International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 5, Issue 7, July 2015)
508
Hand Palm Identification by Using Image
Processing Techniques
Baki KOYUNCU
1, Yasemin GÖKALP
2Computer Engineering Department, Ankara University, Ankara, Turkey
Abstract--- An image processing technique based on filtering and cross correlation techniques is proposed for hand palm identification in this study. Line features of hand palm are deployed for biometric palm recognition. Principle line features are extracted from hand palm image and compare to line features of other hand palm images. Any similarities over 95% is considered as a match. Different image processing techniques are employed to mask, clear and bring forward the hand palm information of line features. Cross correlation algorithm is used to determine the similarities between these line features. Results are presented as percentage match. In the study, identical palm prints display 98% match while non identical palm prints give 10% to 25% match. The technique introduced here emphasizes the cross correlation technique and gives good results compare to other techniques in literature.
Keywords-- Bio-metrics, principal lines, RGB, Cross Correlation method, Median Filter, Maximum Curvature, Kernel,Morphology
I.INTRODUCTION
Personal authentication is an important part of the security systems. Traditional authentication methods include passwords, pin numbers, key codes and cards in security markets. Unfortunately these well know methods are easy to break or duplicate for criminal purposes.
Bio-metrics techniques, on the hand, are unique techniques based on specific human characteristics and very difficult to replicate and use for criminal purposes. Bio-metrics technique [1-3] is a method which recognize unique human features or other human characteristics. Theoretically any human physical and behavioral characteristics can be deployed as bio-metrics to satisfy the requirements of permanence, universality, uniqueness and collectability [4].
Physical bio-metrics which are used to verify and identify individuals can deploy fingerprints [5], palm prints [6], face [7], iris [8], retina [9] and human DNA [10]. One of the widely used biometric technique employs palm prints. Palm print refers to the image of the palm region of the hand. This image is obtained by scanning the hand palm with a scanner. Palm print image consists of principal lines, wrinkles which are secondary lines and epidermal ridges. It differs from a fingerprint image. It also contains other information such as texture, indents and marks and it has a larger area with more details. This characteristic is useful when comparing different palm prints with each other.
Throughout the history, examination of hand palm prints was the only method to distinguish one person from another person. Since most of the people could not read and write their own names, their hand impressions on a contract were the only acceptable form of identification. In 1858, Sir William Herschel, working for the Civil Service of India, recorded hand prints of the employees on their contracts to distinguish them from others during the paydays. This was the first recorded systematic capture of hand images for identification purposes [11]. A block diagram of a typical bio-metric authentication system is shown in Figure 1.
[image:1.595.329.533.444.563.2]This paper is divided into 5 sections. In section 2, construction of a palm print is explained. In section 3, line feature extraction is presented. In section 4, hand palm matching is explained. In section 5 experimental results are given. Finally, in section 6, a conclusion is given together with some discussions.
Fig 1. Bio-metric Authentication system
II.PALM PRINT CONSTRUCTION
II A. Palm print Database
International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 5, Issue 7, July 2015)
509 II B. Image Preprocessing
Horizontal colored images in the database are considered one by one and each image I is rotated by 900 clockwise. Secondly, each colored Red-green-blue image is converted to gray scale image by using image processing techniques with MATLAB image processing toolbox.
O = imrotate (I, (angle)) instruction rotates input image by an angle degree in a counterclockwise direction around its center point. O is the resultant output image. Clockwise rotation can be obtained by given a negative value for angle in the instruction.
Imrotate instruction adjusts the size of the output image O so that it includes the entire rotated palm image. Imrotate uses nearest neighborhood interpo- lation and sets the pixel values outside the rotated palm image in O to 0(zero), [13]. See Figure 2.
(a) (b)
Fig 2. (a) original RGB image (b) 900 rotated gray scale image
II C. Masking
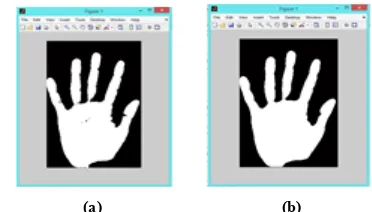
Masking is an image processing technique to extract the object image from a given image. Initially an RGB hand palm image is converted into a gray scale image as seen in Figure 2. Gray scale image is later masked by applying thresholding process.[14]
Thresholding process uses an intensity threshold level across the gray scale image and the intensities below the threshold is identified as 0 and above the threshold is identified as 1. Hence a two stage intensity is generated where 0 is the black background and 1 is the white hand palm image. The pixel intensities are formed as a binary intensity diatribution across the gray scale image. Figure 3 shows the gray scale and masked images.
The pixel information is in binary across the new thresholded image. The objective of binarization is to determine a true black background and a white foreground regions. This way the boundaries of the hand palm image is drawn for further processes. MATLAB algorithm which is used for this masking is given with the below instructions :
level=graythresh(“rotated image ”); Mask=im2bw(“rotated image ”,level);
(a) (b)
Fig. 3 (a) Gray scale image, (b) Thresholded image
II D. Filtering
Filtering is an image processing technique to remove the unwanted noise components from the image. The noise in hand palm image is the shadows and the random pixel variations. In this study, median filtering is used to remove these random variations and enhance the line features in the palm image.
The median filter allows a great deal of high spatial frequency details to pass while remaining very effective for removing noise in images Like the mean filter, the median filter considers each pixel in the image in turn and looks at its nearby neighbors to decide whether or not it is representative of its surroundings. The median is calculated by first sorting all the pixel values from the surrounding neighborhood into numerical order and then replacing the pixel being considered with the middle pixel value, [15]. For example a 3x3 matrix in Figure 4 is sorted from smallest to largest as shown here: -24 -20 -18 -18 -17 -13 13 17 20. Its median -17 is taken and replaced with -24 in figure 4.
(a) (b)
Fig 4. (a) Unfiltered image (b) median filtered image
The above 3x3 image matrix is travelled across the total image in x and y directions and median filtered image matrix is replaced with the original image matrix. Median filtered hand palm image is presented in Figure 5.
[image:2.595.343.522.133.235.2] [image:2.595.51.268.338.453.2] [image:2.595.344.521.495.575.2] [image:2.595.334.520.650.756.2]International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 5, Issue 7, July 2015)
510 II E. Cropping
Image cropping is a process that changes the range of pixel intensity values across the image. New boundaries of the object image is set with cropping. Image cropping ensures that the pixel values in the output image are at the same magnitude as those in the input image. This process provides smaller boundaries for the shape of the hand composed of palm and fingers.
Pixels in the output image beyond the maximum hand boundaries are cancelled. Cropping can result in the output image being slightly smaller, with the edges having been cropped.
Each pixel has (x,y) coordinates according to its position. Upper boundary of image cropping is determined with maximum y coordinate of white pixels (1). Lower boundary of image cropping is determined with minimum y coordinate of white pixels (1). Similar operation is repeated along x directions with white pixels (1). Finally new boundaries are plotted for hand palm image, [16]. See Figure 6.
(a) (b)
Fig. 6 a) masked image b) cropped mask image
III.LINE FEATURE EXTRACTION
In image processing, feature extraction starts from an initial set of measured data and continues to build derived values identified as features. These features are informative and they facilitate the subsequent learning and generalization steps. Feature extraction is related to dimensional reduction.
In this study, a method is proposed to find the line features in hand palm images and only the principal lines are emphasized. The lines are detected by searching for positions where the curvatures of the palm image are locally maximal. The lines are joined with each other, and finally the line network pattern is obtained.
III A. Line Features
Grayscale and masked images which are previously obtained are deployed in the generation of maximum curvature function which extracts the curvature patterns from the palm images.
Maximum curvature function is accomplished by a 2D convolution between a kernel image and an input image. 2D convolution convolves in both horizontal and vertical directions in 2D spatial domain. Masked image is used as the kernel image matrix and gray-scale image is used as the input image.
A mathematical convolution equation is given by the following equation;
jj j
j
j
n
i
m
h
j
i
x
n
m
h
n
m
x
n
m
y
(
,
)
(
,
)
*
(
,
)
(
,
).
(
,
)
Where y[m,n] is.output image(lined image), x[m,n] is input image(grayscale image) and h[m,n] is kernel image(masked image).
Convolution of two matrixes is accomplished. A standard deviation of alpha is assumed with kernel matrix and curvatures are generated. Alpha is used to calculate the derivatives for the maximum curvatures. Kernel matrix, masked image, is firstly flipped in both horizontal and vertical directions. It is later sequentially moved in steps over the gray-scale image matrix.
[image:3.595.51.239.369.514.2]If the kernel matrix is aligned centrally on the input image matrix, then the kernel data is multiplied by the Overlapped input image data. The addition of these multiplications generates the curvature patterns across the hand palm, [17]. These curvature patterns which are final line features are presented in Figure 7.
Fig 7 Final line features of hand palm image
III B Morphology
[image:3.595.397.482.447.543.2]International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 5, Issue 7, July 2015)
[image:4.595.118.198.132.223.2]511
Fig. 8 Hand palm image with only principal Lines
IV.HAND PALM MATCHING
Principle lines of the hand palm image are defined by using above image processing techniques. Furthermore, similarities between different hand palms will be investigated. Various known hand palm images will be stored in a data base and an unknown hand palm image will be compared with this data base. Hence the unknown hand palm image will be identified if a match is scored between data base and unknown palm images.
Cross correlation technique will be deployed to measure the similarity of two images. In pattern recognition, cross-correlation is a measure of similarity between two objects. One object is moved with respect to another object and a maximum similarity between objects generates a maximum signal. A maximum dissimilarity produces a minimum signal. This is also known as a sliding dot product or inner-product. It is commonly used for searching a long signal for a shorter with known feature.
Images with principle lines are two level intensity images with only dark background and bright line intensities. Different hand palm images have different principle lines at different (x,y) coordinates. If the source image is P1(x,y) and the unknown image is P2(x,y),
similarity function S will be the cross correlation of P1(x,y) and P2(x,y).
S has a maximum when PL1(x,y)=PL2(x,y), and it
decreases as the difference between P1(x,y) and P2(x,y)
increases. Cross correlation between two images P1, P2
with principle lines is shown below equation;
x y
v y u x P y x P y
x P y x P v u
S( , ) 1( , )* 2( , ) 1( , ). 2( , )
At the end of the cross correlation, the amount of shift between the known and unknown images define the correlation signal amplitude for matching each other. The maximum signal amplitude is generated to show the maximum similarity. Hence, the percentage of similarity between two images and where the similarity occurs are two information derived at the end of the cross correlation [18].
V. EXPERIMENTAL RESULTS
MATLAB software is employed and an image processing software is developed.
A data base of hand palm images from internet is used to identify unknown hand palm images. One of the hand palm images is taken as the unknown image and compared with the database using the developed software. Figure 9. The software has 2 options 1) single matching ,2) database matching
In the first case , a colored hand palm image is place in the image box on the top left corner of the GUI . Another colored hand palm image is placed in the second image box next to the first box. All the stages of the line feature identifications are carried out for both images and the percentage similarity between them is presented after the cross correlation stage.
Fig 9. GUI of the developed image processing software
In the second case, a known hand palm image in the left top box is compared with the hand palm images in the data base. Any maximum percentage match is displayed on the GUI and its percentage match is given.
Experiments revealed that same hand palm images gives a match of %98.5. On the other hand, dissimilar images give around %10-%15.
VI.CONCLUSION
Biometric refers to metrics related to human characteristics. Biometrics authentication (or realistic authentication) is used in computer science as a form of identification and access control.
It is also used to identify individuals in groups that are under surveillance. Hand palm images are also deployed for identification. Initially hand palm images are subjected to several image enhancements. Once the principle lines are obtained, cross correlation approach is deployed with these lines to match two hand palm images.
This technique has several advantages. The first advantage is that the cross correlation is quite simple to compute between two dark and bright, binary, images. The second advantage is that cross correlation is independent of translations and scaling in the intensity domain. It is also lightly detached with lighting variations. There have been many works in literature which use cross correlation for matching [2] [3].
[image:4.595.326.558.287.427.2]International Journal of Emerging Technology and Advanced Engineering
Website: www.ijetae.com (ISSN 2250-2459,ISO 9001:2008 Certified Journal, Volume 5, Issue 7, July 2015)
512 REFERENCES
[1] N.V. Boulgouris, K.N. Plataniotis and E. M. Tzanakou,
“Biometrics: Theory, Methods and Applications”, Wiley-IEEE Press, ISBN:978-0- 470-24782-2,2009.
[2] James Wayman, Anil Jain et. al, “Biometric Systems: Technology,
Design and Performance Evaluation”,Springer,ISBN-13: 978-1852335960, 2004.
[3] Mahfuzur Rahman, and Prabir Bhattacharya, “Secure Network
Communication Using Biometrics,” IEEE International Conference on Multimedia and Expo (ICME'01), p. 52, ISBN: 0-7695-11988, 2001.
[4] Shaila K. Dewan, “Elementary, Watson: Scan a Palm, Find a
Clue,” The New York Times, 21 November, 2003.
[5] Nalini Ratha and Ruud Bolle, “Automatic Fingerprint Recognition
Systems” Springer: New York, 2004.
[6] Cogent Systems has just received a contract to provide an
Advanced Integrated Cogent Automated Palm and Fingerprint Identification System (CAPFIS) for the States of Connecticut and Rhode Island,” Cogent Systems Press Release
[7] P. Sinha, B. Balas, Y. Ostrovsky, and R. Russell, "Face
Recognition by Humans: Nineteen Results All Computer Vision Researchers Should Know About" Proceedings of the IEEE, Vol. 94, No. 11, pp 1-15, November 2006
[8] S. Ali, “Person Identification Technique Using Human Iris
Recognition”, International Journal of Computer Technology and Electronics Eng. (IJCTEE), Vol 3, Issue 6, December 2013.
[9] K. Saraswathi, B. Jarayam, and R. Balasubrama-nian, “Retinal
Biometrics based Authentication and Key Exchange System,” International Journal of Computer Applications, Vol 19, No 1, pp 1-7, 2011.
[10] Dr. Jucheng Yang “Biometrics”,June, ISBN 978- 953-307-618-8
,pp 139-154, 2011.
[11] K. B. Ray and R. Mishra, “Palmprint as a Biometric Identifier”, International Journal of Electronics and Communication Technology, Vol 2, Issue 3, ISSN : 2230-7109(Online), September 2011.
[12] College of Engineering, Pune-411005 (An Autonomous Institute
of Government of Maharashtra),
http://www.coep.org.in/index.php?pid=367
[13] http://www.mathworks.com/help/images/ref/ imrotate.html
[14] R. Khokher, R. C. Singh and R. Kumar, “Palm- print Recognition Using Geometrical and Texture Properties”, 2nd International Conference on Research in Science, Engineering and Technology (ICRSET’2014) March 21-22, Dubai (UAE), 2014.
[15] Peng Lei, “Adaptive Median Filter”, Machine Vision, Seminar
Report, ID: 03090345.
[16] https://en.wikipedia.org/wiki/Cropping_(image)
[17] Ludwig, Jamie (n. d.), "Image Convolution". Portland State
University. http://web.pdx.edu/~jduh/courses/Archive/
geog481w07/students/ludwig_image Convolution.pdf
[18] https://en.wikipedia.org/wiki/Cross-correlation