International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 7, July 2014)
329
Flooding Attack in Delay Tolerant Network
Preeti Nagrath
1, Dr. Sandhya Aneja
2, Prof. G. N. Purohit
31
Department of Computer Science, Banasthali University, Jaipur, Rajasthan 2
Research Fellow, IBM Center, University Brunei, Darussalam 3Department of Computer Science, Banasthali University, Jaipur, Rajasthan Abstract—Delay Tolerant Network (DTN) routing
protocols works in an environment where there is no guarantee of end to end path between source and destination. DTNs operate with the principle of store, carry and forward. Mobile nodes have limited buffer space and contact opportunity. So the resources are useful and must be used optimally. The routing protocol message replication strategies react differently to the increase or decrease of buffer size in different network nodes. Aim of this paper is to study the importance of space constraints on various protocols with respect to message delivery ratio, latency & overhead. The simulation results show how resources are an important factor for enhancing the overall network performance. So we must prevent the network from malicious nodes which by various attacks consume the buffer space of the nodes and thereby hamper the network in terms of various evaluation parameters like message delivery and overhead. We also describe how various types of flooding attacks can be implemented by malicious nodes on different routing protocols which can degrade the network performance.
Keywords-Delay Tolerant Networks, Malicious Node, Flooding Attack, Buffer Resource, Bandwidth.
I. INTRODUCTION
Network environments where the nodes are characterized by intermittent and opportunistic connectivity are referred to as delay tolerant networks. Due to lack of consistent connectivity, two nodes can only exchange data when they move into the transmission range of each other (which is called a contact between them). DTNs employ such contact opportunity for data forwarding with “store carry-and-forward” [1] i.e., when a node receives some packets, it stores these packets in its buffer, carries them around until it contacts another node, and then forwards them. In DTN, a node may store a message in its buffer and carry it along for long periods of time, until an appropriate forwarding opportunity arises. Additionally, multiple message replicas are often propagated to increase delivery probability. This combination of long-term storage and replication poses a high storage overhead thus; we need to discuss for efficient message delivery with much significance of buffers space in nodes.
Buffering and forwarding unlimited number of messages may also cause intolerable resources and nodal energy consumption; Nodes have buffer limitations as DTN nodes are battery-powered device with stringent limitations on buffer space and power consumption. With such limitations at the DTN nodes, message drop/loss could happen due to buffer overflow. This leads to a big challenge in the implementation of most previously reported DTN routing schemes document is template.
The researchers have focused on various issues like reducing the delivery delay or increasing the delivery. Optimizing resource usage, providing scalability etc are also issues explored by various algorithms. Each of them has its own merits and demerits and is suitable in certain domains. Buffer size has great impact on various factors like message delivery, delay and overhead. In this paper, we examine effect of buffer size on message delivery, overhead and average delay and found that with the increase in buffer size message delivery ratio increases. So it concludes that buffer space is a very crucial resource and should be used optimally. Many malicious nodes target to misuse the buffer space so as to deplete network resources and thereby hamper network delivery ratio.
In DTNs, malicious nodes can arbitrarily insert bogus messages in the network. If innocent routers further propagate these forged messages, the attacks may generate large amounts of unwanted traffic to the network. Due to resource-scarcity characteristic of DTNs, the extra traffic may pose a serious threat on the operation of DTNs [4]. Further, unauthorized access and utilization of DTN resources are another serious concern in terms of DTN security.
International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 7, July 2014)
330 Therefore, it is urgent to secure DTNs against flood attacks. In the paper, we have categorized different types of flooding attacks that can be there in network. Also we have classified the attacks as per the protocols design. As in Prophet Protocol [10] malicious node exploits the delivery predictability of victim nodes and uses it to choose the victim node to get flooded.
The remainder of this paper is organized as follows Section III shows the preliminaries and section IV as related work. Section V presents impact of Buffer size. Section VI describes various flooding attacks on buffers. Section VII gives simulation results. We summarize the work in Section VIII.
II. PRELIMINARIES
In this section, we briefly explain routing protocols [17, 16, 10, 2] which are used in this paper to present significance of buffer space on performance of network.
Epidemic routing [17] based on flooding strategy is a very basic routing algorithm used in DTNs. As per routing policy of epidemic routing, it requires a node to flood messages in its buffer to all other nodes which come in its contact. Further, nodes receiving messages also transmit their messages to nodes that comes in their contact. Flooding used on contact in epidemic routing results in maximal spreading of the messages throughout the network and therefore achieves high delivery probability. However, it consumes a lot of resources.
Spray and Wait routing proposed by Spyropoulos et al. [16] improves epidemic routing by restricting number of copies of a message which are being spread throughout the network. Improved method comprises of two phases, spray phase and wait phase. In spray phase, the source node first forwards „L‟copies of a message to first „L‟ encountered nodes and then goes to the wait phase. In the wait phase, all nodes those received a copy of the message wait to meet the destination node directly to deliver data to it. Though Spray and Wait routing works a bit like epidemic but it restricts the amount of copies that are spread in the network. Thereby it restricts the excess use of resources. However, it has less delivery ratio compared to that of epidemic routing.
Probabilistic routing using history of encounters and transitivity (PRoPHET): PRoPHET proposed by Lindgren et al. [10] makes forwarding decisions based on strategy which uses delivery predictability of node in contact with respect to destination of message to being forward. Each node maintains the delivery predictability of every other contacted node for all known destinations.
When nodes meet each other, they exchange their delivery predictability information tables. In addition to delivery predictability of node in contact, PRoPHET also uses transitivity information to decide the next hop. PRoPHET incurs much lower communication overhead than epidemic.
MaxProp Routing [2]: MaxProp routing attempts to forward the message to node that has the greater probability to deliver the message to its destination. It calculates the path for each message at each transfer opportunity using a modified Dijkstra algorithm with history as a criterion. MaxProp defines its own way of computing history to dictate the path computation. It incorporates a mechanism of message queuing at peer level. It prefers the newly born messages and degrades the priority of messages based on their delivery probability and the number of hops they have traveled. It uses a heuristic, which in case of bandwidth deficient environment, prefers to forward those messages that have not been able to travel farther from their respective sources. MaxProp routing uses priorities assigned to the messages based on hop count and delivery likelihood of a node in contact to make routing decisions. In a sense, MaxProp is a history-based controlled flooding routing approach.
In next section, we present work done on problems similar to our problem of flooding attack as a consequence of buffer space misuse.
III. RELATED WORK
International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 7, July 2014)
331 As per application requirements, buffer usage policies tune according to low delivery delays or high delivery ratio. Proposed policies need information of topology of network to tune that is gathered by statistical learning. Elwhishi et al [3] also proposed a message scheduling framework to optimize use of buffer space in DTNs. Authors have shown need of buffer management modules to achieve peak throughput. However there is also need to study scenarios where misbehaving node may present in network and may fail these techniques by injecting erroneous messages. In [8] Lee et al. defined different models of flooding attack for probabilistic routing protocols and discussed a queuing mechanism for minimizing impact of attack. When buffer of „node under attack‟ gets full by injected bogus messages, queuing mechanism finds misbehaving node using a metric based on number of encounters and its delivery predictability. This technique starts mitigating attack when attack is at its full potential and buffer of „node under attack‟ gets full. A mechanism that isolates the malicious node before degradation of network performance because of buffer space may help in a better way.
Natarajan et al. [12] defined two types of flooding attacks and proposed a probabilistic scheme using a gateway node as watchdog node to mitigate the attacks. In first type of attack they considered the scenario where a malicious node creates copies of different messages however in second type, malicious node creates copies of same message to flood the network. For mitigation of both type of attacks, a gateway node keeps track of number of messages generated by a node in a time interval and count of number of copies of each message. In case, gateway node finds more than allowed number of copies, it reports the presence of attack. Li et al. in [9] extend idea of counting number of messages generated by each node in a distributed manner rather than centralized approach based on gateway node as proposed by Natarajan et al. [12]. [7] used proxy signatures for handling overuse of buffer space by malicious nodes as well as legitimate nodes for defined specific scenarios. One of defined scenarios is where destination node needs to send the bundles in response of source request. In this scenario, a malicious node may send forge bundles for any randomly chosen destination and thus perform flooding attack. Authors suggested to extend affiliation of bundles sent by destination node in response of source request by using proxy signature on behalf of source node (empowered by source node) that further can be verified by hop-by-hop nodes to restrict the malicious node as well as the legitimate node for overusing the buffer space.
IV. PROBLEM STATEMENT:IMPACT OF BUFFER SPACE
In this section, we show the impact of buffer space on performance of routing protocols. As per requirement of DTN compliance applications, bundle layer is proposed to keep the bundles in buffer till the competent node comes in contact of node which is storing the message to deliver. Many buffer management techniques have also been proposed to prioritize the messages in buffer to increase the message delivery and thereby to improve the network throughput. To meet the purpose of idea presented in this paper we propose to measure performance of routing protocol in terms of measures, (i) Message Delivery Ratio (MDR), (ii) Message Overhead, (iii) Average Message Latency(AML), and (iv) \% of dropped messages with varying buffer space of nodes. MDR is the ratio of total number of messages delivered to their destination to total number of created messages at source node. Message Overhead is the ratio of number of messages relayed to number of delivered data packets and Average Message Latency is ratio of sum of delays (delivered time-creation time) to number of delivered data packets.
TABLE I
Impact of Buffer space on Message delivery ratio (% increase).
Protocols/ %
100% 400% 900% 4900%
Epidemic 27% 66% 110% 145%
Prophet 15.19% 35% 86% 87%
MaxProp 37.53% 88% 88% 110%
Spray and Wait 14.84% 27.37% 27% 28%
Table I shows impact of buffer size on message delivery ratio of routing protocols. It is clear from the table that the packet delivery improves significantly of all the protocols as buffer size increase. In all protocols, on arrival of new packet the oldest packet is removed from the buffer (in case if buffer is full). Epidemic protocol gains a lot in terms of message delivery if buffer size is increased and so is the case with PRoPHET and MaxProp but In Spray and Wait, the messages are very less relayed so there is no need of much buffer space.
International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 7, July 2014)
[image:4.612.56.281.160.282.2]332 TABLE III
Impact of Bufferspace on Overhead (% decrease).
Protocols/ %
100% 400% 900% 4900%
Epidemic 15% 12% 44% 64%
Prophet 9% 23% 37% 60%
MaxProp 17% 40% 51% 57%
Spray and Wait 12% 19% 23% 23%
Table II shows impact of buffer size on message overhead. Message overhead also improves significantly of all the protocols as buffer size increase. Message Overhead decreases as nodes are able to accommodate more messages with increase in buffer space and thereby more messages are delivered which improves the message.
TABLE IIIII
Impact of Bufferspace on Message Latency (% increase).
Protocols/ %
100% 400% 900% 4900%
Epidemic 34% 65% 74% 139%
Prophet 57% 114% 114% 173%
MaxProp 22% 62% 99% 99%
Spray and Wait 52% 146% 152% 152%
Table III shows the impact on Average Message Latency (AML) with respect to buffer size. As the buffer size increases, more messages are stored in the buffer and so older messages are not dropped but delivered with some delay that adds to total latency.
TABLE IVV
Impact of Bufferspace on no. of dropped messages(% decrease).
Protocols/ %
100% 400% 900% 4900%
Epidemic 2% inc 3.30% 24% 100%
Prophet 0.90% 16% 38% 100%
MaxProp 0.28% 44% 24% 100%
Spray and Wait 13% 51% 89% 100%
Number of dropped messages are decreased with increase in buffer space but MaxProp gains largest in saving the dropped messages with increase of buffer space in comparison to others as clear from Table III. However, if buffer space is large enough to accommodate all received messages as consequence no message is dropped. For all protocols there is 100% decrease in dropped messages with 4900% increase in buffer space.
We conclude from above observations that buffer is an important resource in DTNs and impacts the performance of routing protocols. Thus any action which leads to improper use of buffer space may hamper routing performance and consequently may degrade the performance of overall network. In this paper we present the possible ways wherein a misbehaving node flood the forwarder or potential forwarder nodes in network with bogus or replicas of genuine messages to exploit buffer space and thereby degrade the throughput as in terms of aforementioned measures.
V. FLOODING ATTACK
Routing in DTNs relies on the fact that nodes cooperate with each other to forward messages. As in real scenarios, all nodes in a network are not very cooperative. There are also some malicious nodes in the network where prime purpose of these malicious nodes is to perform attacks and to reduce the amount of packets which are being delivered to their intended destinations. To achieve their purpose, adversaries need some strategies so that packets are not able to traverse through network and to finally reach to their destination. As discussed in last section, buffer space is an important resource in DTNs. Buffer space is used to store the messages till node comes in contact of potential forwarder. A strategy which leads to scenario where in buffer space most of the time is occupied by bogus or by copies of genuine messages more than generated by legitimate nodes may disrupt genuine packets to traverse as it is the bogus message or unintended messages which are traversing most of times. In this section, we present „flooding attack‟, possible types of „flooding attack‟ and different strategically models of „flooding attack‟ which exploit buffer space to degrade message delivery and thereby other measures of network performance.
International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 7, July 2014)
333 In this paper, our aim is to present various strategies which can be used to model flooding attack. We emphasis that attacker may heavily use routing protocol as a part of its strategy to launch the flooding attack. In first type of models attacker strategically is not dependent on routing protocol while in second and third type of models attacker strategically uses routing protocol.
[image:5.612.352.545.229.380.2][image:5.612.77.260.237.383.2]
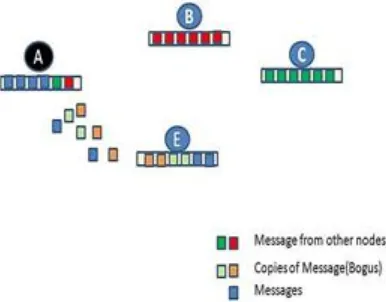
Figure 1: Impact of flooding attack in beginning stage
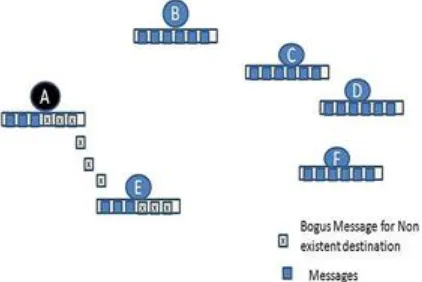
Figure 2: Impact of flooding attack in later stages
A. Flooding Attack(Model1)
In first type of model, we categorize flooding attack as
packet flood attack, replica flood attack, and resource-misuse attack depending upon how genuine data is stopped or dropped from buffer space.
In packet flood attack (also known as a breadth attack) [12], [9] and [5] a node flood the target nodes with a large quantity of useless data (a denial-of-service attack launched by a malicious node) where useless data is generated by attacker using multiple copies of different genuine messages received from other honest nodes in network.
Figure 3: Packet flood attack or breadth attack.
[image:5.612.76.258.407.574.2]In replica flood attack (also known as Depth Attack) [12], [9] and [5] node generates more data than allowed by the network, to increase its throughput and to decrease the latency of its packets (disallowed data generation by a selfish node). Here main aim of misbehaving node is to misuse buffer space of network for its own use rather than to degrade the performance but in turn this also degrades the performance for other users.
[image:5.612.351.533.501.651.2]International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 7, July 2014)
334
Resource-misuse attack [12] uses rare contact opportunities between nodes to transfer bogus data thereby, misusing the limited network bandwidth of the legitimate nodes and causing eviction of regular data packets from the buffers of the legitimate nodes. The network throughput of the DTN decreases considerably due to the effect of resource-misuse attacks. Mobile nodes spend much energy on transmitting/receiving flooded packets which may shorten their battery life.
B. Flooding Attack Model2
Flooding attack on routing protocols:
This type of model is specific to routing protocols where routing protocol defines rules to exchange messages between nodes in contact for intended destinations specified in messages to exchange. As if node in contact is malicious node it may receive genuine messages and create bogus messages including genuine destination nodes ids as well as genuine source node ids which it knows from earlier received genuine messages. Bogus messages generated using this type may be difficult to identify by honest node and consequently honest node occupy bogus messages in its buffer till it meets target destination node or any potential forwarder node. Flooding attack is categorized in [8] as Random flooding and Spoof Flooding depending upon how bogus message is created using genuine source or destination node ids. This type of attack impacts all types of routing protocol however this model impacts largely epidemic and spray and wait like protocols that are based on flooding or controlled flooding strategy and allows multiple copies of same message.
[image:6.612.339.545.346.487.2]Random Flooding: In this approach, malicious node continuously creates fake messages for randomly selected destination nodes. As here shown in Figure 5, Node A randomly chooses Node E as destination node of fake messages for flooding attack.
Figure 5: Random attack in flooding.
[image:6.612.64.269.568.699.2]Spoof Flooding: A trickier approach of flooding attack is spoofing identities of honest nodes by a malicious node present in network and includes those corresponding identities in generated fake messages. By including spoofed identities of genuine sources in network for the fake messages created, the malicious node can bluff victim node to think that the messages are from different sources. In this manner, it would be difficult for the nodes in the network to trace and detect the messages. To further mask the attack, randomly selected genuine destinations are set in generated fake messages for attack. These fake messages will diverge and travel in different paths, and therefore will not be easily detectable. Moreover, this trick magnifies the impact in comparison to random flooding as many times as many sources will be spoofed which in turn will speedily reduce the actual buffer capacities of nodes. Figure 6 shows a possible scenario for of spoof flooding attack.
Figure 6: Spoof attack in flooding. Here Node A spoofs as Node B or Node C.
C. Flooding Attack Model 3
International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 7, July 2014)
335 Possible types of flooding attacks in probabilistic as defined routing protocols in [8] are as following:
[image:7.612.336.542.127.292.2]Selective Flooding: Upon meeting a victim, the malicious node will transfer the fake messages that the victim has a higher predictability of delivering to the destinations. After this, the fake messages will be further relayed through the victim‟s peers until the messages reach their destinations. The relaying process causes fake messages directed into different paths since they are destined for different nodes.
Figure 7: Selective attack in flooding
[image:7.612.64.277.263.427.2]Selective Active Nodes Flooding: This attack aims at flooding selective targets. The node that has the highest involvement is a noteworthy node that is highly active in the network and hence is the favoured target. For all of PRoPHET‟s nodes, by summing the delivery predictabilities, the malicious node knows which nodes are actively having frequent meetings with the rest. The node with the highest sum is the most active node among all, and so it will be the selected victim. Thereafter, the malicious node will create fake messages to flood the victim. To increase the likelihood of the fake messages being forwarded to the victim, the malicious node will set the destinations for the fake messages to be the node which the victim has the highest delivery predictability.
Figure 8: Selective active node attack in flooding. Node A selects Node E as a active node that participates maximum in the network
In case of MaxProp, the number of encounters made determines the probabililty of the node, so the malicious node will create bogus messages to flood the node with highest encounters.
Non-Existent Destination Node Flooding: Flooding attack may have a more complicated move which involves the malicious node setting the destinations for the fake messages to be a non-existent node. Unlike previous attacks, the fake messages will never reach their destinations, and hence it achieves the purpose of making the fake messages remain longer in the network. In order to bluff the victim to accept the fake messages, the malicious node has to increase the victim‟s delivery predictability for the non-existent destination node. This is achieved by exploiting the transitive property of the PRoPHET protocol. The fake messages will stay in the network till they time out or are discarded by the queuing policy implemented.
[image:7.612.340.551.542.683.2]International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 7, July 2014)
336 VI. SIMULATIONS
[image:8.612.323.565.136.276.2]We simulated our algorithms using the Opportunistic Network Environment (ONE) simulator [6] implemented in Java. For simulation purposes reality dataset [14] is taken from crawdad data. There are total 36 nodes in the network. 20 nodes are pedestrians and 16 nodes are trams. Table 5 shows the parameters used in simulations.
Table 5 Simulation Parameters
Parameter name Value
TTL 300 sec
Simulation time 100000 (sec)
Messages generated 3886
Message Size 500kB - 1MB
Experimental results on Crawdad dataset:
Figures 10, 11, 12 and 14 presents comparison of results for Message Delivery Ratio, Message overhead and Latency with varying buffer size.
Figure10: Message Delivery Ratio of routing Protocols on Crawdad dataset with varying buffersize.
Figure 10 shows the impact of buffer size on message delivery ratio of various routing protocols. It is clear from the figure that the packet delivery improves significantly as buffer size increase. In Epidemic protocol , on arrival of new packet the oldest packet is removed from the buffer (in case if buffer is full). So Epidemic protocol gains a lot in terms of message delivery if buffer size is increased. So is the case with Prophet and MaxProp but In Spray and Wait & First Contact Router, the messages are very less relayed so there is no need of much buffer space.
[image:8.612.63.273.234.370.2]Figure 11: Overhead of routing of routing protocols with varying buffersize on Crawdad dataset.
Figure 12: Latency of routing of routing protocols with varying buffer size on Crawdad dataset
Figure 13: Dropped messages of routing protocols with varying buffer size on Crawdad dataset
VII. CONCLUSION
[image:8.612.50.289.430.569.2]International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 4, Issue 7, July 2014)
337 Flooding Attack with different strategies targets the victim nodes and misuse their buffer space, which in turn also impact usage and performance of other resources. These kinds of attacks are waste the precious bandwidth and buffer resources. Also, the mobile nodes spend higher energy for transmitting and receiving flooded packets and replicas results weak battery life. Hence, there is need for a secure method to prevent the DTNs against flood attacks.
Moreover, impact of strategy becomes more severe as it leads to more occupancy of buffer with bogus or replica of genuine messages. So, if while receiving the message from node in contact we follow the node's past behavior in the network to accept the message or not can help to mitigate flooding attack.
REFERENCES
[1 ] Dtnrg. delay tolerant networking research group: dtn-interest mailing list archive. In Available from http://mailman.dtnrg.org/pipermail/dtninterest/2005- April/., 2005. [2 ] J. Burgess, B. Gallagher, D. Jensen, and B. N. Levine. Maxprop:
Routing for vehicle-based disruption-tolerant networks. In INFOCOM 2006. 25th IEEE International Conference on Computer Communications. Proceedings, pages 1 {11, april 2006.
[3 ] A. Elwhishi, P.-H. Ho, K. Naik, and B. Shihada. A novel message scheduling framework for delay tolerant networks routing.volume 24, pages 871{880, May 2013.
[4 ] S. Farrell and V. Cahill. Security considertions in space and delay tolerant networks. In In Proc. of SMC-IT06, 2006.
[5 ] L. X. Iswariya. A secure communication model to detect flooding attacks in disruption tolerant networks. In International Journal Of Engineering And Computer Science, 2014.
[6 ] A. Keranen, J. Ott, and T. K. inen. Theone simulator for dtn protocol evaluation.In Proceedings of the 2nd International Conference on Simulation Tools and Techniques, SIMUTools 09, 2009.
[7 ] A. Krifa, C. Barakat, and T. Spyropoulos.Optimal management policies for delay tolerant networks. In Sensor, Mesh and AdHoc Communications and Networks, 2008.SECON '08. 5th Annual IEEE Communications Society Conference on, pages 260{268,June 2008.
[8 ] F. C. Lee, W. Goh, and C.-K. Yeo. A queuing mechanism to alleviate flooding Attacks in probabilistic delay tolerant networks. In Telecommunications (AICT), 2010 Sixth Advanced International Conference on, pages 329{334, May 2010.
[9 ] Q. Li, W. Gao, S. Zhu, and G. Cao. To lie or to comply: Defending against flood attacks in disruption tolerant networks. volume 10,pages 168{182, May 2013.
[10 ]A. Lindgren, A. Doria, and O. Schelen. Probabilistic routing in intermittently connected networks. SIGMOBILE Mobile Computing and Communications Review, 7, 2003.
[11 ]V. Mahendran, T. Praveen, and C. Murthy.Buffer dimensioning of delay-tolerant network nodes - a large deviations approach. In L. Bononi, A. Datta, S. Devismes, and A. Misra, editors, Distributed Computing and Networking, volume 7129 of Lecture Notes in Computer Science, pages 502{512. Springer Berlin Heidelberg, 2012.
[12 ]V. Natarajan, Y. Yang, and S. Zhu. Resource-misuse attack detection in delay tolerant networks. In Performance Computing and Communications Conference (IPCCC), 2011 IEEE 30th International,pages 1{8, Nov 2011.
[13 ]A. H. A. Qaisar Ayub, M soperi Mohd Zhhid* and S. Rashid. Connection frequency buffer aware routing protocol for delay tolerant network. J Electr Eng Technol, 2013.
[14 ]J. Scott, R. Gass, J. Crowcroft, P. Hui, C. Diot, and A. Chaintreau. Crawdad data set cambridge/haggle (v. 2009-05-29). In Downloaded fromhttp://crawdad.cs.dartmouth.edu/cambridge/haggle, May 2009, 2009.
[15 ]V. Soares, F. Farahmand, and J. Rodrigues. Evaluating the impact of storage capacity constraints on vehicular delay-tolerant networks. In Communication Theory, Reliability, and Quality of Service, 2009. CTRQ'09. Second International Conference on, pages 75{80, July 2009.
[16 ]T. Spyropoulos, K. Psounis, and C. S.Raghavendra. Spray and wait: An efficient routing scheme for intermittently connected mobile networks. In Proceedings of the 2005 ACM SIGCOMM Workshop on Delay-tolerant Networking, WDTN '05, pages 252{259, New York, NY, USA, 2005. ACM.
[17 ]A. Vahdat and D.Becker. Epidemic routing for partially connected ad hoc networks. In Technical Report CS-200006 Duke University, 2000.