102
HOP BY HOP AUTHENTICATION FOR SOURCE
INTERMEDIATE NODE PRIVACY PROTECTION IN
NETWORK
NAJEEM DHEEN A PG Scholar, Department of CSE, Hindusthan Institute of Technology, Coimbatore, India
Email ID: andheen@gmail.com DR.S UMA
HOD/ PG-CSE, Department of CSE, Hindusthan Institute of Technology, Coimbatore, India Email ID: umakarunahind@gmail.com
THIYAGARAJAN A PG Scholar, Department of CSE, Hindusthan Institute of Technology, Coimbatore, India,
Email ID: akthiyagu@gmail.com SUBIN P S
PG Scholar, Department of CSE, Hindusthan Institute of Technology, Email ID: subin616@gmail.com
ABSTRACT- A Message Authentication Code is a short piece of Coimbatore, India. Email information
used to authenticate a message and to provide integrity and authenticity assurances on the message. Integrity assurances detect accidental and intentional message changes, while authenticity assurances affirm the message's origin. For this reason, many message authentication schemes have been established, based on either symmetric-key cryptosystems or public-key cryptosystems. Most of them, however, have the limitations of high computational and communication overhead in addition to lack of scalability and resilience to node compromise attacks. To address these issues, a polynomial-based scheme was recently introduced. However, this scheme and its extensions all have the weakness of a built-in threshold determined by the degree of the polynomial: when the number of messages transmitted is larger than this threshold, the adversary can fully recover the polynomial. A scalable authentication scheme based on elliptic curve cryptography (ECC) is proposed in this work. While enabling intermediate nodes authentication, the proposed scheme allows any node to transmit an unlimited number of messages without suffering the threshold problem. In addition, this scheme can also provide message source privacy.
Keywords: MAC, elliptic curve cryptography, polynomial, crypto systems
WIRELESS SENSOR NETWORKS
1. LITERATURE SURVEY
Message authentication plays a key role in thwarting unauthorized and corrupted messages from being forwarded in networks to save precious sensor energy. Keys are secure against coalitions of up to k users; that is, even if k users pool together their pieces they cannot compute anything about a
103
technique to simultaneously accomplish the goals of lightweight, resilience to a large number of node compromises, immediate authentication, scalability, and non-repudiation.
Multicast stream authentication and signing is an important and challenging problem. Applications include the continuous authentication of radio and TV Internet broadcasts, and authenticated data distribution by satellite [4]. The main challenges are fourfold. First, authenticity must be guaranteed even when only the sender of the data is trusted. Second, the scheme needs to scale to potentially millions of receivers. Third, streamed media distribution can have high packet loss. Finally the system needs to be efficient to support fast packet rates. [6] Propose two efficient schemes, TESLA and EMSS, for secure lossy multicast streams. TESLA (Timed Efficient Stream Loss-tolerant Authentication),offers sender authentication, strong loss robustness, high scalability and minimal overhead at the cost of loose initial time synchronization and slightly delayed authentication.
2. EXISTING SYSTEM
Traditional deniability only considers the privacy of thehonest proved against a possibly malicious verifier, andrequires that the interactions between them be computationallysimulatable, i.e., computational zero-knowledge (ZK). What we wouldlike to happen is that if the prove acts honestly during theprotocol, it also should not be able at a later stage to claimthe messages are authentic in order to violate the privacy of the verifier. This
property is calledforward
deniability,asithassome affinity to the notion of forward secrecy. It is shownthat computational ZK does not guarantee forward deniability, but statistical ZK does. The security of DIKE is analyzed in accordance withthe Canetti-Krawczyk framework (CK-framework) withpost-specified peer sin the random oracle (RO) model. Wealso make discussions on a list of concrete yet essentialsecurity properties of DIKE, most of which are beyond theCK-framework. We then define CNMSZK for DHKE, alongwith detailed clarifications and justifications. To our knowledge, our formulations of CNMSZK for DHKE stand for thestrongest definition of deniability, to date, for key-exchangeprotocols. The CNMSZK property of our protocols is analyzedin the restricted random oracle model, under an extension of the knowledge-of-exponent assumption namedconcurrent knowledge-of-exponent (CKEA) that might be ofindependent interest.
104
this method does not work in multicast networks.
3. PROPOSED SYSTEM
In this proposed system, a secure and efficient source anonymous message authentication method is proposed with effective algorithm Elliptic Curve Cryptography (ECC). This scheme is secure against adaptive chosen-message attacks. This scheme enables the intermediate nodes to authenticate the message so that all corrupted message can be detected and dropped to conserve the sensor power. While achieving compromise resiliency, flexible-time authentication and source identity protection, our scheme does not have the threshold problem. It develop a source anonymous message authentication code on elliptic curves that can provide unconditional source anonymity. It offer an efficient hop-by-hop message authentication mechanism for WSNs without the threshold limitation. Itdevises network implementation criteria on source node privacy protection in WSNs. It proposes an efficient key management framework to ensure isolation of the compromised nodes. To the best of our knowledge, this is the first scheme that provides hop-by-hop node authentication without the threshold limitation, and has performance better than the symmetric-key based schemes. The distributed nature of our algorithm makes the scheme suitable for decentralized networks.
3.1 SYSTEM ARCHITECTURE
DESIGN
The architecture diagram clearly explains hop by hop authentication features
and functionalities. The fig 4.2 describe about the system architecture for the proposed system.
Fig 3.1 System Architecture
Data are communicated from one node to another node in the above process. First the source node will send the data it is passed into the automatic key generator here a secrete key will be generated automatically for the source node. After the key is generated data is passed into the network with key value in the data.
Above process is made for each and every node in the network by generating its own key until it reaches the destination.
When the data reach its destination it will check for the key of destination node, once validated data is delivered.
3.2 ARCHITERCTURE DIAGRAM
The architectural diagram for hop by hop message authentication.
105
When the data is transmitted from source to destination, Communication will be established in 2 ways either hop by hop or multihop.The intermediate nodes are taken as load node. When there is energy drain in load nodes, alternative node can be replaced. This protocol is named as active protocol. Here Multicasting is also applied, so every node will easily knows the maximum energy level of other nodes.
4. MODULEDESCRIPTION
4.1 NODE FORMATION MODULE
This module is formation of nodes what all needed for sending and receiving information.
One node is assumed as sender node and another node is assumed as receiver node. And some nodes are assumed as information passing nodes.
4.2 DATA TRANSMISSION MODULE
The sender node sends the information to the receiver node through this module. These modules have an option for sending the file from one location to the other location. Each node hasan identity using the IP address.
4.3 DATA RECEIVING AND
VERIFICATION MODULE
This module is for receiving the information. It checks whether the information is coming from secure sender and from the correct path. After authentication, the receiver receives the information through the secure nodes.
4.4 EXPERIMENTAL RESULTS
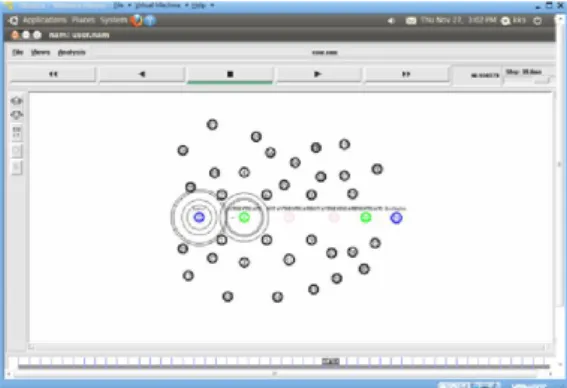
The below screenshots will describe how the proposed system for identifying the adjacent nodes in the network.
Fig 4.1 Viewing Adjacent Nodes
In Fig 5.1 shows the adjacent nodes which are between source and destination. Each node hasa automatic key value that will be generated, when the data passed through that node.
Fig 4.2Authenticating Each Node while sending data
106
5.2 while visiting each node automatic key authentication is made on that node. While transferring data from one node to another node there is a possible for data loss, above Fig 5.3 shows the data loss in node.
Fig 4.3 Finding Unauthenticated Node
Once data loss is occur it seems that the original data doesn’t reach the destination. The above Fig 5.4 check for unauthenticated node in that path.
After identifying alternate node, those nodes are placed in the appropriate location. Now the source node will retransmit the data to the destination node. Finally data is reached in the destination node without data loss.
Fig 4.4 Removing the Unauthenticated Node
In Fig 5.55 the red color node in the path indicates the unauthenticated node.
Once the nodes are identified those nodes are removed from the path.
After the nodes are removed, the destination node will find the alternate node and placed in that path.
5. CONCLUSION
Here the concluded information is the proposed efficient source intermediate node message authentication scheme based on signature and ID generation provides high security than the other methods in the existing research. The excepting results is, our proposed scheme is moreefficient than the bivariate polynomial-based scheme in termsof computational overhead, energy consumption, delivery ratio,message delay, and memory consumption.While ensuring message sender privacy, this scheme can be applied to any message to providemessage content authenticity.
6.REFERENCES
[1] Adrian Perrigy, Ran Canettiz J. D.
andTygary Dawn Song, “Efficient Authentication and Signing of Albrecht M, Gentry C, Halevi S, and Katz J, “Attacking Cryptographic Schemes Based on
‘Perturbation Polynomials’,” Report2009/098,
http://eprint.iacr.org/, 2009.
[2] Advances in Cryptology Proceedings of
CRYPTO '89, volume 435 of Lecture Notes in Computer Science, pages 235{251, Santa-Barbara, California, 1990. Springer-Verlag.
[3] Blundo C, De Santis A, Herzberg A, Kutten
S, Vaccaro U, andYung M, “Perfectly-Secure Key
Distribution for Dynamic Conferences,”Proc.
107
[4] David Pointcheval and Jacques Stern,
“Security Arguments for Digital Signatures and Blind Signatures”.
[5] David Pointcheval and Jacques
Stern,”Security Proofs for Signature Schemes”.
[6] ElGamalT.A., “A Public-Key Cryptosystem
and a SignatureScheme Based on Discrete
Logarithms,”IEEE Trans. InformationTheory, vol. IT-31, no. 4, pp. 469-472, July 1985.
[7] Fan Ye, HaiyunLuo, Songwu Lu, Lixia
Zhang, “Statistical En-route Filtering of Injected False Datain Sensor Networks”.
[8] Gaubatz,G, Kaps J, Ozturk E and Sunar B,
“State of the art in ultralow c key cryptography for wireless sensor networks,” 2005, pp. 146–150.
[9] Martin Albrecht, Craig Gentry and
ShaiHalevi, “Attacking Cryptographic Schemes Based on “Perturbation Polynomials””.
[10] Nyberg K and RueppelR.A, “Message
Recovery for SignatureSchemes Based on the Discrete Logarithm Problem,”Proc. Advances in Cryptology (EUROCRYPT), vol. 950, pp. 182-193, 1995.
[11] Perrig A, Canetti R, Tygar J, and Song D,
“Efficient Authentication and Signing of Multicast Streams over Lossy Channels,”Proc.IEEESymp. Security and Privacy, May 2000.
[12] Pointcheval D and Stern J, “Security
Arguments for Digital Signatures and Blind Signatures,”J. Cryptology, vol. 13, no. 3, pp. 361-396, 2000.
[13] Rivest R, Shamir A, and Adleman L. A
Method for Obtaining Digital Signatures and PublicKey Cryptosystems. Communications of the ACM, 21(2):120{126, February 1978.
[14] Schnorr C P, E_cientIdenti_cation and