International Journal of Innovative Technology and Exploring Engineering (IJITEE) ISSN: 2278-3075, Volume-8 Issue-10, August 2019
Abstract: Crime is a piece of human exercises and should be overseen. No human culture has ever been absolutely free of degenerates and it is impossible that society will ever be. The more populated and complex, a general public turns into the more extensive the scope of solitary directs that must be constrained by the legislature through the military and different organizations particularly the Police Power. At long last, a model crime reporting system was structured that depends on four detailing shapes: a grievance or dispatch revealing structure, a crime occasion report structure, follow-up examination report structure, and a capture report structure. The framework comprises of three useful modules: an information catch module, a report the board and control module, and an information usage module. Future work on crime revealing framework can be custom-made towards availability (portable rendition), mindfulness and enhancement for the utilization.
Keywords: Crime reporting, incident-based, victims, criminals
I. INTRODUCTION
As indicated by World Bank definition, "E-government alludes to the utilization by government offices of data innovations like wide zone arrange, the web and versatile figuring that can change relations with natives, organizations and different arms of government". It adds to open security. The police individual would likewise have the capacity to distinguish any offenders and this is conceivable if a database is accessible for any residents including crooks' and blameless people's everything data. For the open wellbeing there would be record about the needed people, suspected lawbreakers' history, needed vehicles, stolen autos, cases, news and occasions, contact subtleties, proposals, etc. [1]. The destinations of this work are free access of the residents for their inquiries and grievances, building up database for natives and police faculty. The ordinary open in India are reluctant to give a grumbling in police headquarters since they are loaded up with a bogus dread about the police division. An online objection enlisting framework will understand the feelings of trepidation of open and will likewise help the police office in getting culprits. An online arrangement is valuable as the arrangement is naturally distributive [2], [3].
E – Police: Online Crime Reporting Framework is proposed to give all out electronic data framework support
Revised Manuscript Received on August 02, 2019.
Dr. S. Selvakani, Assistant Professor and Head, Department of Computer Science, Thiruvalluvar University College of Arts and Science, Arakkonam.
Mrs. K. Vasumathi, Assistant Professor, Department of Computer Applications, Thiruvalluvar University College of Arts and Science, Arakkonam.
M. Harikaran, Research Scholar, Department of Computer Science, Thiruvalluvar University College of Arts and Science, Arakkonam.
for crafted by the police. It is essential exercises are not straightforwardness related; however help furnish cops with data on criminal cases and on lawbreakers [3].
The individual who enlisted the case could likewise gain admittance to case subtleties and advancement anytime, either by setting off to any police headquarters and mentioning an officer to get to their case on E-police, or by getting to their case subtleties online by means of the application utilizing a FIR code number that is issued at the season of enrollment [3], [4]. Accessible case subtleties would incorporate the FIR, moves made, activities pending, other crime subtleties, and so on. The unfortunate casualty could hold up a grievance in the event that they see from getting to case subtleties that the case has not been enrolled appropriately, or that there has been no advancement put forth on the defense since it was last gotten to. At last, senior officers in the police administration could likewise utilize E-police to screen case subtleties and advancement. The majority of this influences the straightforwardness of case dealing with, and the responsibility of cops [4], [5].
II. SURVEY OF TECHNOLOGY
Literature survey is the most important step in software development process. Before developing the tool it is necessary to determine the time factor, economy and company strength. Once these things are satisfied, then the next step is to determine which operating system and language can be used for developing the tool. Once the programmers start building the tool the programmers need lot of external support. This support can be obtained from senior programmers, from book or from websites. Before building the system the above consideration are taken into account for developing the proposed system.
The major part of the project development sector considers and fully survey all the required needs for developing the project. For every project Literature survey is the most important sector in software development process [6], [7].
Before developing the tools and the associated designing it is necessary to determine and survey the time factor, resource requirement, man power, economy, and company strength. Once these things are satisfied and fully surveyed, then the next step is to determine about the software specifications in the respective system such as what type of operating system the project would require, and what are all the necessary software are needed to proceed with the next step such as developing the tools, and the associated operations [6], [7] .
Web Based Online Crime Reporting System
using Asp.Net
III. METHODOLOGY A. Existing System
Residents (Citizens) can't get the data and the present status of the culprits of all urban areas Crime information mining is the use of information digging strategies for Crime investigation. Different explores have been completed in this area. Crimes can be isolated into subcategories dependent on various criteria. In eight crime classes are given. They are criminal traffic offenses, sex violations, burglary, misrepresentation, and fire related crime, medicate offenses and vicious crimes [8].
There were numerous endeavors to investigate distinctive sorts of violations utilizing mechanized strategies yet there is no bound together structure portraying how to apply those procedures to various crime types. In, they have utilized a structure which incorporates a connection between the crime information mining procedure and crime type attributes. There are a few existing frameworks which use crime information digging systems for crime examination, for example, territorial crime investigation program, information digging structure for crime design distinguishing proof and opiates organize in Indian police division [9].
A crime distinguishing proof framework is depicted in which can be utilized to foresee conceivable suspects for given crime. They have utilized five kinds of operators to be specific, message space specialist, door operator, detainee operator, criminal specialist and proof specialist [9], [10].
B. Proposed System
In this paper talked about that present manual arrangement of the police headquarters is extensive and tedious. After a gritty investigation of the present framework, it is a decent time to propose another framework which dependent on the PC. The proposed framework is planned to evacuate every one of the downsides and impediments of existing framework and make progressively mindful to the client and the administration needs.
The real targets of the proposed framework are to give the quicker methods for Crime Grievance Report. It will diminish the time devoured motel planning of reports and get the opportunity to profit by the most recent innovation of PCs.
The proposed framework incorporates following highlights:
• Citizens not have to go police headquarters to see the criminal's information.
• They can legitimately observe data on location.
• Visitor can without much of a stretch get the data about the crime.
• Reduce the labor. • Reduce the time.
• Member can see the present status of the crime reporting.
IV. SYSTEM DESIGN AND IMPLEMENTATION Implementation is the most significant stage in accomplishing a fruitful framework and giving the client's certainty that the new framework is serviceable and viable. Execution of an altered application is to supplant a current one. This sort of discussion is generally simple to deal with, give there are no real changes in the framework.
Each program is tried exclusively at the season of
this program connected together in the route determined in the projects detail, the PC framework and its condition is tried as per the general inclination of the client. The framework that has been created is acknowledged and ended up being agreeable for the client. Thus the framework will be actualized very quickly.
A straightforward working methodology is incorporated so the client can comprehend the distinctive capacities obviously and rapidly. At first as an initial step the executable type of the application is to be made and stacked in the regular server machine which is available to the whole client and the server is to be associated with a system.
Figure 1 System Architecture
Basic Modules
1. Police Station Registration Module 2. Victim FIR Registration Module 3. Investigating Evidence Register Module 4. Department Module
5. Report Module
1. Police Station Registration Module
This module keeps up the data pretty much all the police headquarters that are enrolled according to the purview of the framework. It additionally gets coordinated with the representatives who are working in these stations alongside their assignment.
2. Victim FIR Registration Module
This module keeps up the data identified with the primary examination report of the crime groupings that have occurred. The FIR enrolls all that information that is essential for the examination to occur in appropriate length. It recognizes the crime classification and the crime nature.
3. Investigating Evidence Register Module
This module makes an accumulation of data identified with every one of the confirmations that become completely vital under the ordinary succession of the examination, this module progressively thinks upon the progressions that occur while the arrangement of examination is under procedure.
4. Department Module Law and Order
Traffic and control
Cyber Crime
Women Protection
International Journal of Innovative Technology and Exploring Engineering (IJITEE) ISSN: 2278-3075, Volume-8 Issue-10, August 2019
5. Report Module
Complaints recorded in multi day and move made to it. It ought to likewise report unattended grumblings.
Crime rate because of different kinds of violations in a month/year and furthermore in locale/state insightful.
Report with respect to most needed hoodlums and abundance data if accessible.
Police officers frequently send out the FIR (copy) duplicate to report group.
V. RESULT AND DISCUSSION A. Testing Reports
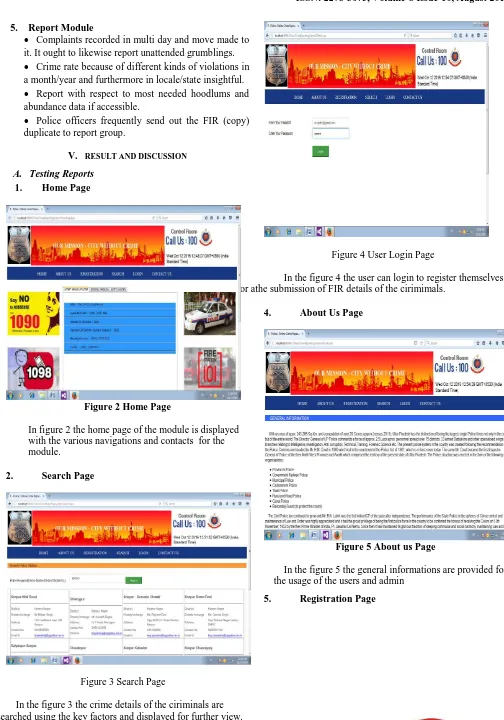
[image:3.595.41.545.29.749.2]1. Home Page
Figure 2 Home Page
In figure 2 the home page of the module is displayed with the various navigations and contacts for the module.
2. Search Page
Figure 3 Search Page
In the figure 3 the crime details of the ciriminals are searched using the key factors and displayed for further view.
3. User Login Page
Figure 4 User Login Page
In the figure 4 the user can login to register themselves for athe submission of FIR details of the cirimimals.
4. About Us Page
Figure 5 About us Page
In the figure 5 the general informations are provided for the usage of the users and admin
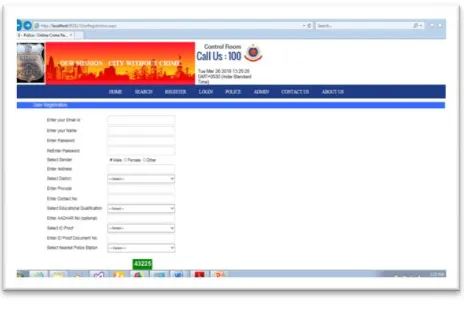
[image:3.595.48.279.192.436.2]Figure 6 Registration Page
In figure 6 the user registration page is shown with filling up details for registering the email id for the complaints placed by the user.
6. Admin Page
Figure 7 Admin Page
In figure 7 the admin can login with the username and password to view the complaints placed by the user from the location.
[image:4.595.46.284.553.722.2]7. Contact Us Page
Figure 8 Contact us Page
In figure 8 the contact details of the police and its brief details have been displayed for the purpose of the user
B. Implementation
A vital stage in the framework life cycle is the fruitful execution of the new framework plan. Usage just methods changing over another framework structure into activity. This includes making PC compatible records, preparing the working errand, and introducing equipment, terminals before the framework is done and running.
An essential stage in the framework life cycle is the effective usage of the new framework plan. Execution just methods changing over another framework plan into operation.This includes making PC good documents, preparing the activity staff, and introducing equipment , terminals before the framework is done and running.
Installation of Software:
Above all else, I arranged (Distribute) Pre Compiled Web documents with the assistance of Manufacture Menu. At that point these documents are replicated into httpdocs/www.root envelope in IIS Web Server Reassure with the assistance of FileZilla Programming. On this Server I additionally duplicate Database of all the procedures that are required to retrieves the information from database. Then begin the IIS Server and access the site.
Training the Operating Staff:
Every one of the clients are given exhibition in the wake of replicating all the files. In this show all the info factors are taken and venture is executed. After this I give them opportunity to run venture independent from anyone else.
Installation of Hardware:
Undertaking all the equipment necessities are not satisfied but rather exist their systems administration between the customer’s machines already. So the main need is to introduce appropriate equipment for the product.
VI. CONCLUSION
In conclusion, in this take a look at, looked at the diverse definitions of criminal facts. Sooner or later, a prototype crime reporting device turned into designed that is predicated on four reporting forms: a criticism or dispatch reporting form, a criminal offense event record form, observe-up investigation document form, and an arrest document shape. The device includes five practical modules: a police station registration module, victim FIR register module, investigating evidence register module, department module and report module. The machine keeps an occasion or case report and a police activity record. The conceptual crime reporting device layout and facts elements for that reason evolved ought to now be examined and evaluated in an operational environment.
FUTURE SCOPE OF THE PROJECT
International Journal of Innovative Technology and Exploring Engineering (IJITEE) ISSN: 2278-3075, Volume-8 Issue-10, August 2019
Photo
A comfort for the server farm might be made accessible to enable the work force to screen on the locales which were cleared for facilitating amid a specific period.
REFERENCES
1. World Bank’s Website, Definition of E-Government;
http://www.web.worldbank.org › ... › Information & Communication E-Government
2. Harlow (1985), Reporting Crimes to the Police: Bureau of Justice Statistics Special Report NCJ-99432, US Government Printing Office, Washington DC.
3. Boba, R. (2005). Crime Analysis and Crime Mapping
4. Skogan (1984), “Reporting crimes to the police: The status of world research”, Journal of Research in Crime and Delinquency, vol. 21, pp. 113-37.
5. Robert D. Crutchfield, George S. Bridges, and Susan R. Pitchford, “Analytical and Aggregation Biases in Analyses of Imprisonment: Reconciling Discrepancies in Studies of Racial Disparity,”
6. Toshinobu Yasuhira, “Fundamental Upgrade of the Internal Network System within the National Police Agency of Japan”, 43rd Annual 2009 International Carnahan Conference on Security Technology, 2009.pp.100-106
7. Lyon (2005), “Global Positioning System” Location Tracker 8. The Nigeria Dailies, (2009), “The Historical Background of Nigerian
Police”
9. Allen (2002), “Meaning of Crimes”, Crime Management
10. Black (1984), “Crime as social control”, in Toward a General Theory of Social Control, vol. 2, Selected Problems, ed.
AUTHORSPROFILE
Dr. S. Selvakani is currently serving as the Head of the Department of Computer Science and Applications, Thiruvalluvar University College of Arts and Science.
She completed her Ph.D. in Computer Science in the year 2009 in Mother Teresa University. A holder of both M.Tech and MCA, M. Phil gives her the acumen to engage in research in mobile computing. As a proficient student, she has graduated her MCA with University Rank 3 from Manonmaniam Sundaranar University and M.Phil. with Distinction from Madurai Kamarajar University. She began her career as lecturer in Bharathiyar University in 2002 and since then has worked in colleges in Chennai and Tirunelveli. Her single longest work experience is with Francis Xavier Engineering College, Tirunelveli as the Head of the Department for over 7 years.
Dr. S. Selvakani has been an active researcher throughout her career. She has published 70 papers in international journals / conferences including Elseiver, Inderscience etc. Her research experience has earned her accolades as reviewer for International Journals like SPRINGER – WINE. As a well-known academic, she has chaired many sessions and has been the guest speaker in both National and International conferences. She is a member of Board of Studies for various reputed Autonomous Colleges and a Question paper setter for Bharathiyar University, Madras University and various Deemed Universities.
Mrs. K. Vasumathi, Serving as an Assistant Professor in the Department of Computer Applications. Thiruvalluvar University College of Arts and Science. She Completed B.Sc., M.Sc., (IT), M.Phil. and [SET] in the field of Computer Science. She is an eminent Scholar. A Strong hard worker with 9 years of Teaching Experience.