8
Innovative Research in Engineering Sciences Vol 3(1), 8-14(2017)
Journal of Innovative Research in Engineering Sciences
ISSN(2476-7611)Journal homepage:
www.Joires.com
Steganography in least significant bits
Abolfazl Ghare Sofloo*1, Mehran Aghayi 2
1Master’s in software engineering, Islamic Azad University, Tehran, Iran. 2Professor of software Engineering, faculty member of Payam Noor, Tehran, Iran.
Abstract: Steganography is the art and science of hiding important information in other information. It should be done so that the host data do not be destroyed and no one can be informed about the existence of secret information; this means that if the information is placed in audio or video files, this can’t reduce the quality of these files in a significant way. On the other hand, in steganography, we need the host information resistance against processing methods, that is, contents of the message should be stable against the processing, or in other words, it is resistant to processes that are to explore the message and can’t readily reveal the message.
The increasing spread of the Internet in the current era has generated significant developments in the field of digital communications. Internet has become an environment for simple and fast sharing and exchanging of all kinds of digital products, text, audio, image and video, and results in quantitative and qualitative growth of the production of these products. With increasing production and pervasiveness of the use of these products, the owners of the works gradually became concerned about the protection of their rights; thus the issue of protection of copyrighted data, to avoid violating the rights of the authors, seemed necessary. On the other hand, the general use of encryption systems, each day was limited by state and the need for alternative methods for secret telecommunication was arose that was a prelude to the emergence of steganography. So far, most of the steganography methods for color images have been done in RGB color space, and all methods have hadtheirown advantages and disadvantages. This article while introducing different methods of steganography try to provide a new method for steganography and various advantages of this method.
Keywords: Steganography. Latent mining.Color space.Color image.RGB color space
1. Introduction
Since humans were able to communicate with each other, having the possibility of communicating secretly has been an important demand of people. Ongoing development of Internet and the rapid growth of the digital world have led people to the digital data and having communication through digital data. Meanwhile, the Communications Security is an important need which and daily need, which every day its importance is felt increasingly. In general, there are 2 ways of hidden communication. In the first method that is encryption data can be encrypted in a way that is understandable to third parties, but receiver and sender by using a shared key can decrypt the information. The second method of confidential communication is steganography. In steganography, in addition to keeping information secret, confidential relationship must be kept secret. In fact, the steganography is the art and science of hiding communication and aims to conceal the existence of any connection between sender and receiver. It is often assumed that the codification of an exchanged message, the connection becomes Secure, but in practice, only doing encryption is not sometimes enough.
Steganography is rooted in a Greek word meaning "covered writing", and in fact, it is the art and science of hiding information in a way that prevents discovery of the hidden message. Steganography consists of a
Large selection of communication methods that hide the message. These methods include invisible inks, micro
Points, digital signature and camouflaging channels. Actually, concealing communication by putting a message in a medium acts as coverage in a way that generates least detectable change, and makes it impossible to reveal the existence of hidden messages in the medium even as something likely. Steganography truly flourished in the twentieth century. Due to the development of technology in today's world and being possible to perform and operation from far away, using global and local networks, as well as the lack of need to concentrate all data in one place, and requirement of having access to remote information and also guaranteeing the security of information at the time of sending and reception, the importance of keeping information safe from unauthorized access becomes more and more evident. steganography is a method through which it is possible to move information, in the form of a masking agent, between specified points and with the highest degree of accuracy and security, So that even if in the route, information was accessed by unauthorized, there will be no possibility for them of having access to hidden data. In fact, steganography is the art and science of embedding information in a carrier medium, and given the significant progress of digital communication, its usage rate is increasing.
Article Info
9
There are numerous methods to embed information into another file. The most famous of these methods is LSB, which inserts information in least significant bits of image colors. In addition to carrying hidden information, steganography has other applications. One of its general applications is that, for example the legal owner of a picture can embed a series of messages within the image. This type of Steganography is called watermarking. In general, the main purpose of steganography, is security, which means the inability to prove the existence of the message. A lot of research has been done in the field of Steganography in gray images, but in comparison, much less research has been conducted in the domain of color images. Choosing a color space is the first step in the processing of color images. Among computer-related color spaces, are RGB, CMY (K), YUV, YCbCr, YIQ and HSV. [1]
By studies, numerous Steganography techniques have been proposed, and in this regard, many articles have been provided with different resistance and capacity. [2-5].
In this paper, a new approach is offered using LSB as well as XOR algorithm for storing a text file in an image and it is implemented in the software MATLAB and results will be presented.
2. Indicators in Steganography
Steganography systems have various indicators, and they can be categorized by them. Each application, based on needs, puts its main focus on a series of these indicators, and tries tosomehow enhance the ability of those indicators. A number of Steganography indicators can be grouped as follows:
A) We define the inclusion effectiveness of the medium which Steganography is run on: When we give it as input to the detector, the detector detects the presence of Steganography, Having this in mind; the effectiveness of Steganography process is tantamount to possibility of inclusion process output, at the time of decryption, being considered experienced Steganography.
B) Similarity
In general, the accuracy of a Steganography system depends on the perceptual similarity between the original image and the image Steganography run on. Sometimes the qualities of medium Steganography run on and the main medium is reduced in the transmission path before they reach consumer. In many applications, in order to achieve higher strength and lower cost, we can consent to intermediate accuracy.
C) Volume of data storage
Storage volume refers to the number of bits in a server or per unit of time in which the medium is coded. For an image, storage volume is the number of bits that are stored in it, while for sound; storage volume is the number of bits that are stored in one second. Different applications may require different storage volumes. In many applications there is a need for the detector to detect if Steganography is run on the message. If there is such a message, it should specify which of two different modes has been coded.As
regards the articles which are in the field of Steganography, there are a lot of systems in which there is only single-bit Steganography, and detector only determines whether there is Steganography or not. such systems are sometimes called single-bit Steganography systems because there are only two different cases of output: The presence or absence of Steganography.
D) Resistance
After information was recorded in the host signal by using a Steganography method, Digital nature of the host signal and a variety of hardware and software subject the host signal to different kinds of processing in order to edit and bring about a change. After doing this process, it is possible that all or part of the information contained in the host signal is not able to be recovered. After doing a special processing on the host signal the higher the recoverable amount is, the more robust Steganography method is than that kind of processing[12-19].
E) Cost
Steganography detection process can economically depend on specific business indicators. Technically, the two concepts should be considered. The first concept is the speed of inclusion and recovery the number of the included and detectors that must be put to work. The other concept is that whether the included content and detector that are needed for inclusion and recognition should be of special-purpose hardware tools or only software or a combination of these two can be used. In distributed control system, inclusion and recognition processes should be performed straightaway. Different applications are different regarding the number of the included and detectors they need. For example[20-25], distributed control system generally requires a small number of the included. But it perhaps needs to have hundreds of detectors at different geographical locations. Applications that are related to copy control may need one included,but millions of detectors which are inaudio and video devices and are all its detectors[26].
3. Research method
10
3-1. Main activities of the research planFigure 1. Channels Forming RGB color space.
One of the color spaces that is well known for Steganography is RGB. (Figure 1) Because the colors of red, green and blue are the primary colors, each color is determined as weighted sum of red, green and blue components. A vector in the space of RGB describes the colors intensity of the components.
In this article, as shown in figure (2), before planting the original data, one of the color image channels was determined as reference. And then using the information that is to be run on by Steganography and we started to do XOR operation. And after the imposition of embedding conditions in all the pixels, all information is embedded in the remaining two channels using the proposed algorithms.
Figure 2. Steganography algorithm with the proposed method
All the steps to insert Steganography into an image are as follows:
1. Loading a picture in order to conduct Steganography:
In order to conduct Steganography on information, first call an image which we want to hide information in.
2. Converting the text to decimal and then to binary
In the phase, after calling the considered image, we should separate the chosen text word by word and make it like a fiber. Each word is converted to its corresponding number (decimal) and in the next stage each number is converted to binary.
Message (10000001) Dec2Bin
3. Breaking every bit message into eight parts In order to conduct Steganography on information, after converting each word to binary, in this phase each byte that represents a word is divided into eight bits.
Breaking into 8 parts (10000001)(10000001) 4. Selecting one of the three channels of the image for Xoroperation:
After dividing each byte into 8 bits, one of the three channels of the image is chosen as the reference matrix and Xoroperation is run so as to determine the considered channel for Steganography.
5. Selecting one of the pixels of the matrix chosen for Steganography:
As it was mentioned in previous phase, after choosing the reference channel and conducting Xor operation, we choose one of the remaining channels in order to do the first Steganography.
6. Inserting a bit of message characters in one of the channels of the covered object:
As you can see in Figure (3), every bit of message characters with a few bits is separated from the pixels of the covered object. The operation will continue until all the bits of the message become loaded.
Figure 3. Every bit of message characters with a few bits is separated from the pixels of the covered object
4. Discussion and conclusion
In this section we study the results of Steganography and latent mining, the proposed method and comparing it with the other existing methods. The comparison criteria in this article are MSE, PSNR and BER, which the formula to calculate comes in the following:
2
, , 1 1
3
, ' ,
M N
k R G B i j k k
MSE
MN
I i j I i j (1)
M and N specifies the height and width of the image and I is the original image and I ' is the image then after Steganography. [6]
n 2
10 log(2 1) PSNR
MSN
(2)
11
L (M(i) M (i))t 2 i 1
BER 100
L
(3)BER formula is used as to measure the error during extracting information. M(i) is the ith bit of the message embedded in the image and M'(j) is the ith byte of the extracted message. Moreover, L is the length of the message embedded in the image. Obviously the less the value of BER is, the better and more desirable the method is. [6] and [11].
4-1. comparing the results obtained from the proposed method with other methods available in RGB space
The results of applying the proposed algorithm has been announced on several announced images as shown in Table 1, as the host images and one text as for Steganography are as follows.
Table 1. The results of the simulation of the proposed method
Image name MSE amount PSNR amount
Baboon 0.51 71.02
Lena 0.52 70.95
Sailboat 0.52 70.97
Bird 0.54 70.79
The results of the proposed system were compared with the paper [7] and [8] in the field of quality of image Steganography is run on in Table 2 and diagram 1.
Table 2. Comparing the results of the proposed method and with the previous one
Image name
PSNR amount in
article (7)
PSNR amount in article (8)
Our proposed system
Baboon 48.7995 56.87 71.02
Lena 48.7943 55.96 70.95
Sailboat 48.7967 54.87 70.97
Bird 48.8063 54.76 70.79
koala 48.8787 54.32 70.67
Figure 4. Comparing the results of the proposed method with those of the previous
As can be seen Table (2), PNSR of articles [7] and [8] and the proposed method were compared with each other, and the PNSR amount obtained by the proposed
method was higher compared to the other methods, which reflects the quality of images after Steganography operations, and as we said before, by increasing the image quality, finding out about the presence or absence of information in the images decrease significantly.
4-2. comparing the results of the proposed method with the other color spaces
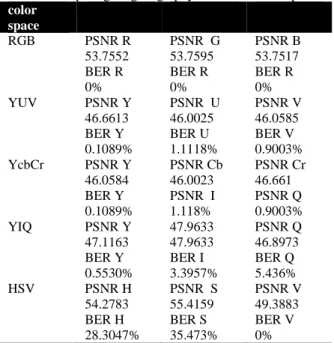
Steganography is implemented in different color spaces using MATLAB software and in order to run the tests, some messages with various bits are embedded in 24-bit color image and results are shown in Table 3 below.
Table 3. Comparing Steganography in various color spaces
color space
RGB PSNR R PSNR G PSNR B
53.7552 53.7595 53.7517
BER R BER R BER R
0% 0% 0%
YUV PSNR Y PSNR U PSNR V
46.6613 46.0025 46.0585
BER Y BER U BER V
0.1089% 1.1118% 0.9003%
YcbCr PSNR Y PSNR Cb PSNR Cr
46.0584 46.0023 46.661
BER Y PSNR I PSNR Q
0.1089% 1.118% 0.9003%
YIQ PSNR Y 47.9633 PSNR Q
47.1163 47.9633 46.8973
BER Y BER I BER Q
0.5530% 3.3957% 5.436%
HSV PSNR H PSNR S PSNR V
54.2783 55.4159 49.3883
BER H BER S BER V
28.3047% 35.473% 0%
Our criteria for determining which color space is more suitable for Steganography is PSNR and BER values for each color space channel. The less BER is and the more PSNR is , the better that method is. According to chart 3 and the values of PSNR and BER, it can be said that RGB color space is the most appropriate one in terms of Steganography capacity because in this color space BER is zero in all 3 channels, while their PSNR is high. After RGB, HSV is the second appropriate because BER in V channel of this color space is zero. The reason is that when the conversion of RGB color space to HSV and vice versa is done, this channel is not dependent on two other channels, i.e. H and S. But it should be noted that in HSV color space, two channels of S and H due to their high BER cannot be used at all. The cause of the existing error in the two channels is due to a rounding error when converting color spaces [27].
As shown in chart 3, PSNR and BER values in color spaces YUV, YCbCr are too close to each other. This is due to the similarity of these two conversions. These two color spaces, after HSV color space, are the most appropriate because BER value in them is so low. In these two color spaces; channel Y (in the YUV and YCbCr color spaces), and then channels V and Cr and
0 0.1 0.2 0.3 0.4 0.5 0.6 0.7 0.8
proposed method
article 7
12
finally U and Cb channels are suitable for Steganography respectively.
In the space color of YIQ, Y channel is partly proper for Steganography, while two channels I and Q are not suitable for it. It is due to high BER of these two channels.
The reason for BER in the color spaces of YUV, YCbCr, YIQ and HSV is due to conversions and rounding error. For the following reasons Steganography in RGB color space excels compared to other color spaces.
A) BER is zero in this color space, and Steganography capacity is high compared to other color spaces. PSNR is high (high image quality).
B) Computational complexity in this color space is low (because it does not need to convert space).
4-3. Comparing Steganography resistance of the different channels of different color spaces with the proposed method
In this article, in order to compare Steganography resistance in different channels of different color spaces we have used lament mining methods of WS [9] and Sample pair [10] that both are common and successful lament mining method. For this purpose, the exact 50 images on which Steganography was run in the previous step in different channels of different color spaces are tested and the results are given in chart 3 and chart 4.
As shown in charts (3 and 4) in color spaces in which conversion ratio is used, these coefficients make it harder to detect embedded message. As a result Steganography in color spaces YUV, YCbCr, YIQ and HSV compared to RGB have more resistance tolatent miners.Moreover, if we attempt to extract the data using the LSB in RGB color space, the output does not make any sense [28-29].
Table 4. The results of Sample Pair method of latent mining . Color
space
Diagnosis Percentage based on Channel Steganography run on
RGB Channel R Channel G Channel B 92% 94% 94% YUV Channel Y Channel U Channel V
26% 18% 30% YCbCr Channel Y Channel
Cb
Channel Cr 28% 16% 30% YIQ Channel Y Channel S Channel V
36% 16% 32% HSV Channel H Channel S Channel V
36% 18% 74%
Table 5. The results of WS method of latent mining Color
space
Diagnosis Percentage based on Channel Steganography run on
RGB Channel R Channel G Channel B 94% 98% 92% YUV Channel Y Channel U Channel V
0% 168% 2% YCbCr Channel Y Channel Cb Channel Cr
0% 16% 2% YIQ Channel Y Channel S Channel V
4% 22% 8% HSV Channel H Channel S Channel V
22% 20% 6%
Color spaces other than RGB have good resistance against conventional methods of latent mining.
Due to the conversions that are conducted from RGB color space to another color space is done; these conversions can be set as the key and it makes Steganography in these color spaces more resistance compared to latent mining methods.
A) Channel V in the HSV color space is suitable for Steganography, because BER is zero in this channel and its resistance is higher compared to Steganography in the channels of RGB color space.
B) Overall the problem with this form of Steganography in color space which use conversion ratio is that when extracting information, we have BER due to having rounding errors when converting RGB to considered color spaces.
4-4. The indicators of Steganography performed with the proposed method
As discussed in section 2 Steganography systems have various indicators which can categorize them. According to the matters proposed, the proposed indicators will be measured:
A) We assessed the effectiveness of inclusion of proposed matters in the cover object of Steganography, and after moving the cover object, 100% of the data were returned using a detector.
B) Similarity
Using the circuit PSNR obtained in the previous step it was clear that the cover object quality decreased significantly after Steganography, which reflects the quality of the considered method.
C) Data storage volume
According to the fact that in order to do Steganography, data instead of being converted to images, are Steganography run on, and this increases the storage volume.
D) Cost
In the control system, the distribution of inclusion processes and diagnosis system are carried out immediately. In order to do the processes of detecting Steganography in terms of economy, we can point out to characteristics of this proposed method that as to conduct Steganography and detection of information by the proposed method, only the public software and hardware are accessible and applicable.
Conclusion
In this paper in addition to present a method for Steganography of information, the proposed method was compared with a variety of Steganography areas. And in every area some well-known and common methods were introduced and their pros and cons were discussed. Moreover, some secure Steganography techniques and important, effective parameters affecting Steganography were introduced.
13
Regarding these methods we should always be careful how to determine the algorithm and its parameters.
In order to have a secure Steganography, in addition to algorithm and its area of work, we should consider its parameters and issues such as image quality, availability and other needful parameters; we should always strike a balance between Steganography capacity, and probability of exploring human and being detected statistically.
Steganography knowledge is very dynamic and Procedures for successful and undetectable Steganography has always been proposed by it. At the same time there are other ways are created to break these algorithms and discover hidden data. As a result the battle between the inventors of new methods of Steganography and their breakers always continues and with the advent of a new method to deal with previous methods.
The algorithm which was presented in detail in this article has been able to well be higher than other well-known storage methods. However, this method also cannot guarantee the impossibility of being detected by other methods provide.
Since the image is the most important medium being used especially on the Internet media and our visual perception of changes in the images is limited. Images have been known as one of the best cover media for Steganography. And thus numerous Steganography algorithms are offered for different image structures, such as raw images or BMP (24 bit color or 8-bit black and white), palette images (16 colors, 256 colors, ...) compressed images such as JPEG, 2000 JPEG and ... in location area and conversion area.
Using JPEG structure for image transmission, especially on the Internet is much more conventional than the rest of the structures, so several methods have been introduced for Steganography in JPEG images. In the case of GIF images, it should be noted that despite the widespread use of these images on the Internet and users tendency to use it, applying them has some limitations to using Steganography. In fact, the limited number of colors in an image palette (e.g. GIF) and their small size makes some trouble for Safe use of cryptographic algorithms.
References
1) Ze-Nian, Li., Mark, S., Drew. (2003), Fundamentals of Multimedia, Chapter 4.
2) Thomas, J., Leontin Philjon, N., Venkateshvara, R. (2011), Metamorphic cryptography — A paradox between cryptography and steganography using dynamic encryption, Dept. of Inf. Technol., Kings Eng. Coll, Chennai, India.
3) Sunny, D. (2014), Highly randomized image steganography using secret keys. Department of Computer Science, ManavRachna College of Engineering, Faridabad, Haryana (India).
4) Monica, A., Dagadita, E., Ioan, S., Razvan, D. (2013), Data Hiding Using Steganography,
Comput. Sci. & Eng. Dept., Univ. Politeh. of Bucharest, Bucharest, Romania.
5) Ajit, S., Swati, M. (2010), Securing Data by Using Cryptography with Steganography, SES, BPS MahilaVishwavidhyalaya,India.
6) Warangal, A.P. (2010), Estimating the Embedding Capacity of a Color Image using Color Difference, IEEE.
7) .Vaishnavia, D.,.Subashini, T.S. (2014), Robust and Invisible Image Watermarking in RGB Color spaceusing SVD, Dept. of Computer Science and Technology, Annamalai University, Chidambaram, 608002, Tamilnadu, India.
8) Rajni, G., Naresh K. (2014), LSB Based Digital Watermarking Technique, Department of Computer Science & Engineering, Giani Zail Singh PTU Campus Bathinda, Punjab.
9) Fridrich, J., Goljan, M. (2004), On estimation of secret message length in LSB steganography in spatial domain, Security, Steganography, and Watermarking of Multimedia Contents VI, E. J. Delp III and P. W. Wong, eds., Proc. SPIE 5306, 23-34.
10) Dumitrescu, S., Xiaolin, Wu., Wang, Zhe. (2003), Detection of LSB Steganography via Sample Pair Analysis”, In LNCS vol. 2578, Springer-Verlag, New York, pp. 355–372.
11) Sajedi, H. (2010), increased capacity of Steganography Pictures, Doctorate thesis, Sharif University of Technology, June.
12) Nutan, M., Swati, N. (2015), LSB Image Steganography with DES Cryptography, Sanghvi Institute of Management and Science, Indore, M.P., India.
13) Singh, R.K., Shaw, D.K., Javed Alam, M. (2015), Experimental Studies of LSB Watermarking with Different Noise, National Institute of Technology, Jamshedpur 831 014, India.
14) Simmons, G. J. (1984), The prisoners’ problem and the subliminal channel, in Advances in Cryptology: Proceedings of Crypto 83,(D. Chaum, ed.), pp. 51–67, Plenum Press.
15) Othman, O. K., Yusnita binti, Y. (2012), An Improved Wavelet Digital Watermarking Software Implementation.
16) Kumar, A., et al. (2014), Wavelet Based Image Watermarking: Futuristic Concepts in Information Security.
17) An Information-Theoretic Model for Steganography,Christian Cachin,March 4, 2004. 18) Petitcolas (Eds). (1999), Information Hiding
Techniques for Steganography and Digital Watermarking, Stefan Katzenbeisser. Artech House Books, Dec., ISBN 1-58053-035-4. 19) Cummins, J., Diskin, P., Lau, S., Parlett, R.
(2004), Steganography and Digital Watermarking, The University of Birmingham,
14
Comput. Sci. & Eng., Hajee MohammadDanesh Sci. & Technol. Univ. (HSTU), Dinajpur, Bangladesh.
21) Masud Karim, S. M. Md., Saifur Rahman, Md., Ismail, H. (2011), A new approach for LSB based image steganography using secret key, Computer Science and Engineering Discipline, Khulna University, 9208, Bangladesh.
22) Thomas, J., Leontin Philjon, N., Venkateshvara R. (2011), Metamorphic cryptography — A paradox between cryptography and steganography using dynamic encryption, Dept. of Inf. Technol., Kings Eng. Coll, Chennai, India.
23) Sunny, D. (2014), Highly randomized image steganography using secret keys, Department of Computer Science, ManavRachna College of Engineering, Faridabad, Haryana (India).
24) Adriana, M., Emil, D., Slusanschi, I., Dobre, R. (2013), Data Hiding Using Steganography, Comput. Sci. & Eng. Dept., Univ. Politeh. of Bucharest, Bucharest, Romania.
25) AjitSingh, S.M. (2013), Securing Data by Using Cryptography with Steganography, SES, BPS Mahila Vishwavidhyalaya, India.
26) Vaishnavia, D., Subashini, T.S. (2014), Robust and Invisible Image Watermarking in RGB Color space using SVD, Dept. of Computer Science and Technology, Annamalai University, Chidambaram, 608002, Tamilnadu, India.
27) Rajni, G., Naresh, K. (2014), LSB Based Digital Watermarking Technique, Department of Computer Science & Engineering, Giani Zail Singh PTU Campus Bathinda, Punjab.
28) Shing Hsieh, M., Tseng D.C., Huang, Y.H. (2001), hiding digital watermarks using multiresolution Wavelet transform, IEEE Transactions on industrial electeonics, 48(5). 29) Caronn, G. (1995), assuring ownership right for