Viewpoint
Public cloud vendors: security ranking and
positioning analysis
By Edward Hamilton (Senior Manager)
April 2011
Executive summary
The market for cloud services is growing rapidly, but players in several highly regulated industry verticals (such as government and finance) appear not to be adopting general cloud services – primarily because of concerns over security, regulatory compliance and governance issues. Instead, they are either dismissing the business opportunity or defining private clouds, which removes a significant portion of the potential cost reduction benefits that cloud services offer.
Our analysis of the security offered by a range of cloud service providers revealed that, in most cases, it largely focused on:
technical security controls – which are necessary but not sufficient for enterprises because security must be a balance of different types of security control, including people, process and technology
compliance with legislation and regulation in the USA – which is an important market, but concentrating solely on it limits the opportunities for cloud service providers.
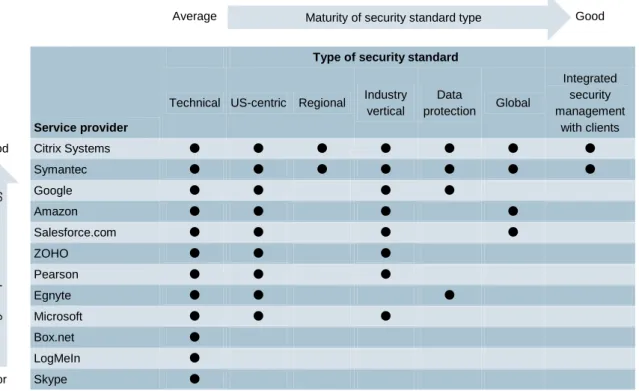
Some providers have numerous security certifications, but the alignment and strategy behind those certifications do not enable them to increase their addressable market significantly. Each certification costs time and money to maintain, so cloud service providers need to ensure that they are obtaining the maximum benefit from each certification. Figure 1 shows our assessment of providers’ approach to security certification.
Table 1: Assessment of the security certification strategy of a selection of cloud service providers [Source: Analysys Mason, 2011]
Average Good
Service provider
Type of security standard
Technical US-centric Regional Industry vertical Data protection Global Integrated security management with clients
Good Citrix Systems
Symantec
Google
Amazon
Salesforce.com
ZOHO
Pearson
Egnyte
Microsoft
Box.net
LogMeIn
Poor Skype
Key: = Provider complies with security standards of this type.
Citrix Systems and Symantec have comprehensive documentation that outlines their end-to-end security strategies. These start with the technical security controls, but also include a range of security certifications that cover regions, global and industry verticals. The two providers’ strategies also discuss risk management and working with clients’ own security teams. Other providers may have similar strategies, but documentation about them is not easily accessible. Security professionals will assume that risks have not been mitigated until suitable evidence can be supplied.
Recommendations for cloud service providers
Concentrate on certification to international security standards that are applicable worldwide. Many service providers focus on compliance with US regulations and standards. They will need to broaden their scope to include internationally recognised standards if they are to address the enterprise market effectively. We recommend ISO 27001, Payment Card Industry Data Security Standard (PCI DSS), ISO 22301 and the Data Protection Act/Safe Harbour. Providers should also map country- and industry-vertical-specific security controls back to ISO 27002:2005 to demonstrate compliance to country-based vertical security requirements.
Ensure the suitable security documentation is readily available. The information must offer more than high-level sales and marketing messages, or it will be dismissed as such. Service providers must ensure that they provide suitable security information to potential clients, enabling them to quickly and easily ascertain the level of security maturity of the cloud service being offered.
Enable internal enterprise security teams to integrate with cloud service provider security teams. Service providers should develop their security operating procedures to enable collaboration between their security teams and those of their clients, allowing them to share information about threats, risks and incidents.
Maturity of security standard type
S tr en gt h of p ro vide r’s s tr at eg y
Organisations in the government and banking sectors already include this feature in their outsourcing contracts. If cloud service providers wish to enter these markets, they have to be able to offer the same or better levels of security. Internal enterprise security teams must have the utmost assurance that security compliance is met and escalation processes are in place to deal with all breaches appropriately and quickly.
Forecast
Analysys Mason forecasts that revenue from the public cloud services market will grow from USD12.1 billion in 2010 to USD35.6 billion in 2015 (see Figure 1). Software-as-a-service (SaaS) currently accounts for the majority of revenue, but the balance will shift towards infrastructure-as-a-service (IaaS) during next five years.
Figure 1: Enterprise cloud-based service revenue, worldwide, 2010–2015 [Source: Analysys Mason, 2011]
Public cloud service providers must ensure that their security is appropriate for global markets to achieve this anticipated revenue growth. If they do not, enterprise organisations and governments will continue to deploy private cloud solutions.
Market leaders
We considered a range of providers, from market leaders to relatively new entrants. We reviewed the offerings of Amazon, Box.net, Citrix Systems, Egnyte, Google, LogMeIn, Microsoft, Pearson, salesforce.com, Skype, Symantec and ZOHO. Citrix and Symantec clearly differentiated themselves as the market leaders. They demonstrate a detailed understanding of information security and assurance in a range of global verticals. Their documentation discusses the technical controls, security and risk management, and how their services integrate with clients’ own security teams.
Cloud service providers’ technical security infrastructure appears to follow good technical practices. However, security is significantly poorer at an application level and is almost non-existent when it comes to security governance. In particular, most cloud service providers have yet to clearly define how their security governance would link to and integrate with a client’s security team. For example, it is not clear how providers will report any data breaches they detect. Waiting to include such news in a monthly status report would not provide a
0% 5% 10% 15% 20% 25% 30% 35% 40% 45% 0 5 10 15 20 25 30 35 40 2010 2011 2012 2013 2014 2015 Y e a r-on -y e a r g ro w th ra te Rev e n u e (USD b ill io n ) Revenue Growth
suitably timely level of security governance for enterprises. Cloud service providers need to offer integrated security governance that allows two-way communication to a defined service-level agreement.
Most of the security standards that these service providers support are designed to comply with US regulation and legislation (see Figure 2).
Figure 2: Security standards followed by a selection of cloud service providers, by region1 [Source: Analysys Mason, 2011]
SAS 70 was the most-commonly adopted security standard among the service providers we considered (see Figure 3). SAS 70 is useful for organisations that are based in, or have their headquarters in, the USA. Most cloud service providers are US-based and need to comply with this standard, so it makes sense for them to extend their audits to include service provision. Some providers are moving towards adoption of more internationally recognised security certifications, mainly the de facto global security standard ISO 27001.
Figure 3: Security standards followed by a selection of cloud service providers1 [Source: Analysys Mason, 2011] US standards 71% International standards 26% Other regional standards 3% 0% 10% 20% 30% 40% 50% 60% 70% Data Protection COBIT FISMA HIPAA NIST Safe Harbour ISO 27001 SOX PCI DDS SAS 70
Many of the region- and vertical-specific security standards are based on the security controls defined in ISO 27002 (the security control set for ISO 27001). Complying with and being certified to ISO 27001 enables providers to support a common, globally accepted security baseline and to add additional security controls to enable compliance with specific national, regional, or vertical security requirements.
Market drivers and inhibitors
The following factors are driving adoption of cloud-based solutions in the enterprise sector.
Lack of IT staff. Small enterprises in developed markets rarely have enough IT staff to manage on-premises technology, and the staff they do have are generalists rather than specialists in particular applications or infrastructure components. In emerging markets, finding skilled IT staff is difficult. Cloud solutions remove the need for SMEs to have deeply technical IT staff dedicated to one particular on-premises technology solution.
High cost of skilled IT talent in developed markets. Especially in developed markets, the cost of highly skilled IT staff often makes the total cost of ownership of on-premises solutions unreasonably high. Switching to cloud solutions reduces an enterprise’s reliance on these difficult-to-find and expensive resources.
Consumer adoption of social networking and consumer cloud solutions. Consumers will become more comfortable with the online application experience as they become more accustomed to cloud-based solutions such as social networks (for example, Facebook and MySpace), hosted email and calendaring, and PC-based telephony (for example, Skype). These consumer tools encourage the building of online communities and collaboration. Consumers’ comfort with these tools builds a willingness to consider and adopt enterprise cloud solutions.
Move towards simplifying the network and technology environment. Real-time access to applications across the company can be an unreachable goal for businesses with multiple office locations – especially small businesses. Maintaining a networked application environment is too complex and expensive for small enterprises. Those that attempt it often suffer a low quality of service, high levels of downtime and high support costs. Cloud solutions remove the complexities of maintaining networked application environments, making an application available from virtually any laptop or desktop with broadband Internet access.
Remote working and mobility. More than 50% of employees work outside their primary workspace at least one day per week. Having access to applications in multiple work environments is key to ensuring continuity of stakeholder interactions. For example, Vodafone is finding that SMEs want cloud solutions to ensure that they never miss a call from a customer or prospect. Such a simple, yet profound, business need – not elaborate features and rich product functionality – quite often drives the adoption of a new technology.
Capital limitations. In these particularly difficult economic times, when credit is very tight, businesses prefer to purchase solutions on a pay-as-you-go basis, rather than make relatively large capital expenditures. Spreading out the payments related to a technology solution is one form of financial and business risk diversification for enterprises.
Network operators’ desires to gain greater technology wallet-share with established customers by following their traditional business model (that is, monthly recurring revenue). Vodafone, for example, increases its share of an SME’s technology wallet from 30% to 80% by adding cloud services to an existing mobile or fixed network service customer. By selling additional cloud services with three-year terms, Vodafone is able to increase the average customer lifetime. and decrease churn on its core connectivity product lines. This incremental lifetime value of the mobile or fixed network customer has a tremendous impact on margins.
However, several factors are inhibiting the adoption of cloud-based solutions, one of which is security. Data is a key information asset for many organisations, and transferring a key asset to a public IT system where the security is unknown requires significant faith in the supplier. Organisations do not trust other organisations, so providers must demonstrate that they will secure their clients’ information assets to an appropriate security level to mitigate the identified risks.
Business environment
The move towards cloud services appears to be relentless, as numerous players develop and deploy additional IT platforms, infrastructure and applications. Cloud IT services is a natural development of IT outsourcing and organisations’ desire to reduce IT costs. They appear to have all the benefits of outsourcing without the traditional risks of customised IT development or COTS deployment, for the following reasons.
The services and applications already exist and have been deployed, which minimises the risk of incurring the cost overruns that affect so many IT projects.
Most cloud-based IT services require no capital investment and have only minimal upfront configuration charges, which enables enterprises to budget annually for the services.
Enterprises require little in-house IT skills to use cloud-based services, which enables them to redeploy valuable IT assets elsewhere.
The services can be deployed quickly, which allows enterprise IT departments to become more responsive to stakeholders and focused on business needs rather than IT minutiae.
Enterprises will encounter additional risks when making the transition to, and using, cloud services. Some of these are related to security – for example, compliance with the required legislation and regulation within their country, region and industry, as well as the usual security concerns about the confidentiality, integrity and availability of data.
A mature security solution will strike a balance between technical security controls and a security governance set, consisting of policy, procedures and standards. Currently, most cloud service providers are not providing suitable security governance for organisations that operate in highly regulated or complex legislative environments.
Many service providers’ security compliance standards are very US-centric. The USA is the largest single economy in the world, but the business case for developing cloud-based services will nevertheless be weaker if the service provider focuses solely on this market. To address other markets, providers will need to address international and other regional standards. Organisations in highly regulated sectors might conclude that cloud services do not offer appropriate security after performing a simple search on the available services and their security compliance standards. As a result, they are designing and implementing their own clouds – for example, many governments are designing their own clouds that adhere to security standards they have defined.
Market definition
For this work, Analysys Mason utilised the National Institute of Science and Technology’s (NIST’s) definition of cloud services.1 We reviewed a selection of cloud service providers’ offerings.
1 See NIST (Gaithersburg, Maryland, 2009), The NIST Definition of Cloud Computing. Available at http://www.nist.gov/itl/cloud/upload/cloud-def-v15.pdf.
![Figure 1: Enterprise cloud-based service revenue, worldwide, 2010–2015 [Source: Analysys Mason, 2011]](https://thumb-us.123doks.com/thumbv2/123dok_us/8688395.2350410/3.892.169.732.376.734/figure-enterprise-service-revenue-worldwide-source-analysys-mason.webp)
![Figure 2: Security standards followed by a selection of cloud service providers, by region 1 [Source: Analysys Mason, 2011]](https://thumb-us.123doks.com/thumbv2/123dok_us/8688395.2350410/4.892.265.657.276.592/figure-security-standards-followed-selection-service-providers-analysys.webp)