Protocol(ACSP)
Masoumeh Safkhani1
, Nasour Bagheri2
and Majid Naderi1
1
Electrical Engineering Department, Iran University of Science and Technology, Tehran, Iran. {M Safkhani,M Naderi}@iust.ac.ir
2
Electrical Engineering Department, Shahid Rajaee Teacher Training University, Tehran, Iran.
NBagheri@srttu.edu
Abstract. Recently Qianet al.[38] have proposed a new attack for RFID systems, called counting
attack, where the attacker just aims to estimate the number of tagged objects instead of steal the tags’ private information. They have stated that most of the existing RFID mutual authentication protocols are vulnerable to this attack. To defend against counting attack, they propose a novel Anti-Counting Security Protocol called ACSP. The designers of ACSP have claimed that their protocol is resistant against counting attack and also the other known RFID security threats. However in this paper we present the following efficient attacks against this protocol:
– Tag impersonation attack: the success probability of attack is ”1” while the complexity is two
runs of protocol.
– Two single tag de-synchronization attacks, the success probability of both attacks are ”1” while
the complexity is at most two runs of protocol.
– Group of tags de-synchronization attack: this attack, which can de-synchronize all tags in the
range at once, has success probability of ”1” while its complexity is one run of protocol. .
– Traceability attack: the adversary’s advantage in this attack is almost 1
2, which is almost the
maximum of possible advantages for an adversary in the same model. The complexity of attack is three runs of protocol
Keywords: RFID, Authentication, Counting attack, ACSP, Tag Impersonation Attack, De-synchronization Attack, Traceability Attack.
1 Introduction
Radio Frequency Identification (RFID) systems consist of a reading device called reader and one or more tags. The reader is a powerful device which can read/modify the tag’s information. Tags are very constraint devices that range from passive tags, which respond only at reader commands, to active tags, which have an on-board power supply.
The design of secure authentication protocols for low-cost RFID tags has received the at-tention of a lot of researchers, though many protocols have been published lately [1, 4, 6–12, 15–19, 21, 22, 27, 28, 30–37]. However, most of them have not satisfied the claimed security goles [1–3, 5, 13, 14, 19, 20, 23–30]. The security of an RFID protocol can be analyzed in sev-eral direction. For example, an adversary may be interested in tracking the tag holder which can compromise the tag holder privacy or it may try to clone a legitimate tag to pay less. We can classify the main known attacks in the field of RFID as follows:
– Forgery attacks that include:
• Tag impersonation
• Reader impersonation
– Secret disclosure attacks that include:
• Reader’s secret values, e.g. shredkey, disclosure attack
• Tag’s secret values, e.g. tag’sID, disclosure attack – De-synchronization attacks
– Cloning attacks – Replay attacks
Recently, Qian et al. have proposed a new attack, called counting attack, in which the adversary’s target is to estimate the number of tagged objects. They have stated that most of the existing RFID protocols are vulnerable to counting attack. In addition, to defend against this attack, they have proposed a new protocol entitled ACSP [38]. Qian et al. have claimed that ACSP is secure against counting attack and also against the other attacks in the context. However, we show that their claims do not hold.
Paper Contributions: In this paper we show three kinds of attacks against ACSP. The first attack is the tag impersonation attack which is able to forces the reader to authenticate the adversary as a legitimate tag. The second attack is a de-synchronization attack which is able to de-synchronize the communication between the tag and the reader and the third attack is a traceability attack which is able to trace tags and compromise the privacy of the tag holder. The success probability of all attacks is ”1”, the complexity of any given attack is at most two runs of protocol and the main computation cost of any attack is at most one calculation of hash function and one calculation ofCRC function.
Paper Organization: The notations used in the paper are presented in Section 2. The ACSP protocol is briefly described in Section 3. In Section 4 we describe our impersonation attack which can be considered as synchronization attack also. We present another de-synchronization attack which is de-synchronize a single tag and the reader in Section 5. In Section 6, we present another de-synchronization which de-synchronizes all tages in the range. Traceability attack is described in Section 7. Finally, we conclude the paper in Section 8.
2 Preliminaries
Throughout the paper, we use the following notations:
• R: RFID reader.
• T: RFID tag.
• SID: The session identifier.
• SIDcur: The current session identifier.
• SIDnew: The new session identifier used in the following communica-tion session.
• T ID: The current unique identifier of tag.
• T IDnew: The next identifier of tag used in the following communica-tion session.
• Ri,1≤i≤5: Pseudo random numbers that are generated by the reader or the tag.
• H(x1, x2): One way hash function with variablesx1 and x2.
• CRC: Cyclic Redundancy Code.
• M ASKV AL: Bit mask.
• ⊕: Exclusive-or operation.
• A: Adversary.
• SELECT: Select command.
• QU ERY: Query command.
• IDEN T: identification message from tag, containing T ID informa-tion.
• AU T HEN: Authentication message.
• U ERY REP: End current slot command.
• QU ERY ADJU ST: End current slot command.
Each message which is sent from the reader to the tag or wise versa includes aM SGHEADER, the message body and the CRC of the message. The M SGHEADER can be SELECT,
QU ERY,IDEN T,AU T HEN,U ERY REP orQU ERY ADJU ST.
3 ACSP Description
Recently Qian et al. [38] have proposed a new attack for RFID system which has been called counting attack. The attacker’s goal in counting attack is to estimate the number of tagged objects instead of stealing private information of tags. They have stated [38] that most of the existing RFID mutual authentication protocols are vulnerable to counting attack. To defend against this attack, they have proposed a novel anti-counting security protocol or in short term called ACSP [38]. In this section we present a brief description of ACSP.
ACSP is composed of two phases: SID Update and Tag Identification that described sepa-rately in below:
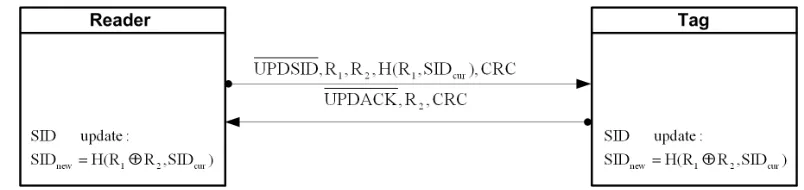
SID Update Phase: This phase of protocol, which is depicted in Fig.2, accomplishes as below:
1. The reader generates two random numbersR1andR2and sends (U P DSID, R1, R2, H(R1 , SIDcur), CRC) to the tag.
2. Upon receipt of the message, each tag checks the values ofH(R1, SIDcur) and CRC to verify whether the command is valid. If it is valid, tags update localSID asSIDnew=
H(R1⊕R2, SIDcur).
Tag Identification Phase: This phase of protocol, which is depicted in Fig. 1, works as follows:
1. The reader R generates a random number R3 and sends (SELECT , R3, H(R3, SID),
(M ASKV AL⊕SID), CRC), to the target tag.
2. Upon receipt of the message, any tag Ti checks the included CRC, R3 and corre-sponding H(R3, SID). If all are correct, the tag extracts M ASKV AL by calculating (M ASKV AL⊕SID)⊕SID. If the tag’sIDmatchesM ASKV AL, the tag gets ready to respond, otherwise the tag keeps silent until receiving the next Select command. 3. R generates a random numberR4 and sends (QU ERY , R4, H(R4, SID), CRC).
4. Upon receipt of the message, a ready tagTichecksCRCand correctness of (R4, H(R4, SID)) in the Query command. If they are correct, it generates a random number R5 and
re-sponds with (IDEN T , R5, H(R4, T ID), CRC) as identification message.
5. Upon receipt of the identification message without collision, R proceeds as follows: (a) It will search for the tag’s T ID in its database according to R4 andH(R4, T ID).
(b) If R finds theT ID of the tag it does as follows:
– Updates tag’sT ID asT IDnew=H(R4⊕R5, T ID). – Sends (AU T HEN , H(R5, T ID), CRC) to the tag.
(c) Else, the reader sends (QU ERY REP /QU ERY ADJU ST , Rp, H(Rp, SID), CRC) to end this slot and start a new one.
6. The tag receives (AU T HEN , H(R5, T ID), CRC) and upon receipt of these values, it
checksH(R5, T ID) and proceeds as follows:
(a) If it is correct, it update its ID asID=H(R4⊕R5, T ID).
Fig. 1.The ACSP’s Tag Identification Phase.
Fig. 2. The ACSP’s SID Update Phase.
4 Tag Impersonation Attack
Tag impersonation attack is a forgery attack in which the reader accepts a spoofed tag as a legitimate tag. Any secure RFID authentication protocols must resistance against all kind of forgery attacks, include tag impersonation attack. In this section, we prove that ACSP is vulnerable to tag impersonation attack. In our tag impersonation attack, to impersonate the tagTi the adversary (A) can follow the bellows steps:
Phase 1: Retrieving T IDnew
1. The reader R generates a random number R3 and sends (SELECT , R3, H(R3, SID),
(M ASKV AL⊕SID), CRC), to the target tag Ti. A does not change the transferred message of this step.
2. Upon receipt of the message, any tag Tj checks the included CRC, R3 and corre-sponding H(R3, SID). If all are correct, the Ti extracts M ASKV AL by calculating
(M ASKV AL⊕SID)⊕SID. If the tag’s ID matches M ASKV AL, Ti gets ready to respond, otherwise it keeps silent until receiving the next Select command. A does not change the transferred message of this step.
3. Rgenerates a random number R4 and sends (QU ERY , R4, H(R4, SID), CRC).Adoes not change the transfered message of this step.
4. Upon receipt of the message, a ready tagTichecksCRCand correctness of (R4, H(R4, SID)) in the Query command. If they are correct, it generates a random number R5 and re-sponds with (IDEN T , R5, H(R4, T ID), CRC) as identification message.
5. Aintercepts (IDEN T , R5, H(R4, T ID), CRC), changes theR5 value to zero, computes the correspondingCRCofIDEN T ,0, H(R4, T ID) and sends(IDEN T ,0, H(R4, T ID), CRC) to the reader.
6. Upon receipt of the identification message without collision, R proceeds as follows: (a) It will search for the tag’s T ID in its database according to R4 andH(R4, T ID). (b) If R finds theT ID ofTi, which will find, it does as follows:
7. Ablocks this message.
Hence, following the above procedure, the adversary knows the T IDnew =H(R4, T ID), the
secret T ID ofTi stored in the reader database.
Phase 2: Tag impersonation : to impersonate the tag, Awaits until the reader initiates a new session to identify any tag Tjwhere:
1. Rgenerates a random numberR3and sends (SELECT , R3, H(R3, SID),(M ASKV AL⊕
SID), CRC).
2. Upon receipt of the message,A gets ready to respond.
3. R generates a random numberR4 and sends (QU ERY , R4, H(R4, SID), CRC). 4. Upon receipt of the message, A blocks any responds from other tags towards R and
generates a random numberR5 and responds with (IDEN T , R5, H(R4, T ID), CRC) as identification message, whereT ID has has been retrieved from Phase 1 of attack. 5. Upon receipt of the identification message without collision, R proceeds as follows:
(a) It will search for the tag’s T ID in its database according to R4 andH(R4, T ID).
(b) It finds theT ID of Ti and does as follows:
– UpdatesTi’sT IDasT IDnew=H(R4⊕R5, T ID) =H(R4⊕0, T ID) =H(R4, T ID). – Sends (AU T HEN , H(R5, T ID), CRC) to Ti.
6. Aupdates its record ofT ID toT IDnew=H(R4⊕R5, T ID).
So the reader authenticates adversary as a legitimate tag and updates tag’sT ID. The success probability of above attack is ”1” and the complexity is only two successive runs of protocol. We emphasis that, as it has been indicated in the attack, onPhase 2 of the attack the adversary does not need to wait for an special session of protocol between R and the target tag Ti to impersonateTi but it can impersonateTi on any run of protocol afterPhase 1of attack, where the adversary retrievesT ID of Ti.
Remark 1. After the successful run of the given tag impersonation attack, the reader authen-ticates the adversary as a legitimate tag and updates tag’s T ID while the legitimate tag has not updated itsT ID. Hence, the reader and the legitimate tag will not authenticate each other anymore in the following transactions. Therefore, the given impersonation attack leads to de-synchronization attack.
Remark 2. To overcome the potential de-synchronization attack because of the message lost problem occurring in the tag identification procedure, designers suggested [38, Sec. 6] that the reader preserves a copy ofT ID used in the last successful identification for each tag. However, this modification also does not improve the security of the protocol against the proposed attack.
5 Single Tag De-synchronization Attack
In de-synchronization attack, the adversary forces the tag and the reader to update their com-mon values to different values from each other. If the adversary can be succeed in forcing the tag and the reader to do so, they will not authenticate each other in the further transactions. Qianet al.[38] have stated that it is possible to desynchronize the tag and the reader in ACSP if the adversary block the transferred message from the reader to the tag in step 5b and to solve the problem , as an enhanced protocol, they suggested [38, Sec. 6] that the reader preserves a copy ofT IDused in the last successful identification for each tag. However, in section 4 we have described a powerful tag impersonation attack which also desynchronize the target tag and the reader in their original and enhanced protocols.
an adversary AchangesR5 and CRC properly, there is now way for the tag to understand the modification. We use this observation in our de-synchronization attack against ACSP. In this attack, Adoes as follows:
– A lets step 1 and step 2 of protocol to be run without any change.
– Aintercepts the message of step 3 of protocol and changes the value ofR5to some arbitrary
value, i.e.R5⊕∆, and computes the correspondingCRC of (IDEN T , R5⊕∆, H(R4, T ID)) denoted by CRC′
. Then it sends (IDEN T , R5⊕∆, H(R4, T ID), CRC′
) to the reader. – The reader authenticates the man in the middle adversary as a legitimate tag. Then R
updates tag’s T ID asT IDnew=H(R4⊕R5⊕∆, T ID).
It must be noted that the reader updates the tag’s T ID by R5⊕∆ while the tag does
not update its T ID so they cannot authenticate each other in the following transactions. The success probability of above attack is ”1” and the complexity is only one run of protocol.
6 Group De-synchronization Attack
In this section we introduce an attack which is desynchronized all tags in the range. It must be noted that in ACSP the reader and tags share the session identifier, SID. This value gets updated periodically following the SID Update Phase 3 of protocol. However, if an adversary forces the tag to updates its SIDnew to a different value compared to the value in the reader side, then the Tag Identification Phase 3 of protocol can not be run properly and the tag and the reader will be desynchronized. In addition, in SID Update Phase of protocol, all tags must update their SID, otherwise they will lost their synchronization with the reader. On the other hand, to update SID, the reader generates two random numbers R1 and R2 and sends (U P DSID, R1, R2, H(R1, SIDcur), CRC) to tags. Each tag, upon receipt of the message,
checks the values ofH(R1, SIDcur) andCRC and if it is valid it updates localSIDasSIDnew=
H(R1⊕R2, SIDcur). It can be seen that the adversary A can do as follows:
1. A intercepts the message, 2. changes R2 toR′
2 6=R2,
3. calculates the CRC′
=CRC(U P DSID, R1, R2, H(R1, SIDcur)),
4. and broadcasts (U P DSID, R1, R2, H(R1, SIDcur), CRC) to all tags in the range.
Obviously, the modified message will pass the tags verification test and all tags in the range will update theirSIDtoSIDnew=H(R1⊕R′2, SIDcur). Since with a high probabilityH(R1⊕
R2, SIDcur)6=H(R1⊕R2′, SIDcur) (the exact probability is 1−2−nwhere nis length ofSID in bits), all tags are desynchronized from the reader. The success probability of above attack is almost ”1” and the complexity is only one run of protocol.
Remark 3. It must be noted that the designers have discussed [38, Sec. 6] that the the tag and the reader will be de-synchronized if tag does not receive the U P DSID command. To overcome this problem they suggested any tag to send a update acknowledge command as (U P DACK, R2, CRC) to the reader. However, this message can be generated by the adversary and sent to the reader because it does not include any secret parameter. Therefore, the enhanced protocol is also vulnerable to the given attack.
7 Traceability Attack
1 for to Tj = T1 cases. A’s success in winning the traceability game G is equivalent to the success of breaking the untraceability property offered by the protocol. So the advantage of A
in distinguishing whether the messages correspond to Ti or not is defined as below:
AdvAUNT(q, kr) =|P r[ebiscorrect]−
1 2|
where q is a security parameter (i.e. the bit length of the key shared between the tag and the reader) and kr is the number of timesA runs the protocol. Our traceability attack is described as below:
Phase 1: Learning , in this phase of attack the adversary de-synchronize Ti and R. In addition, though the de-synchronization attack it can achive the required information to trace Ti later.
1. AdesynchronizeTi and Rfollowing the given tag impersonation attack which also leads to de-synchronization(refer to 1) and store the following messages transfered betweenR
toTi, include:
– (SELECT , R3, H(R3, SID),(M ASKV AL⊕SID), CRC), from R toTi. – (QU ERY , R4, H(R4, SID), CRC),from R toTi.
– (IDEN T , R5, H(R4, T ID), CRC),from Ti toR.
Phase 2: Challenge , in this phase of protocol the adversary does as follows:
1. A sends the eavesdropped (SELECT , R3, H(R3, SID), (M ASKV AL⊕SID), CRC) to the target tagTj.
2. Upon receipt of the message,Tjchecks the includedCRC,R3and correspondingH(R3, SID). IfTi =Tjthen all are correct andTiextractsM ASKV ALby calculating (M ASKV AL⊕
SID)⊕SID. The tag’s ID matchesM ASKV AL,Ti gets ready to respond. If Ti 6=Tj it will keep silence.
3. Asends the eavesdropped (QU ERY , R4, H(R4, SID), CRC) toTj.
4. Upon receipt of the message, ifTjis ready, it checksCRCand correctness of (R4, H(R4, SID)) in the Query command which. If they are correct then it generates a random numberR′
5
and responds with (IDEN T , R′
5, H(R4, T ID′), CRC′) as identification message.
5. Aeavesdropped (IDEN T , R′
5, H(R4, T ID′
), CRC′
) and go to the next phase of attack. Phase 3: Guessing , A finishes G and outputs a bit eb as its conjecture of the value b. In
particular,A utilizes the following simple decision rule in generating the decision biteb: (
ifH(R4, T ID) ==H(R4, T ID′) eb= 1
if X 6=Y eb= 0 (1)
In the given attack, the adversary desynchronize the reader and the target tag Ti at the first phase of attack. Hence,Ti will not update its secret parameters includeSIDandT ID. On the other hand, as long as SID and T ID are fixed, the eavesdropped values in the Learning phase of attack are pass the tags verification tests in the protocol and the adversary will expect the sameH(R4, T ID) from the tag to be included in itsIDEN T command. Hence, ifTi=Tj then with the probability of “1” we have H(R4, T ID) == H(R4, T ID′). However, if Ti 6= Tj
then with a negligible probability H(R4, T ID) ==H(R4, T ID′). This probability is less than
2−n, wheren is the output length of hash function,H(.). Therefore, the success probability of adversary to output the correctebis lower bounded by 1−2−n. Hence, the adversary advantage in wining the game is as follows, which is almost the maximum of possible advantages:
AdvAUNT(q,1) =|1−2−n−1
2|=| 1 2−2
−n|
8 Conclusion
In this paper we considered the ACSP, UHF RFID mutual authentication protocol. Based on its designers’ climes this protocol is supposed to resist counting attack and the other known attacks against an RFID system. However, we presented several efficient attack against this protocol with high success probability. Our attacks include tag impersonation attack, single tag de-synchronization attack, group of tags de-synchronization attack and traceability attack. The success probability of all attacks are almost ”1” and the complexity are at most three runs of the protocol. Hence, ACSP is not a secure protocol for an ordinary applications of RFID systems.
References
1. N. Bagheri, P. Peris-Lopez, M. Safkhani, M. Naderi, and J. C. Hernandez-Castro. On the Security of Tanet al.Serverless RFID Authentication and Search Protocols. Manuscript, 2011.
2. N. Bagheri, M. Safkhani, M. Naderi, and S. K. Sanadhya. Security Analysis ofLM AP++, an RFID
Authen-tication Protocol. Cryptology ePrint Archive, Report 2011/193, 2011. http://eprint.iacr.org/.
3. M. B´ar´asz, B. Boros, P. Ligeti, K. L´oja, and D. Nagy. Passive Attack Against the M2AP Mutual Authenti-cation Protocol for RFID Tags. InFirst International EURASIP Workshop on RFID Technology, Vienna, Austria, September 2007.
4. M. Burmester, B. de Medeiros, J. Munilla, and A. Peinado. Secure EPC gen2 compliant radio frequency identification. In P. M. Ruiz and J. J. Garcia-Luna-Aceves, editors,ADHOC-NOW, volume 5793 ofLecture Notes in Computer Science, pages 227–240. Springer, 2009.
5. T. Cao, E. Bertino, and H. Lei. Security Analysis of the SASI Protocol. IEEE Trans. Dependable Sec. Comput., 6(1):73–77, 2009.
6. H.-Y. Chien and C.-H. Chen. Mutual authentication protocol for RFID conforming to EPC class 1 generation 2 standards. Computer Standards & Interfaces, 29(2):254–259, 2007.
7. J.-S. Cho, S.-S. Yeo, and S. K. Kim. Securing against brute-force attack: A hash-based RFID mutual authentication protocol using a secret value. volume 34, pages 391–397, 2011.
8. E. Y. Choi, D. H. Lee, and J. I. Lim. Anti-cloning protocol suitable to EPCglobal class-1 generation-2 RFID systems. Computer Standards & Interfaces, 31(6):1124–1130, 2009.
9. Class-1 generation 2 UHF air interface protocol standard version 1.2.0, Gen2, 2008.
http://www.epcglobalinc.org/standards/. InGen-2 Standard. EPCGlobal, 2008.
10. EPC Tag data standar dversion 1.4.2008. http://www.epcglobalinc.org/standards/. Yearly report on al-gorithms and keysizes, Technical Report D.SPA.13Rev.1.0,ICT-2007-216676,. InGen2 Standard. ECRYPT, 2010.
11. C. Hung-Yu. SASI: A New Ultralightweight RFID Authentication Protocol Providing Strong Authentication and Strong Integrity. IEEE Transactions on Dependable and Secure Computing, 4(4):337–340, December 2007.
12. T. Li. Employing Lightweight Primitives on Low-Cost RFID Tags for Authentication. InVTC Fall, pages 1–5. IEEE, 2008.
13. T. Li and R. H. Deng. Vulnerability Analysis of EMAP - An Efficient RFID Mutual Authentication Protocol. InSecond International Conference on Availability, Reliability and Security - AReS 2007, Vienna, Austria, April 2007.
14. T. Li and R. H. Deng. Vulnerability analysis of EMAP-an efficient RFID mutual authentication protocol. InARES, pages 238–245. IEEE Computer Society, 2007.
15. N.-W. Lo and K.-H. Yeh. An efficient mutual authentication scheme for EPCglobal class-1 generation-2 RFID system. In M. K. Denko, C.-S. Shih, K.-C. Li, S.-L. Tsao, Q.-A. Zeng, S.-H. Park, Y.-B. Ko, S.-H. Hung, and J. H. Park, editors,EUC Workshops, volume 4809 ofLecture Notes in Computer Science, pages 43–56. Springer, 2007.
16. P. Peris-Lopez, J. C. H. Castro, J. M. Est´evez-Tapiador, and A. Ribagorda. M2ap: A minimalist mutual-authentication protocol for low-cost rfid tags. In J. Ma, H. Jin, L. T. Yang, and J. J. P. Tsai, editors,
Ubiquitous Intelligence and Computing, Third International Conference, volume 4159 ofLecture Notes in Computer Science, pages 912–923. Springer, 2006.
17. P. Peris-Lopez, J. C. H. Castro, J. M. Est´evez-Tapiador, and A. Ribagorda. Advances in Ultralightweight Cryptography for Low-Cost RFID Tags: Gossamer Protocol. In K.-I. Chung, K. Sohn, and M. Yung, editors,
WISA, volume 5379 ofLNCS, pages 56–68. Springer, 2008.
19. P. Peris-Lopez, J. C. Hernandez-Castro, J. E. Tapiador, and J. C. A. van der Lubbe. Cryptanalysis of an EPC class-1 generation-2 standard compliant authentication protocol. Eng. Appl. of AI, 24(6):1061–1069, 2011.
20. P. Peris-Lopez, T. Li, J. C. Hernandez-Castro, and J. E. Tapiador. Practical attacks on a mutual authentica-tion scheme under the EPC class-1 generaauthentica-tion-2 standard.Computer Communications, 32(7-10):1185–1193, 2009.
21. A. Sadighian and R. Jalili. FLMAP: A Fast Lightweight Mutual Authentication Protocol for RFID Systems. InThe 16th IEEE International Conference On Networks (ICON 2008), pages 1–6, New Delhi, India, 2008. 22. A. Sadighian and R. Jalili. AFMAP: Anonymous Forward-Secure Mutual Authentication Protocols for RFID systems. In R. Falk, W. Goudalo, E. Y. Chen, R. Savola, and M. Popescu, editors,The Third IEEE International Conference on Emerging Security Information, Systems and Technologies(SECURWARE 2009), pages 31–36, Athens, Greece, 2009. IEEE Computer Society.
23. M. Safkhani, N. Bagheri, and M. Naderi. Cryptanalysis of Chen et al.’s RFID Access Control Protocol. Cryptology ePrint Archive, Report 2011/194, 2011. http://eprint.iacr.org/.
24. M. Safkhani, N. Bagheri, M. Naderi, and hamid Behnam. On the Security of Wei et al.’s RFID Mutual Authentication Protocol. Manuscript, 2011.
25. M. Safkhani, N. Bagheri, M. Naderi, Y. Luo, and Q. Chai. Tag Impersonation Attack on Two RFID Mutual Authentication Protocols. InFARES, 2011.
26. M. Safkhani, N. Bagheri, P. Peris-Lopez, M. Naderi, and J. C. Hernandez-Castro. Cryptanalysis of Choet al.’s Protocol, A Hash-Based Mutual Authentication Protocol for RFID Systems. Manuscript, 2011. 27. M. Safkhani and M. Naderi. Cryptanalysis and Improvement of a Lightweight Mutual Authentication
Proto-col for RFID system. In 7th
International ISC Conference on Information Security and Cryptology 2010(IS-CISC’10), pages 57–59, 2010.
28. M. Safkhani, M. Naderi, and N. Bagheri. Cryptanalysis of AFMAP. IEICE Electronics Express, 7(17):1240– 1245, 2010.
29. M. Safkhani, M. Naderi, N. Bagheri, and S. K. Sanadhya. Cryptanalysis of Some Protocols for RFID Systems. Cryptology ePrint Archive, Report 2011/061, 2011. http://eprint.iacr.org/.
30. M. Safkhani, M. Naderi, and H. F.Rashvand. Cryptanalysis of the Fast Lightweight Mutual Authenti-cation Protocol (FLMAP). International Journal of Computer & Communication Technology (IJCCT), 2(2,3,4):182–186, 2010.
31. J. Shen, D. Choi, S. Moh, and I. Chung. A Novel Anonymous RFID Authentication Protocol Providing Strong Privacy and Security. In2010 International Conference on Multimedia Information Networking and Security, 2010.
32. C. C. Tan, B. Sheng, and Q. Li. Secure and Serverless RFID Authentication and Search Protocols. IEEE Transactions on Wireless Communications, 7(4):1400–1407, 2008.
33. C.-H. Wei, M.-S. Hwang, and A. Y. Chin. A Mutual Authentication Protocol for RFID. IT Professional, 13(2):20–24, 2011.
34. S. A. Weis, S. E. Sarma, R. L. Rivest, and D. W. Engels. Security and privacy aspects of low-cost radio frequency identification systems. In D. Hutter, G. M¨uller, W. Stephan, and M. Ullmann, editors, SPC, volume 2802 ofLecture Notes in Computer Science, pages 201–212. Springer, 2003.
35. W. W. Y. Gu. A light-weight mutual authentication protocol for ISO 18000-6B standard RFID system . In
Proceedings of ICCTA 2009, pages 21–25, 2009.
36. T.-C. Yeh, Y.-J. Wang, T.-C. Kuo, and S.-S. Wang. Securing RFID systems conforming to EPC class 1 generation 2 standard. Expert Syst. Appl, 37(12):7678–7683, 2010.
37. G. G. Yiyuan Luo, Qi Chai and X. Lai. A lightweight Stream Cipher WG-7 for RFID Encryption and Authentication. InIEEE Globecom 2010 proceedings, 2010.
38. Zhuzhong Qian , Ce Chen, Ilsun You, Sanglu Lu. ACSP: A novel security protocol against counting at-tack for UHF RFID systems. In Elsevier, Computers and Mathematics with Applications, volume ? of