International Journal of Innovative Technology and Exploring Engineering (IJITEE) ISSN: 2278-3075, Volume-8 Issue-7, May, 2019
Abstract. Internet of Things IoT) is important platforms to provide efficient data retrieval from outsource wireless data storage system in day-to-day activities. Major challenge in these type of wireless storage data sources to extract useful data from heterogeneous data by constrained IoT in real time vehicular ad hoc networks. Privacy is also complex task for retrievable data from wireless storage system. So that in this paper, we propose Hash based cipher-text attribute based encryption paradigm (HCPABEP) to explore secure based data retrieval from vehicular ad hoc networks. Road side unit (RSU) is the component to perform efficient encryption and decryption efficiency of vehicle information at storage in server side. Our proposed approach mainly adapted and estimated position of vehicles with encrypted and decrypted overhead in storage system. Our experimental results show that proposed approach gives better data forwarding with privacy preserving in vehicular ad hoc networks.
Index Words: Wireless sensor networks, Internet of Things, Road side Unit, attribute based encryption.
I.INTRODUCTION
At present, with the quick improvement of the city, individuals are increasingly more necessity on transportation, confronting the standardization issue, for example, city traffic clog, traffic wellbeing, traffic association, etc, the customary mindset has been unfit to take care of these issues .With the improvement of innovation science related technologies like geo-graphic data, sensor related data computer vision related concepts; Internet-of-Vehicles (IoV) has drawn extraordinary research and industry consideration.
The blend of data from sensors installed distinctive vehicles and on the framework through correspondence frameworks will at long last yield traffic sensor systems opening up an absolutely new range of functionalities with phenomenal benefits[2]. Above all else, helpful detecting and agreeable move arranging will impressively improve traffic wellbeing. Besides, such innovation empowers facilitated traffic directions, which stays away from sharp increasing speed/deceleration and lingering. In light of this data, speed can be blended with both the traffic light cycles and the traffic circumstance, in this manner yielding improved traffic
Revised Manuscript Received on May 07, 2019.
S Vivek Reddy, Department of CSE, Koneru Lakshmaiah Education Foundation, Vaddeswaram, A.P, India.
Dr V Krishna Reddy, Department of CSE, Koneru Lakshmaiah Education
stream just as fuel and CO2 funds of up to 14%. Up to 25% of fuel and by far most of traffic space can be spared through tight caravan driving of vehicles on thruways.
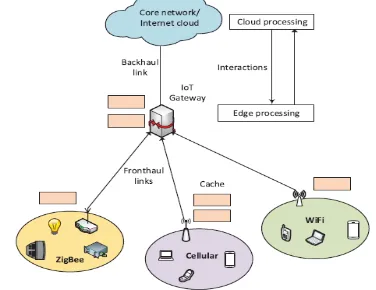
[image:1.595.362.522.513.650.2]Processing of outsourced cloud data to edge of the cloud systems, it employs the type of user services, for example, area mindfulness, nature of administrations (QoS) upgrade, and low inactivity. Haze processing can furnish these administrations with versatile assets easily. It likewise empowers the smooth assembly between distributed environment and IoT gadgets for substance conveyance. In data processing from heterogeneous data sources security issue is the major challenging task to register and transfer data from clients to cloud storage system.When all is said in done, the signi cannot dangers in mist figuring systems are: Information Alteration: A foe can bargain information uprightness by endeavoring to adjust or obliterate the authentic information. Subsequently, it is basic to de ne a security system to give information respectability confirmation of transmitted data between different users in cloud. Listening in Attacks: busybodies can increase unapproved block attempt to get familiar with a great deal about the client data transmitted through remote correspondences. The danger of such assaults is that they can't be effectively recognized in light of the fact that spying does not transform anything in the system tasks. Basic procedure
Figure 1. Data outsourcing from different storage devices in cloud
The essential security prerequisites for the correspondences between the mist hubs and the cloud are: secrecy, get to control, confirmation, and unquestionable status to store and access data from cloud shown in figure 1.We propose a novel encrypted key exchange protocol based on CP-ABE for secure
communications in a fog computing network, which
Adaptive Cloud Framework to Explore
Outsourced data in Wireless IoT Computing
Systems
includes the accompanying accomplishments:
We build up a convention for scrambled key trade dependent on CP-ABE that consolidates encryption and mark to accomplish a ne-grained information get to control, conveniality, validation, and verifiability.
We talk about the security of our convention and demonstrate its rightness. Specifically, we research the security of our convention under various assault situations.
We dissect the execution of our proposed convention and delineate its efficiency as far as message estimate and correspondence overhead.
We execute and contrast our convention and a certificate-based convention and demonstrate its practicality.
II. BACKGROUND WORK
There is a limitless scope of potential applications for mist and edge registering, extending from basic IoT based sensor observing to the perplexing information handling frameworks characteristic in Industry 4.0, e-wellbeing, keen urban areas and so on. Therefore, hidden applications differ in their requirements dependent on the level of (I) logical area mindfulness and low inertness, (ii) geographic dispersion, (iii) scale and coordination of end-point systems, (iv) heterogeneity, between operability and usefulness of end focuses, (v) ongoing versus clump preparing, (vi) portability of end focuses, and (vii) interaction between the edge, the haze and the cloud layers [4,22]. Provisioning for such heterogeneity requires critical arranging forthright and continuous advancement all through the C2T continuum including application plan. Most of current haze and edge benefits that help applications can be additionally isolated into three principle classifications - Content Distribution Networks (CDN), IoT and Virtual Network Functions (VNF). While every one of the three utilize a similar foundation, the useful parts of each sort of administration are in a general sense unique. CDN administrations center generally around static substance replication and circulation over various areas. IoT administrations are utilized to offload information preparing and capacity from sensors to edge areas specifically pushing a portion of the information up the system stack to the cloud. VNFs are chains of system works that handle portable system convention traffic (e.g., LTE stack) or give organize traffic separating and directing capacities, for example, undertaking, firewall and VPN administrations. Law [23] proposes "a reproduction model ought to dependably be created for a specific arrangement of targets. Truth be told, a model that is legitimate for one goal may not be for another." Modeling the majority of the applications sent inside a mist/edge system can be helpful for foundation suppliers however developing a recreation arrangement that can proficiently deal with a lot of such expansive goals is a test and needs cautious thought.
Recent studies attract on the emergence of 5G networks and the interaction during these networks and gloom and achieve computing. 5G networks cope join improvements over optimizationof aerial resource style, rich disclosure pre-processing, and context-aware services (using cell jade,user lot, and allocated baud rate as information) [20]. Notwithstanding these improvements,as each smoke and upset application take care of have different fixer
requirements and make out generate differenttypes of word and join traffic, a mechanism manage be forced upon to detect delay-sensitive flowssuch as network slicing [26].
Modelling addict mobility aspects requires the implementation of geographic depth of perception logic,for concrete illustration calculation of the nearest soaring attain
answer based on freak coordinates at each
simulationtimestep. Furthermore, availability and access to real-world announcement on bring to a close user mobility is problematicboth legally and technically. Additional calculations besides increase the entanglement and computationalresource demands of a if and only if pose platform. Intelligent exemplar generators are one everything but kitchen sink forcreating gloom and upset infrastructure
workload models based on 3rd lots of laugh
socio-demographic andgeographic data that gave a pink slip be hand me down for simulation purposes.
III. EDGE-CLOUD DATA PROCESSING PROCEDURE
[image:2.595.338.526.359.504.2]Edge registering and cloud registering arrangements have their very own particular focal points and drawbacks from the viewpoint of live information examination in remote IoT systems.
Figure 2.Heterogeneous IoT networks edge cloud data processing
International Journal of Innovative Technology and Exploring Engineering (IJITEE) ISSN: 2278-3075, Volume-8 Issue-7, May, 2019
Other than the constant preparing of enormous IoT information, this synergistic system an empower newwireless IoT applications which may require joint efforts among diverse edge figuring units, and between edge processing units and the cloud focus.
The framework will benefit from the upsides of both the distributed computing and edge registering. Not with standing this, we imagine cloud focus as an observing and direction stage to have compelling ongoing information handling at the edge-side of remote IoT systems. In down to earth situations, IoT gadgets/sensors are heterogeneous in nature as far as their registering capacities, insight just as the figuring/ handling power. In such manner, it turns out to be profoundly beneficial to direct the task/handling of edge-hubs in request to use the accessible correspondence and processing assets in a successful way. In the thought about system, edge processing accumulates data from the encompassing radio condition while the distributed computing helps by giving appropriate guidelines to the edge-side hubs for their activities. For instance, the tasks at the edge-side, for example, information pressure, filtering, examining rate, control, and settling on choices on the sort of information to be detected/procured can be bolstered by the cloud focus by giving appropriate control motions over the criticism joins.
Since the cloud focus can have a worldwide perspective on data gathered from a substantial number of sensors sent over a substantial topographical locale, the control of edge handling from the cloud-side can give significant upgrades in future remote IoT systems. Because of immense measure of registering assets accessible at the cloud end, it is beneficial to off-load a great part of the computational undertakings to the cloud. On the other hand, it is beneficial to deal with deferral delicate errands at the edge-side. Contingent upon different dimensions of data for example, traffic types, area data, preparing delay what's more, transmission overhead, the choice on whether to off load information to the cloud or not can be made. It can likewise be considered that all the edge hubs are worked in an organized manner in request to help each other as far as correspondence, figuring furthermore, capacity/storing assets. Another imperative perspective which can be abused in the proposed system is that cloud preparing can use the history/deferred data accessible at the cloud-focus so as to surmise certain choices for the edge preparing without the need of hanging tight for the quick information gathered from IoT hubs.
IV. PROBLEM DESCRIPTION
[image:3.595.331.539.54.167.2]In this section, describe the problem formation in vehicular ad hoc networks, basic representation of VANETs shown in figure 3, this framework mainly consists 3 components a) trusted center (TC), Roadside unit (RSU) along with road simulation structure and on-board units (OBUs) simulated with running vehicles. Whenever vehicles communicate with each with other one then nearest RSU extract data from short range communication based on wireless sensor communication with specific bandwidth in communication range of vehicles.
Figure 3. Problem description for different vehicle passing between RSU’s
The trusted center combined with multiple modules like user authentication with trusted or un-trusted authentication of each vehicle, encryption of each vehicle, message description etc. Authenticated trust module consists registration vehicle information by roadside unit (RSU), on-board units (OBUs), manage attributes of system and exploring distributing different security keys for vehicles stored in storage system. TC verifies each vehicle message and then estimate the transmitted range either vehicle damaged in affected simulated roads. Then TC encrypt vehicle information with respect to correspond vehicle attributes..
Basic problem formation in vehicular ad hoc network information is as follows:
1) Privacy preserving is the major aspect in vehicular ad hoc networks, vehicles store without authentication with respect to access control policies in vehicular ad hoc networks.
2)Privacy enforcement, messages should be constrained with access control and deliver data to selected or specified vehicles without hiding information of vehicles.
Based on multimedia scenario of data transmission message encryption and decryption computed at each vehicles. In addition that a new cryptographic model introduce for significant communication in VANETs.
V.SYSTEM MODEL IMPLEMENTATION
In this section, we present procedure and implementation of proposed approach based versatile mixed media information sending plan for protection safeguarding in vehicular specially appointed systems.
Attestation Procedure of Vehicles
Setup(λ, U) Environment: In setup environment, describe the security parameters λ and storage in quality set U, in this master key generates for each vehicle based on group information of each vehicles with different representations. At that point, it picks a substantial number of gathering components h1,..., hU∈ G related with each characteristic of the trait set U. In addition, the framework picks two examples in
Zp haphazardly, i.e., α1 ∈Zp, α2 ∈Zp, and let α = (α1 + α2) mod p. At long last, the open key PK is meant as The ace mystery key is spoken to as
MK = α1, α2, α. At the point
when vehicles move
need to enroll at an adjacent RSU.combined with on-board unit.
Algorithm 1. Registration of different vehicles with respect to different vehicular attributes.
As shown in alg 1, receive vehicle request from one to other vehicles via RSU and performs attestation of on board unit in vehicle. Targeted RSU identifies authentication of each vehicle in on-board unit. RSU explores registered vehicles and describe type of vehicle with dynamic data of vehicle. Based on dynamic attribute based on type of vehicle name, location and dimensionality based on longitude and latitude and also analyze the characterization of data in vehicular ad hoc networks.
Vehicle Message Authentication
[image:4.595.310.550.354.486.2]When a message reported as a particular event message i.e. trusted center define launches emergency in vehicle communication. First it identifies status emergency representation in vehicle information. If rescue situation appeared then based on its location it s stores vehicle information with their selective messages with access control on disseminated communication of each vehicle. Fig. 4 demonstrates a cryptography-restricting access approach for message scattering.
Figure 4. Access control policies with respect to different vehicle attributes
The calculation initially determines a vector v = (s, y2,..., yn)T ∈Zn p. Every segment s ∈Zp is haphazardly picked as the key to be shared. Different qualities are embraced to share the encryption type s. For I = 1 to l, it ascertains λi = Mi v,where Mi ith column of M with respect to vector representation.
Additionally, select few irregular examples r1,...,rl∈Zp in the cryptography computation over encrypt. The CT is ciphertext produced as: C = me(g, g)αs,C = gs, (C1 = gaλ1 h−r1 ρ(1), D1 = gr1 ), . . . ,Cl = gaλlh−rl ρ(l), Dl = grl) Because of the seriousness of crisis, the confided in focus assesses and illustrate over required time, and then it chooses the distance to communicate the message. Check each message whether it check authentication at storage side.
VI. EXPERIMENTAL EVALUATION
Having the bits of knowledge into the different components influencing the execution of our versatile information sending plan in VANET concerning Internet of Things, we lead tests utilizing genuine maps extricated from the Hangzhou database in this segment. We play out a lot of analyses utilizing a littler area of the guide, and lead a few investigations to check the productivity of our proposed plan.
Figure 5. Road segment with respect to different vehicular attributes.
[image:4.595.85.260.585.736.2]As appeared in Fig. 3, it shows design of the road simulation way point with different junctions for different vehicles communication each then, we calculate location time for vehicle communication in wireless ad hoc networks. Different simulation parameters shown in table 1.
Table 1. Vehicular simulation parameters.
Procedure for Attestation of different vehicles 1: Vehicles move around RSU
2: Vehicle (L Nv )P KRSU → RSU 3: RSU gets L Nv by SKRSU 4: if L Nv ∈ DMV then
5: dead set on attributes: {type, blew up out of proportion, year,...}L Nv
6. attribute description in bold:{road,loc, dir,...}L Nv
7: complete if
8: attributes are transferred by RSU to middle of the road along by all of the
L Nv
9: KeyGen configures Trust center
(MK,S)→AK, SK
10: Then middle of the road AK → RSU, SK → vehicle nodes
11: do for
Simulation Parameter
Value description
Speed of
vehicle
60m/h
Range of
communicatio n
500 m
RSU Coverage Starting from 10
[image:4.595.331.510.597.719.2]International Journal of Innovative Technology and Exploring Engineering (IJITEE) ISSN: 2278-3075, Volume-8 Issue-7, May, 2019
Every vehicle pursues the briefest way to its goal. We receive the down to earth information from the genuine street section. The number of street paths is considered in steady with the genuine streets. The quantity of vehicles and their thickness in the reproduction are gathered by blades which are conveyed on the genuine street fragments. We use JAVA with NETBEANS and different data sets relates to vehicles traffic data.
[image:5.595.76.267.268.447.2]Our answer for the decoding calculation at each vehicle is very productive than traditional approaches unscrambling conspire. In the way, the vehicle can calm the calculation remaining task at hand by assigning a large portion of the calculation to the RSU. This arrangement, in any case, is to the detriment of extra RSU decoding calculation overhead.Fig. 6 shows the estimated decoding times of each vehicle at on-board unit, assigning, as an element of approach property N.
Figure 6. Storage of data with respect to different attributes of vehicles.
We rehash the trial on various occasions for each ciphertext arrangement. At that point, we accept the normal qualities as appeared in Fig. 5.
Figure 7. Number of attribute relations with different vehicles.
Fig. 7 shows the normal changed unscrambling time with numerous vehicles as various quantities of different vehicles at same site. As appeared in the Fig. 7,
proposed approach gives better results with respect to time values for different policy attributes.
VII.CONCLUSION
This paper displays a versatile mixed media information sending plot for protection safeguarding in vehicular specially appointed systems. In our approach RSU choose the dynamic location of each vehicle in front of store data into storage system. Decision tree is required for authentication of each vehicle whether it is related to store in two specific formats i.e. hash based format and normal data format. Performance of proposed gives better and efficient results with comparison of privacy relates aspects in real time wireless communication at vehicle ad hoc networks. Complete reproduction results show that our versatile information sending plan can give an effective and secure answer for transmitting interactive media messages.
REFERENCES
1. SHREE KRISHNA SHARMA,” Live Data Analytics With Collaborative Edge andCloud Processing in Wireless IoT Networks”, Received January 31, 2017, accepted February 27, 2017, date of publication March 20, 2017, date of current version April 24, 2017..
2. S. K. Sharma, T. E. Bogale, S. Chatzinotas, X. Wang, and L. B. Le, ``Physical layer aspects of wireless IoT,'' in Proc. Int. Symp. Wireless Commun. Syst. (ISWCS), Sep. 2016, pp. 304_308.
3. P. Fan, ``Coping with the big data: Convergence of communications, computing and storage,'' China Commun., vol. 13, no. 9, pp. 203_207, Sep. 2016.
4. H. Liu, Z. Chen, and L. Qian, ``The three primary colors of mobile systems,'' IEEE Commun. Mag., vol. 54, no. 9, pp. 15_21, Sep. 2016. 5. S. Andreev et al., ``Exploring synergy between communications, caching,
and computing in 5G-grade deployments,'' IEEE Commun. Mag., vol. 54, no. 8, pp. 60_69, Aug. 2016.
6. J. Tang and T. Q. S. Quek, ``The role of cloud computing in contentcentric mobile networking,'' IEEE Commun. Mag., vol. 54, no. 8, pp. 52_59, Aug. 2016.
7. P. Corcoran and S. K. Datta, ``Mobile-edge computing and the Internet of Things for consumers: Extending cloud computing and services to the edge of the network,'' IEEE Consum. Electron. Mag., vol. 5, no. 4, pp. 73_74, Oct. 2016.
8. X. Masip-Bruin, E. Marn-Tordera, G. Tashakor, A. Jukan, and G. J. Ren, ``Foggy clouds and cloudy fogs: A real need for coordinated management of fog-to-cloud computing systems,'' IEEE Wireless Commun., vol. 23, no. 5, pp. 120_128, Oct. 2016.
9. C. Vallati, A. Virdis, E. Mingozzi, and G. Stea, ``Mobile-edge computing come home connecting things in future smart homes using LTE deviceto- device communications,'' IEEE Consum. Electron. Mag., vol. 5, no. 4, pp. 77_83, Oct. 2016.
10. M. Satyanarayanan, ``The emergence of edge computing,'' Computer, vol. 50, no. 1, pp. 30_39, Jan. 2017.
11. S. H. Park, O. Simeone, and S. Shamai (Shitz), ``Joint optimization of cloud and edge processing for fog radio access networks,'' IEEE Trans. Wireless Commun., vol. 15, no. 11, pp. 7621_7632, Nov. 2016. 12. M. Chiang and T. Zhang, ``Fog and IoT: An overview of research
opportunities,'' IEEE Internet Things J., vol. 3, no. 6, pp. 854_864, Dec. 2016.
13. S. Yin and O. Kaynak, ``Big data for modern industry: Challenges and trends [point of view],'' Proc. IEEE, vol. 103, no. 2, pp. 143_146, Feb. 2015.
14. H. Hu, Y. Wen, T.-S. Chua, and X. Li, ``Toward scalable systems for big data analytics: A technology tutorial,'' IEEE Access, vol. 2, pp. 652_687, Jul. 2014.
[image:5.595.63.281.507.715.2]16. Y. He, F. R. Yu, N. Zhao, H. Yin, H. Yao, and R. C. Qiu, ``Big data analytics in mobile cellular networks,'' IEEE Access, vol. 4, pp. 1985_1996, 2016.
17. H. Cai, B. Xu, L. Jiang, and A. V. Vasilakos, ``IoT-based big data storage systems in cloud computing: Perspectives and challenges,'' IEEE Internet Things J., vol. 4, no. 1, pp. 75_87, Feb. 2017.
18. D. Puthal, S. Nepal, R. Ranjan, and J. Chen, ``Threats to networking cloud and edge datacenters inthe Internet of Things,'' IEEE Cloud Comput., vol. 3, no. 3, pp. 64_71, May 2016.
19. J. A. Stankovic, ``Research directions for the Internet of Things,'' IEEE Internet Things J., vol. 1, no. 1, pp. 3_9, Feb. 2014.
20. V. Cevher, S. Becker, and M. Schmidt, ``Convex optimization for big data: Scalable, randomized, and parallel algorithms for big dataanalytics,'' IEEE Trans. Signal Process., vol. 31, no. 5, pp. 32_43, Sep. 2014. 21. J. Sun, C. Zhang, Y. Zhang, and Y. Fang, “An identity-based security
system for user privacy in vehicular ad hoc networks,” IEEE Trans. Parallel Distrib. Syst., vol. 21, no. 9, pp. 1227–1239, Sep. 2010. 22. Y. Xia, X. Liu, F. Xia, and G. Wang, “A reduction of security notions in
designated confirmer signatures,” Theor. Comput. Sci., vol. 618, pp. 1–20, Mar. 2016.
23. R. Lu, X. Lin, H. Zhu, P.-H. Ho, and X. Shen, “ECPP: Efficient conditional privacy preservation protocol for secure vehicular communications,” in Proc. IEEE 27th Conf. Comput. Commun. (INFOCOM), Apr. 2008, pp. 1229–1237.
24. T. R. de Oliveira, S. de Oliveira, D. F. Macedo, and J. M. Nogueira, “Social networks for certification in vehicular disruption tolerant networks,” in Proc. IEEE 10th Int. Conf. Wireless Mobile Comput. Netw. Commun. (WiMob), Oct. 2014, pp. 479–486.
25. R. Lu, X. Lin, and X. Shen, “SPRING: A social-based privacypreserving packet forwarding protocol for vehicular delay tolerant networks,” in Proc. IEEE INFOCOM, Mar. 2010, pp. 1–9.
26. P. Zhong and R. Lu, “PAD: Privacy-preserving data dissemination in mobile social networks,” in Proc. IEEE Int. Conf. Commun. Syst. (ICCS), Nov. 2014, pp. 243–247
27. L.-Y. Yeh, Y.-C. Chen, and J.-L. Huang, “ABACS: An attribute-based access control system for emergency services over vehicular ad hoc networks,” IEEE J. Sel. Areas Commun., vol. 29, no. 3, pp. 630–643, Mar. 2011.
28. X. Hong, D. Huang, M. Gerla, and Z. Cao, “SAT: Situation-aware trust architecture for vehicular networks,” in Proc. 3rd Int. Workshop Mobility Evol. Internet Archit., Aug. 2008, pp. 31–36.
29. S. Ruj, A. Nayak, and I. Stojmenovic, “Improved access control mechanism in vehicular ad hoc networks,” in Ad-Hoc, Mobile, and Wireless Networks. Berlin, Germany: Springer, 2011, pp. 191–205.
AUTHORS PROFILE
Dr. V Krishna Reddy is presently working as Professor in Computer Science Engineering Department, Koneru Lakshmaiah Education Foundation, Vaddeswaram, A.P, India.