9 Page 9-13 © MAT Journals 2019. All Rights Reserved
Detecting Phishing Attack and Spam Email Classification
Sandhya S. Dhakane1, Apurva S. Badgujar1, Sohel Bagwan1, Bharti Kudle21
UG Students, 2Professor 1,2
Department of Computer Science, Genba Sopanrao More College of Engineering, Balewadi, Pune, Maharashtra, India
Email: sandhyadhakane9@gmail.com DOI: http://doi.org/10.5281/zenodo.2602658
Abstract
Now a days phishing Attack could be a threat that acquire sensitive data like user-name, watchword etc through on-line. Phishing email contains messages like raise the users to enter the non-public data so it's simple for hackers to hack the knowledge. Phishing could be a sort of on-line fraud that aims to steal sensitive data like on-line passwords and master card data. To beat this issues associated with security we have a tendency to developed application which supplies mobile and email verification, invisible virtual keyboard that pattern can we have a tendency to be sent to users email account from that user are sort thatdigit and login with success. Conjointly we have a tendency to plan the Spam email detection victimization classification.
Keywords: Information security; intrusion detection; phishing attacks; intrusion detection systems.
INTRODUCTION
Phishing is printed as a result of the fallacious acquisition of con particularization by the meant recipients and conjointly the misuse of such knowledge. The phishing attack is usually done by email. An example of Phishing; as if e-mail seem to be from noted internet sites, from a user's bank, master card company, e-mail, or web service provider. Generally, personal data like master-card selection or word is asked to update accounts. These emails contain a universal resource locater link that directs users to a different electronic computer. This web website is basically a pretend or modified web site. Once users head to the present electronic computer, they’re asked to enter personal data to be forwarded to the phishing wrong-doer. Phishing is usually accustomed learn someone's word or credit cardinfo. With the help of e-mail prepared as if coming back from a bank official institution, computer users ar directed to fake sites. In general, the info that’s purloined by a phishing attack is as
follows: User account selection, User passwords and user name master card data net banking data. The anti Phishing machine, that's supposed to forestall serious threats like this, catches malicious e-mails incoming at e-mail addresses integrated into the system. This system put together provides universal resource locater based mostly management. The system evaluates the keywords fenced within the prevailing info and thus determines the contents of the mail.
Motivation of the Project
The Phishing attack is a form of cybercrime where an attacker imitatesa real person institution by promoting them as an ocial person or entity through e-mail or other communication mediums. By using this type of mailing the attacker hack the user account details. To resolve this type of problems of we developing the application.
Literature Survey
Paper 1: Content Based Spam E-mail Filtering
10 Page 9-13 © MAT Journals 2019. All Rights Reserved Author Name: P. Liu and T.S. Moh,
Description: Currently, E-mail is one among the foremost vital strategies of communication. However, the increasing of spam emails causes traffic congestion, decreasing productivity, phishing, that has become a significant downside for our society. And also the range of spam e-mail is increasing per annum. There-fore, spam e-mail filtering is a vital, purposeful and difficult topic.The aim of this analysis is to search out an efficient resolution to filter doable spam-mails. And as we all know, in recent days, there ar several techniques that spammers use to avoid spam-detection like obfuscation techniques. During this case, the subsequent projected approach uses email content solely to make keyword corpus, along with some text process to handle obfuscation technique. The algorithmic rule was evaluated victimisation the CSDMC 2010 SPAM cor-pus knowledge set that contained 4327 emails within the coaching knowledge set and 4292 emails within the testing knowledge set. The experimental results show that the pro-posed algorithmic rule has 92.8% accuracy.
Paper2: Origin (Dynamic Blacklisting) Based Spammer De-tection and Spam Mail Filtering Approach.
Author Name: N. Agrawaland S. Singh, Description: Messages are the essential unit of web applications. Numerous messages are sent re-ceived ordinarily with an exponential development step by step however spam mail has become an intense issue in email correspondence condition. Thereare number of substance based filter techniques accessible in particular content based, image based separating and a lot more others to channel spam send. These tech-niques are costlier in respect of computation and network resources as they require the examination of whole message and computation on whole contentat the server. These filters are also not in dynamic nature because the nature of spam mail and spammer changes frequently. We
proposed origin based spam-filtering approach, which works with respect to header information of the mail regardless of the body content of the mail. It optimizes the networkand server performance
Paper3: A Practical Approach to E-mail Spam Filters to Protect Data from Advanced Persistent Threat, 2016.
Author Name: J. V. Chan-dra, N.Challa and S.K. Pasupuleti
Description: Time based mostly Self-destructing email primarily aims at protective knowledge privacy. In this paper we have a tendency to mention the spear phishing method as a neighbourhood of advanced persistent threat attack that gathers info associate in nursing targets an individual or organisation. It implements of social engineering techniques to collect knowledge concerning recipient. Malicious emails area unit sent by combining the psycho-logical and technical tricks, wherever phishing emails contains web-links that provoke the recipient to click on them, these links contains websites that area unit infected with malware. We have a tendency to additionally targeting Spam Emails and Targeted Malicious E-mails. During this paper we have a tendency to mentioned recipient aspect detection techniques, like spam or direct mail filters victimisation mathematical construct of theorem spam filtering. We have a tendency to contribute a transparent indication of behaviouralstructure of Advanced Persistent Threat and a suicidal mechanism is adopted as weapons system to shield sensitive confidential knowledge from intruders. A mathematical approach is given together with the process sensible analysis and experimental result.
Paper4: Spam Mails Filtering Using DifierentClassifierswith Feature Selection and Reduction Techniques, 2015.
11 Page 9-13 © MAT Journals 2019. All Rights Reserved GadhwalT. Vyas,
Description: The ceaseless development of email clients has brought about the increasingof spontaneous messages otherwise called Spam. In current, server side and clientside against spam channels are presented for recognizing difierent highlights of spamemails. In any case, as of late spammers presented some viable traps comprising of installing spam substance into advanced picture, pdf and doc as connection which can make incapable to current systems that depends on investigation computerized message in the body and subject fields of email. A considerable lot of proposed working procedure gives an enemy of spam sifting approach that depends on information mining methods which characterize the spam and ham messages. The adequacy of these methodologies is assessed on expansive corpus of straightforward content informational collection just as content implanted picture informational collection. However, the majority of the separating systems can't deal with regular changing situation of spam sends embraced by the spammers over the time. In this way improved spam control calculations or upgrading the effectiveness of different existing information mining calculations to its fullest degree are the most extreme necessity. A similar report is introduced on different spam sifting systems embraced based on different ascribes to discover best among all to separate the best outcomes.
Paper5: A survey and evaluation
ofsupervisedmachinelearning tech-niques forspam
Emailltering
Author Name: P. Prajap-ati and
S.Gadhwal,
Description: Emails square measure utilized in most of the fields of education and business. They will be classified into ham and spam and with their increasing
use; the magnitude relation of spam is increasing day by day. There square measure many machine learning techniques that provide spam mail filtering ways, like clump, Naive Bayes etc. This paper considers totally different classification techniques exploitation wood hen to filter spam mails. Result shows that Naive Bayes technique provides sensible accuracy (near to highest) and take least time among alternative techniques. Conjointly a comparative study of every technique in terms of accuracy and time taken is provided.
Existing system
In the exixting system, they proposed methodology methodology to combat phishing emails.We developed a system called SAFE-PC for detecting new phishing campaigns, which are evolved from prior ones. Check phishing techniques and startegies
Proposed system
1. In the proposed we developed application that detects phishing attacks on Emails.
2. Also provide security for user account like verification of mobile number and email.
3. Also find Mac address of that system. 4. The main proposed system of our
project is to implement virtual invisible keyboard that only accessible by user when the pattern is match and that pattern will be send on email according to that mail the user type that pattern if the pattern will be match then the user is detected as original user and access that account .If the pattern from virtual invisible keyboard is not match more than one time then message will be sent to their emails and on mobile number.
5. Detect the Spam Email based on content on Emails.
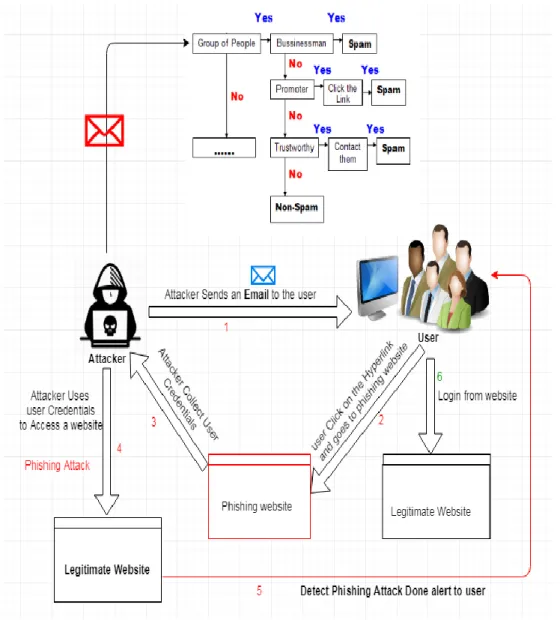
12 Page 9-13 © MAT Journals 2019. All Rights Reserved System Architecture
Figure 1: System Architecture
Application
1. Provides security in social media like facebook, twitter, emails
2. Use in military security purpose to secure data.
3. Goverments websites. Advantages
1. Gives security over our Email accounts 2. Secure our private data.
3. Notify message gives after login one time notify us that something gone wrong with our accounts.
4. Secures important emails that useful in various sectors like Financial, security, Government.
Disadvantage
1.More than one time fails to login gives trouble to user for login again 2.invisible keyboard matching after checking mails that matches lose time but provide security.
CONCLUSION
In this we conclude that defends security over phishing attack. we provides security over phishing attack threats by providing mobile Number OTP, Email verification and virtual invisible keyboard to access user account.Also we detect spam emails using the classification and content of email.
13 Page 9-13 © MAT Journals 2019. All Rights Reserved REFERENCES
1. Christopher N. Gutierrezy, TaegyuKimy, Raffaele Della Cortez, Jeffrey Averyyx,DanGoldwassery, Marcello Cinquez, SaurabhBagchiy, "Christopher N. Gutierrezy, TaegyuKimy, Raffaele Della Cortez, Jeffrey Averyyx,DanGoldwassery, Marcello Cinquez, Saurabh Bagchiy",2018.
2. Juan Chen, ChuanxiongGuo,"Online Detection and Prevention of Phishing Attacks"16 July, 2015.
3. Dr.RadhaDamodaram,"STUDY ON
PHISHING ATTACKS AND
ANTIPHISHING TOOLS" Jan-2016. 4. V. Suganya,"A Review on Phishing
Attacks and Various Anti Phishing Techniques"April 2016.
5. MuhammetBaykara,
ZahitZiyaGürel"Detection of phishing attacks"2018.
6. J. Thomas, N. S. Raj and P. Vinod, "Towards filtering spam mails using dimensionality reduction methods," 2014 5th International Conference- Conuence the Next Generation Information Technology Summit (Conuence), Noida, pp. 163-168, 2014. 7. H. AlRashid, R. AlZahrani and E. ElQawasmeh, "Reverse of e-mailspam filtering algorithms to maintain e-mail deliverability," 2014 Fourth International Conference on Digital
Information and Communication Technology and its Applications (DICTAP), Bangkok, pp. 297-300,2014.
8. S. Dhanaraj and V. Karthikeyani, "A study on e-mail image spam filter-ing techniques," 2013 International Conference on Pattern Recognition, Informatics and Mobile Engineering, Salem, pp. 49-55, 2013.
9. P. K. Panigrahi, "A Comparative Study of Supervised Machine Learn-ing Techniques for Spam E-mail Filtering," 2012 Fourth International Conference on Computational Intelligence and Communication Net-works, Mathura, pp. 506-512, 2012. 10.T. du Toit and H. Kruger, "Filtering
spam e-mail with Generalized Ad-ditive Neural Networks," 2012 Information Security for South Africa, Johannesburg, Gauteng, pp. 1-8, 2012.
Cite this article as: Sandhya S. Dhakane, Apurva S. Badgujar, Sohel Bagwan, & Bharti Kudle. (2019). Detecting Phishing Attack and Spam
Email Classification. Detecting
Phishing Attack and Spam Email
Classification, 4(1), 9–13.
http://doi.org/10.5281/zenodo.260265 8