of a negotiation process between the provider and the consumer. Several research papers proposed automated SLA negotiation mechanisms [7]. SLA negotiation is not considered in this paper. This research only considers the QoSs management for a set of aggregated web services on a set of virtual resources given a static SLA between the provider and the consumers.
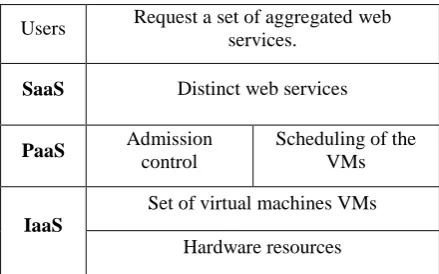
The general model of the distributed SOA applications on the cloud, as described in [4, 8], consists of three layers, as shown in Figure 1. The first layer is the software layer which manages all the web services offered to customers by the SaaS provider. The second layer is the PaaS platform layer which includes the admission control and scheduling algorithms for ensuring the SLA contracts between the consumers and the provider. Further, this layer allocates the required VMs to fulfill the customer’s requests. Finally, the IaaS layer controls the initiation and removal of the VMs. Minimizing the number of the VMs in this layer ensures reducing the cost of the IaaS infrastructure. It is crucial for the IaaS provider to maximize resources utilization to minimize the infrastructure const. Further, the SaaS cloud provider should minimize the cost penalties from the Service Level Agreement (SLA) violations, and satisfy the SLA agreements. Therefore, the algorithms in the PaaS layer play the role of the SLA management. The main objectives of SLA management is to ensure minimizing the IaaS Infrastructure cost, SLA
violations, and maximizing the performance and the VMs utilizations.
Users Request a set of aggregated web services.
SaaS Distinct web services
PaaS Admission
control
Scheduling of the VMs
IaaS
Set of virtual machines VMs
Hardware resources
Figure 1. The general model of distributed SOA applications in a cloud environment.
The service consolidation problem is defined as an optimization problem which allocates the set of composed or aggregated web services on a set of VMs to ensure certain QoSs, such as the response time defined in the SLA while at the same time minimizing the IaaS cost by minimizing the number of VMs and maximizing the initiated VMs utilizations [9]. Several research efforts has addressed the SCP problem using either heuristics or linear programming. However, these research did not consider the efficiency of the proposed algorithm given a large-scale virtual machines as well as the elasticity of the VMs.
To this end, this paper deals with the following challenges:
An admission control to avoid violating the specified SLA.
Finding the best available mapping for a set of aggregated services on a subset of large-scale VMs using light-weight metaheuristic algorithm. Satisfying the user’s QoSs requirements and
minimizing the SLA violations.
Maximizing the initiated VMs utilization. Taking into account the elasticity of the cloud by
adding or removing VM instances dynamically to reduce the cost incurred by the IaaS provider and the penalties of SLA violations.
The key contributions of this research are: 1) a mathematical formalization for a simple admission control of a SaaS provider to a void the violation of the QoSs specified in the SLA agreement, 2) a scheduling algorithm for a set of aggregated web services on a set of VMs using simulated annealing, 3) another scheduling algorithm for a set of aggregated web services on a set of VMs using Tabu search, 3) an empirical comparison between the previous algorithms.
formalization of the service consolidation problem is presented in Section 3. The proposed heuristic algorithm is presented in Section 4. Finally, Section 5 concludes and suggests future work.
II. RELATED WORK
Cloud computing is an advanced distributed computing environment which integrates the state of the art of the recent technological advancements such as virtualization, web services, and QoSs management for distributed large-scale applications. The aggregated services of the distributed application are offered by the SaaS provider while the computing resources are offered by the IaaS provider which maintains a set of virtual machines on large-scale data centers. The PaaS provider includes the admission control and the scheduling algorithm for the QoSs management based on the SLA agreement between the used and the PaaS provider. To this end, the SCP problem is defined as: given a set of virtual machines on data-centers of a public IaaS provider, and a set of aggregated web services, find a mapping of the services on the subset of the VMs which ensures certain QoSs, such as the response time defined in the SLA while at the same time minimizing the IaaS cost by minimizing the number of VMs and maximizing the initiated VMs utilizations [9].
The SCP problem is NP-hard problem, and is extensively studied using different techniques [9-11]. SCP and QoSs management problem has been addressed by auction mechanism in a number of research efforts [12, 13]. The auction mechanisms are used to select the set of services and the resources to achieve the maximum benefit for the customers rather than the utilization of the resources.
Several techniques handled the SCP problem ranges from such as heuristics, linear programming, and meta-heuristics [14, 15]. For example in [9], an algorithm based on integer linear programming and rule-based constraints defined between services and servers, is proposed to find a feasible solution for the SCP problem in a short time. However, the proposed algorithm does not take into account the dynamic elasticity of the VMs at the IaaS layer. Further, the algorithm is not efficient with large-scale instances.
In [4], an admission control strategy along with a scheduling algorithm, based on a utility function, is introduced to maximize the IaaS profit and satisfy the SLA agreement between the SaaS providers and the users. In the admission control, four different strategies are used to specify incoming requests as accepted or declined. The first strategy, Initiate a new VM, is used if the new request cannot be completed within the deadline on all available VMs. The second strategy, called wait strategy, is used to assign the new request on an initiated VM if it can be completed within the specified deadline of the
request. The third strategy, insert in VM, is used to insert the new request before already accepted requests on a particular VM if the already accepted requests can wait the new request to finish. The fourth strategy, penalty delay, accepts the new request with certain penalty if cannot be completed within the deadline. The main drawback of the admission control is that a specific sequence of the mentioned strategies is used which may not lead to the best possible scheduling. The scheduling algorithm maximizes the IaaS profit by reducing the resources cost by reducing the number of VMs initiated in the data centers as well as maximizing their utilizations. However, the proposed strategy and scheduling algorithm consider only a single web service request. In our research we are concerned with the QoSs of a distributed application, consisting of a set of aggregated web services, which considers. In [16], enhanced the previous admission control to dynamically select the best possible strategy for each new request using the decision tree algorithm.
In [17], a heuristic algorithm based on queuing network is proposed to allocate applications on the available servers. The proposed algorithm considers only the response time. In [18], an algorithm based on simulated annealing is used to improve the resource utilization. The experimental results showed that the algorithm outperform the First Come First Serve (FCFS) resource allocation method. In [19], a game theory is used to cloud resource allocation to improve the utilization of the resources. However, the algorithm is not scalable for large-scale set of resources.
The following section presents the proposed mathematical formalization of the service consolidation problem. Based on the mathematical problem formalization, the admission control will be proposed and the scheduling algorithms
III. PROBLEM FORMALIZATION
The main goal of the SCP algorithm is to assign a set of aggregated web services to a subset of virtual machines. The objective of the assignment is to improve the utilization of the resources and to satisfy the QoSs of the web services defined in the SLA agreement. By improving the utilization of the resources, we minimize the cloud infrastructure costs as we minimize the number of the required virtual machines. The formal model about the Cloud SCP problem can be expressed as follows:
depends on the available resources of the physical machine m.
Let M is a set of physical machines, V is a set of virtual machines, R is a set of physical resources common to all machines. S is a set of web services. Each web service s explicitly defines the required resources r, such as CPUs, memory and network bandwidth.
𝐶 𝑚, 𝑟 is the total capacity of resource r on machine m, and 𝑅𝑞 𝑠. 𝑟 is the requirement of resource r by web service s. 𝑆𝐶 𝑚. 𝑟 is the safety capacity of resource r for machine m.
Let M(s) = m is the assignment of the web service s
on machine m, the usage U of a machine m for a resource r is defined as:
𝑈 𝑚. 𝑟 = 𝑅𝑒𝑞(𝑠. 𝑟) 𝑠∈𝑆.𝑀 𝑠 =𝑚
(1)
The first rule of any admission control strategy is to assign a web service to a certain machine only if there are available resources on the physical machine
m. A web service s can be assigned on a machine m
only if the machine has enough capacity available on every resource r. An assignment should satisfy the capacity constraint:
𝑈 𝑚. 𝑟 ≤ 𝐶 𝑚. 𝑟 . ∀ 𝑚 ∈ 𝑀. 𝑟 ∈ 𝑅 (2)
The utility function for assignment M, f(M), which describe the resource assignment is described as follows:
𝑓 𝑀 = 𝑤1 𝑓 𝐶 + 𝑤2 𝑓(𝑅𝑇) (3)
𝑤1 and 𝑤1are weights. Each weight indicates the preference for the assignment, and 𝑤1+ 𝑤2= 1.
The term 𝑓 𝐶 defines the utility function for the workload on physical machine m, and 𝑓 𝐶 is described as follows:
𝑓 𝐶 = 1 − 𝐶 𝑚. 𝑟 − 𝑈(𝑚. 𝑟)
𝑆𝐶 𝑚. 𝑟 − 𝑈(𝑚. 𝑟) (4)
The term 𝑓(𝑅𝑇) defines the utility function for the expected response time, and 𝑓 𝑅𝑇 is described as follows:
𝑓 𝑅𝑇 = 1 − 𝑇𝑒 𝑇𝑆𝐿𝐴
(5)
𝑇𝑒 is the expected response time of the web services
S on the current assignment M, described as follows: 𝑇𝑒= 𝑀𝑎𝑥𝑠(𝑟𝑒𝑠𝑝𝑜𝑛𝑠𝑒_𝑡𝑖𝑚𝑒(𝑠. 𝑣)) (6) 𝑇𝑆𝐿𝐴 is the upper bound of the response time defined in the SLA agreement.
The following section describes the proposed scheduling algorithms which find the appropriate assignment for the set of aggregated web services S
on virtual machines V by evaluating the utility function defined in (3).
IV. THE PROPOSED ALGORITHM
Figure 2 shows the general architecture of the cloud execution environment for distributed web-services applications. The architecture receives the requests from the consumers as well as the QoSs preferences for the requested services. The request is forwarded to the cloud service discovery and the admission control to find the best match services according to the user request and preferences. The proposed scheduling algorithm uses the utility function, defined in Equation (3), to evaluate the nominated
Figure 2. Cloud SaaS resource broker. SaaS provider
PaaS
Admission control and Service discovery
SLA-based utility function evaluation
Resource allocation search function
Resource allocator users
Request for aggregated services S
IaaS Provider
resource assignment. The resources are allocated from the IaaS cloud provider. The IaaS provider respond with the required VMs to the SaaS provider by instantiating the VMs images on the physical resources.
The following subsection will discuss two different scheduling algorithms, namely Simulated Annealing and Tabu Search, to find an appropriate resource allocation for the user requests.
A. Simulated Annealing
The simulated annealing (SA) search heuristic is an iterative algorithm that is widely used in the literature for scheduling distributed component-based application on distributed resources. The simulated annealing algorithm randomly perturbs the current selected resource allocation to find a better resource allocation. The SA search algorithm is a generalization of the Monte Carlo algorithm that is used for optimization of multi-variable functions. The concept originates from the method in which crystalline structures are brought into more ordered states by an annealing process of repeated heating and slowly cooling the structures. Simulated Annealing is used as a scheduling algorithm in the grid environment [20]. Further, in [18], Simulated Annealing has been used as a scheduling algorithm to allocated independent requests to resources to maintain high utilization.
Figure 3 shows the main steps of the SA algorithm, which is an iterative process. During each iteration, a random allocation of the aggregated web services on a subset of a subset of virtual machines is proposed. After that, each proposed allocation is perturbed to find a better mapping of the aggregated web services on available virtual machines. The reallocation gain from the currently proposed allocation to the
randomly generated allocation is calculated using Equation (5). If the gain is positive, the randomly generated allocation is assigned as the currently selected allocation. If the maximum number of iterations is reached, or no allocation is being accepted, the selected allocation is returned as the best allocation. The SA algorithm iteratively decreases the temperature T in order to jump out from local minima. At higher values of T, the algorithm frequently accepts bad allocations to reduce the chance of getting stuck with a local minimum.
B. Tabu Search
The Tabu Search (TS) algorithm is a popular techniques in assigning multiple jobs on limited resources in Grid computing [21-23]. Tabu search algorithm is proved to be effective in finding an optimum solution for resource scheduling under time and cost constrains [22, 24]. TS is a meta-heuristic scheduling algorithm used to guide the search for resources as a global optimized solution [25]. As shown in the TS Algorithm, Figure 4, the TS algorithm uses a historical memory which is a short-term memory, simply called recency. Recency stores the information of the recently explored solutions, and a long-term memory, simply called frequency. It contains the collected information during the overall search process. The solutions stored in the recenecy and frequency lists are considered tabu, and marked as restrictions. As a result, some aspiration criteria are needed for removing the tabu solutions. There are inner heuristics like the local search which are used for exploring the neighborhood of a solution, or the intensification and diversification procedures which are used for managing the exploration/exploitation on the search space. The components of the TS
Input: initial resource allocation R. BEGIN
Start with an initial temperature T numberOfAcceptedSolutions = MAXACCEPTED
WHILE ({termination condition is not satisfied} numberofAcceptedSolutions > 0) DO numberOfAcceptedSolutions = 0
REPEAT the following a fixed number of times
Generate a random resource allocation dr randomly
Calculate the gain from the utility function, Equation (5). IF (gain > 0 OR random() < exp(-gain/kT) ) THEN
Proposed_allocation = dr
numberOfAcceptedSolutions = numberOfAcceptedSolutions + 1 IF( numberOfAcceptedSolutions == MAXACCEPTED) BREAK ENDIF
END REPEAT
Decrease the temperature T; END WHILE
return(Proposed_allocation); {whatever found so far is the best deployment found} END
algorithm, well described in [26], consists of:
Service mapping: A mapping of the set of services to a set of physical machines. The mapping is represented as a vector of size n where mapping[i] indicates the machine where service i is assigned to.
Initial mapping: It is generated randomly but should satisfy the capacity condition, equation (2), where enough resources for the web service should be available on the physical machine. Further, the assignment should satisfy the utility function condition, equation (3).
Historical memory: As described before, the historical memory consists of three different memories:
1) The recency memory which is a tabu list with the information of the last mapping of each web service was assigned to every physical machine, 2) The tabu hash table contains all the information
of all the explored mappings,
3) The frequency memory which is a list of how many times every web service has been assigned each physical machine.
Aspiration criteria: Two criteria are used to accept tabu movements:
1) fitness (they are accepted when yielding to better mappings),
2) makespan (movements improving the makespan of the mapping are allowed).
Neighborhood exploration: The TS considers neighbors which satisfy better improvement of the utility function defined in Equation (3).
Intensification: The process of improving the current mapping if the current mapping is in a promising region.
Diversification. Three soft diversification methods are used to perform perturbations to the mapping:
V. THE PERFORMANCE EVALUATION
The CloudSim simulator [27] is used to evaluate the proposed algorithm with in a cloud environment. The proposed algorithm is implemented within a cloud environment consists of one IaaS architecture. The IaaS architecture contains 100 physical machines each of which can initiate up to 5 VMs. The requests arrival rate is modelled as Poisson distribution with varying mean from 1000 to 5000 requests per second. Each request randomly create consolidated services using Poisson distribution with varying mean from 10 to 50 web services. The response time for each web service is represented using normal distribution with mean equal to 200ms and standard deviation equal to 50.
Table
1
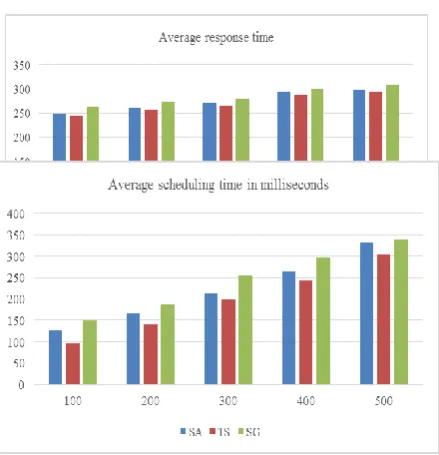
shows the SLA settings for each web service. The following evaluation results are obtained using the average of 10 experiments run.Figure 5 shows the number of initiated VMs corresponding to different number of requests created randomly using the above configuration. It is obvious that the Tabu search algorithm provides a better utilization than the Simulated Annealing and the static greedy algorithms (SG) (at least 10% less than the Simulate Annealing, and 15% less than the static greedy). Figure 6 shows the average response time for the proposed scheduling. It is clear that the tabu search could maintain the response time specified in the SLA even under heavy requests unlike the simulated annealing and the static greedy algorithms. Figure 7 shows that the scheduling time for the tabu search is 17% less than the other algorithms.
Input: initial service-resource mapping. BEGIN
Reset the tabu and aspiration conditions WHILE not termination-condition DO
Generate a subset of mapping[s] which do not violate the tabu conditions or hold the aspiration criteria
Choose the best mapping with respect to the utility function in Equation (5) if improvement(mapping) then update the mapping
Update the recency and frequency;
if (intensification condition) then Perform intensification; if (diversification condition) then Perform diversification; END WHILE
return(mapping); {whatever found so far is the best mapping found} END
Table 1. SLA settings
VI. CONCLUSION AND FUTURE WORK
This paper has presented a formalization model of the service consolidation problem on the cloud environment in which allocates a set of composed or aggregated web services on a set of VMs. Further an investigation of a number of scheduling algorithms which aim to maximize the SaS provider profit by efficiently minimizing the cost of the rented resources from the IaaS provider. This is done by maximizes the utilization of the initiated VMs and minimizing the number of the initiated VMs. Experimental evaluation showed that that the
proposed Tabu scheduling algorithm improves the number of initiated VMs with fastest response time than the simulated annealing scheduling algorithm and the static greedy scheduling algorithms.
The focus in the future work will be in improving the robustness of the admission control to avoid overloading the resources, and to reduce the number of SLA violations. Moreover, it is important to consider dynamic SLA negotiations along with the admission control.
R
EFERENCES[1] F. Curbera, M. Duftler, R. Khalaf, W. Nagy, N. Mukhi, and S. Weerawarana, "Unraveling the Web Services Web: An Introduction to SOAP, WSDL, and UDDI," IEEE Internet Computing, vol. 6, pp. 86-93, 2002.
[2] M. P. Papazoglou, Web Services: Principles & Technology: Pearson Education, 2008.
[3] D. Guinard, V. Trifa, and E. Wilde, "A resource oriented architecture for the Web of Things," in Internet of Things (IOT), 2010, 2010, pp. 1-8.
[4] L. Wu, S. K. Garg, and R. Buyya, "SLA-based admission control for a Software-as-a-Service provider in Cloud computing environments," J. Comput. Syst. Sci., vol. 78, pp. 1280-1299, 2012.
[5] M.-K. HUSSEIN, "Towards an Adaptive QoS of Cloud-based Web Services," International Journal of Engineering and Innovative Technology (IJEIT), vol. 4, pp. 27-32, 2014. [6] M.-K. HUSSEIN and M.-H. MOUSA, "A Framework for
Adaptive QoS of Web Services using Replication," International Journal of Computer Science & Communication Networks, vol. 2, pp. 288 - 294, 2012. [7] S. Son, G. Jung, and S. C. Jun, "An SLA-based cloud
computing that facilitates resource allocation in the distributed data centers of a cloud provider," J. Supercomput., vol. 64, pp. 606-637, 2013.
[8] L. Wu, S. K. Garg, and R. Buyya, "SLA-Based Resource Allocation for Software as a Service Provider (SaaS) in Cloud Computing Environments," presented at the Proceedings of the 2011 11th IEEE/ACM International Symposium on Cluster, Cloud and Grid Computing, 2011. [9] K. Dhyani, S. Gualandi, and P. Cremonesi, "A Constraint
Programming Approach for the Service Consolidation Problem," in Integration of AI and OR Techniques in Constraint Programming for Combinatorial Optimization Problems: 7th International Conference, CPAIOR 2010, Bologna, Italy, June 14-18, 2010. Proceedings, A. Lodi, M. Milano, and P. Toth, Eds., ed Berlin, Heidelberg: Springer Berlin Heidelberg, 2010, pp. 97-101.
[10] D. Ardagna, G. Casale, M. Ciavotta, J. F. Pérez, and W. Wang, "Quality-of-service in cloud computing: modeling techniques and their applications," Journal of Internet Services and Applications, vol. 5, pp. 1-17, 2014.
[11] S. Singh and I. Chana, "A Survey on Resource Scheduling in Cloud Computing: Issues and Challenges," Journal of Grid Computing, pp. 1-48, 2016.
[12] S. Arshad, S. Ullah, S. A. Khan, M. D. Awan, and M. S. H. Khayal, "A survey of Cloud computing variable pricing models," in Evaluation of Novel Approaches to Software Engineering (ENASE), 2015 International Conference on, 2015, pp. 27-32.
[13] W. Y. Lin, G. Y. Lin, and H. Y. Wei, "Dynamic Auction Mechanism for Cloud Resource Allocation," in Cluster, Cloud and Grid Computing (CCGrid), 2010 10th IEEE/ACM International Conference on, 2010, pp. 591-592.
[14] A. Beloglazov and R. Buyya, "Optimal online deterministic algorithms and adaptive heuristics for energy and performance efficient dynamic consolidation of virtual machines in Cloud data centers," Concurr. Comput. : Pract. Exper., vol. 24, pp. 1397-1420, 2012.
[15] E. Yaqub, R. Yahyapour, P. Wieder, A. I. Jehangiri, K. Lu, and C. Kotsokalis, "Metaheuristics-Based Planning and
SLA options values
Response time 150 — 300 ms
Number of virtual CPUs 1
Storage size 10GB
Figure 6. Comparison between the average response time for the Tabu search, Simulated Annealing and the static greedy
algorithm.
Figure 5. The number of initiated VMs corresponding to different number of requests.
Figure 7. Comparison between the average scheduling time for the Tabu search, Simulated Annealing and the static greedy
Optimization for SLA-Aware Resource Management in PaaS Clouds," in Utility and Cloud Computing (UCC), 2014 IEEE/ACM 7th International Conference on, 2014, pp. 288-297.
[16] F. Motavaselalhagh, F. Safi Esfahani, and H. R. Arabnia, "Knowledge-based adaptable scheduler for SaaS providers in cloud computing," Human-centric Computing and Information Sciences, vol. 5, pp. 1-19, 2015.
[17] J. Anselmi, E. Amaldi, and P. Cremonesi, "Service Consolidation with End-to-End Response Time Constraints," in 2008 34th Euromicro Conference Software Engineering and Advanced Applications, 2008, pp. 345-352.
[18] D. Pandit, S. Chattopadhyay, M. Chattopadhyay, and N. Chaki, "Resource allocation in cloud using simulated annealing," in Applications and Innovations in Mobile Computing (AIMoC), 2014, 2014, pp. 21-27.
[19] P. S. Pillai and S. Rao, "Resource Allocation in Cloud Computing Using the Uncertainty Principle of Game Theory," IEEE Systems Journal, vol. PP, pp. 1-12, 2014. [20] A. YarKhan and J. J. Dongarra, "Experiments with
Scheduling Using Simulated Annealing in a Grid Environment," in Grid Computing — GRID 2002: Third International Workshop Baltimore, MD, USA, November 18, 2002 Proceedings, M. Parashar, Ed., ed Berlin, Heidelberg: Springer Berlin Heidelberg, 2002, pp. 232-242.
[21] J.-q. Li, Q.-k. Pan, and Y.-C. Liang, "An effective hybrid tabu search algorithm for multi-objective flexible job-shop
scheduling problems," Computers & Industrial Engineering, vol. 59, pp. 647-662, 2010.
[22] F. Larumbe, B. Sans, and x00F, "A Tabu Search Algorithm for the Location of Data Centers and Software Components in Green Cloud Computing Networks," IEEE Transactions on Cloud Computing, vol. 1, pp. 22-35, 2013.
[23] I. Darmawan, Kuspriyanto, Y. Priyan, and I. J. M, "Integration of Genetic and Tabu Search algorithm based load balancing for heterogenous grid computing," in Computer, Control, Informatics and Its Applications (IC3INA), 2013 International Conference on, 2013, pp. 325-329.
[24] M. I. Alam, M. Pandey, and S. S. Rautaray, "A Proposal of Resource Allocation Management for Cloud Computing," International Journal of Cloud Computing and Services Science, vol. 3, pp. 79-86, 2014 2014.
[25] "Tabu Search—Part I," ORSA Journal on Computing, vol. 1, pp. 190-206, 1989.
[26] J. C. Fatos Xhafa, Bernabé Dorronsoro, Enrique Alba, "A Tabu Search Algorithm for Scheduling Independent Jobs in Computational Grids," Computing and Informatics, vol. 28, pp. 1001-10014, 2009.