Sensor Networks
by
Hani Alzaid
Bachelor of Computer Engineering(King Saud University)– 2000
Master of Computer Science and Engineering(University of New South Wales)– 2005
Thesis submitted in accordance with the regulations for the
Degree of Doctor of Philosophy
Information Security Institute
Faculty of Science and Technology
Queensland University of Technology
Secure data aggregation, wireless sensor networks, performance analysis, security analysis, reputation systems, trust systems, node compromise, attacks, cryptographic-based solutions, reputation-based solutions, forward & backward secure key management, On-Off attacks,
A Wireless Sensor Network (WSN) is a set of sensors that are integrated with a physical en-vironment. These sensors are small in size, and capable of sensing physical phenomena and processing them. They communicate in a multihop manner, due to a short radio range, to form an Ad Hoc network capable of reporting network activities to a data collection sink. Recent advances in WSNs have led to several new promising applications, including habitat monitoring, military target tracking, natural disaster relief, and health monitoring.
The current version of sensor node, such as MICA2, uses a 16 bit, 8 MHz Texas Instruments MSP430 micro-controller with only 10 KB RAM, 128 KB program space, 512 KB external flash memory to store measurement data, and is powered by two AA batteries. Due to these unique specifications and a lack of tamper-resistant hardware, devising security protocols for WSNs is complex. Previous studies show that data transmission consumes much more energy than computation. Data aggregation can greatly help to reduce this consumption by eliminating redundant data. However, aggregators are under the threat of various types of attacks. Among them, node compromise is usually considered as one of the most challenging for the security of WSNs. In a node compromise attack, an adversary physically tampers with a node in or-der to extract the cryptographic secrets. This attack can be very harmful depending on the security architecture of the network. For example, when an aggregator node is compromised, it is easy for the adversary to change the aggregation result and inject false data into the WSN. The contributions of this thesis to the area of secure data aggregation are manifold. We firstly define the security for data aggregation in WSNs. In contrast with existing secure data aggregation definitions, the proposed definition covers the unique characteristics that WSNs have. Secondly, we analyze the relationship between security services and adversarial models considered in existing secure data aggregation in order to provide a general framework of required security services. Thirdly, we analyze existing cryptographic-based and reputation-based secure data aggregation schemes. This analysis covers security services provided by these schemes and their robustness against attacks. Fourthly, we propose a robust reputation-based secure data aggregation scheme for WSNs. This scheme minimizes the use of heavy cryptographic mechanisms. The security advantages provided by this scheme are realized by integrating aggregation functionalities with: (i) a reputation system, (ii) an estimation theory, and (iii) a change detection mechanism. We have shown that this addition helps defend against most of the security attacks discussed in this thesis, including the On-Off attack. Finally, we
between Lamport’s reverse hash chain as well as the usual hash chain to provide both past and future key secrecy. The proposal avoids the delivery of the whole value of a new group key for group key update; instead only the half of the value is transmitted from the network manager to the sensor nodes. This way, the compromise of a pairwise key alone does not lead to the compromise of the group key. The new pairwise key in our scheme is determined by Diffie-Hellman based key agreement.
Front Matter i Keywords . . . i Abstract . . . iii Table of Contents . . . v List of Figures . . . ix List of Tables . . . xi Declaration . . . xiii
Previously Published Material . . . xv
Acknowledgements . . . xvii
1 Introduction 1 1.1 Background . . . 1
1.2 Challenges in Wireless Sensor Networks . . . 3
1.2.1 Challenges in the End Device . . . 4
1.2.2 Challenges in the Network . . . 5
1.3 Data Aggregation and Security Challenges . . . 6
1.4 Research Objectives . . . 7
1.5 Outline . . . 9
2 Secure Data Aggregation in Wireless Sensor Networks 13 2.1 Secure Data Aggregation in Wireless Sensor Networks . . . 14
2.1.1 Security Requirements for Data Aggregation Security . . . 15
2.2 The Expected Adversarial Model and Security Concerns . . . 17
2.2.1 Security Attacks . . . 17
Sybil Attack (SY) . . . 17
Selective Forwarding Attack (SF) . . . 18
Replay Attack (RE) . . . 19
Spoofed Data Attack (SD) . . . 19
2.2.2 Adversary Classification . . . 21
2.3 Current Secure Data Aggregation Schemes . . . 22
2.3.1 Single Aggregator Model . . . 23
Du et al.’s Scheme . . . 24
Przydatek et al.’s Scheme . . . 25
2.3.2 Multiple Aggregator Model . . . 31
Hu & Evans’s Scheme . . . 32
Jadia & Mathuria’s Scheme . . . 34
Westhoff et al.’s Scheme . . . 35
Yang et al.’s Scheme . . . 38
2.4 Security Analysis . . . 40
2.4.1 Security Services . . . 41
2.4.2 Attack Vulnerability . . . 44
2.4.3 Framework for Evaluating New Schemes . . . 45
2.5 Performance Analysis . . . 46
2.5.1 First Scenario: No Aggregation & No Security . . . 47
2.5.2 Second Scenario: Aggregation but No Security . . . 48
2.5.3 Third Scenario: Hu & Evans’s Scheme . . . 48
2.5.4 Fourth Scenario: Jadia & Mathuria’s Scheme . . . 49
2.5.5 Fifth Scenario: Przydatek et al.’s Scheme . . . 49
2.5.6 Sixth Scenario: Du et al.’s Scheme . . . 50
2.5.7 Example . . . 51
2.6 Summary . . . 52
3 Reputation-based Trust Systems in Wireless Sensor Networks 53 3.1 Analysis Framework for Reputation Systems . . . 55
3.1.1 Information Gathering and Sharing Phase . . . 55
3.1.2 Information Modeling Phase . . . 57
3.1.3 Decision Making Phase . . . 58
3.1.4 Dissemination Phase . . . 59
3.2 Security Attacks against Reputation-based Trust Systems . . . 60
Bad Mouthing Attack (BM) . . . 60
Ballot Stuffing Attack (BS) . . . 61
On-Off Attack (OO) . . . 62
Newcomer Attack (NE) . . . 64
3.3 The State of the Art of Reputation-based Trust Systems in WSNs . . . 64
3.3.1 Boukerche & Ren’s Scheme . . . 64
3.3.2 Shaikh et al.’s Scheme . . . 66
3.3.3 Michiardi & Molva’s Scheme . . . 68
3.3.4 Srinivasan et al.’s Scheme . . . 69
3.3.5 Ozdemir’s Scheme . . . .¨ 70
3.4 Comparison of Current Reputation-based Systems in WSNs . . . 71
3.4.1 Classification Model . . . 72
3.4.2 Reputation Components . . . 73
3.4.3 Attack Vulnerability . . . 73
3.5 Summary . . . 76 vi
4.2 Data Model . . . 83
4.3 Adversarial Model . . . 83
4.4 Security Requirements . . . 84
4.5 The Proposal Reputation-based Secure Data Aggregation Scheme . . . 85
4.6 Experimental Evaluation . . . 92
4.6.1 Scenario 1: No Attacks . . . 95
4.6.2 Scenario 2: Abrupt Change . . . 96
4.6.3 Scenario 3: “1-per-2” Strategy On-Off Attack . . . 99
4.7 Security Analysis . . . 101
4.7.1 Reputation Components . . . 101
4.7.2 Security Services . . . 103
4.7.3 Attacks Resilience . . . 104
4.8 Summary . . . 106
5 Mitigating On-Off Attacks in Reputation-based Secure Data Aggregation 109 5.1 Related Work . . . 110
5.1.1 Estimation Theory . . . 110
5.1.2 Change Point Detection . . . 111
5.2 The Proposed Enhanced Reputation-based Secure Data Aggregation Scheme . . 112
5.3 Experiment Evaluation . . . 119
5.3.1 Scenario 1: No Attacks . . . 121
5.3.2 Scenario 2: Abrupt or Incipient Change . . . 122
5.3.3 Scenario 3: “1-per-2” Strategy On-Off Attack . . . 125
5.3.4 Scenario 4: “1-per-3” Strategy On-Off Attack . . . 131
5.4 Summary . . . 132
6 A Forward & Backward Secure Key Management in Wireless Sensor Net-works 135 6.1 Adversary Model and Security Concerns . . . 136
6.2 Related Work . . . 138
6.3 The Proposed Forward & Backward Secure Key Management Scheme - FBSKM 140 6.3.1 Group Key Update Protocol . . . 141
6.3.2 Pairwise Key Update Protocol . . . 142
6.3.3 Delivery Failure Management . . . 143
6.4 The Enhanced FBSKM (E-FBSKM) . . . 144
6.5 Security Analysis . . . 146
6.5.1 Robustness Against Adversaries . . . 146
6.5.2 Achievement of Past & Future Secrecy . . . 147
6.5.3 Resilience Against Impersonation Attacks . . . 149
6.6 Performance Analysis . . . 149
6.6.1 Memory Overhead . . . 149
6.7 Summary . . . 154
7 Conclusion and Future Work 157
7.1 Research Summary . . . 157 7.2 Future Work . . . 160
Bibliography 163
1.1 Main components of a sensor node . . . 2
1.2 An aggregation scenario using the SUM aggregation function . . . 7
2.1 Sybil Attack . . . 18
2.2 Selective Forwarding Attack . . . 19
2.3 Replay Attack . . . 20
2.4 Spoofed Data Attack . . . 20
2.5 Classification of adversaries . . . 22
2.6 A sketch of single and multiple aggregator models . . . 22
2.7 Classification of current secure data aggregation schemes . . . 24
2.8 A Merkle hash tree . . . 28
2.9 The proposed framework for secure data aggregation schemes . . . 45
2.10 The aggregation tree model used in the performance analysis section . . . 46
3.1 The reputation system phases . . . 55
3.2 Bad Mouthing Attack . . . 61
3.3 Ballot Stuffing Attack . . . 62
3.4 On-Off Attack . . . 63
3.5 Newcomer Attack . . . 63
3.6 A community as suggested in TOMS [12] . . . 65
3.7 Classification of current reputation-based trust systems in WSNs . . . 72
4.1 A simplified deployment area for ¨Ozdemir’s scheme . . . 80
4.2 The radio coverage inRSDA . . . 82
4.3 A simplified deployment area forRSDA . . . 87
4.4 The first scenario of RSDAevaluation in which dataset-1 is used . . . 95
4.5 The second scenario of RSDAevaluation in which dataset-2 is used . . . 97
4.6 The third scenario ofRSDA evaluation in which dataset-3 is used . . . 98
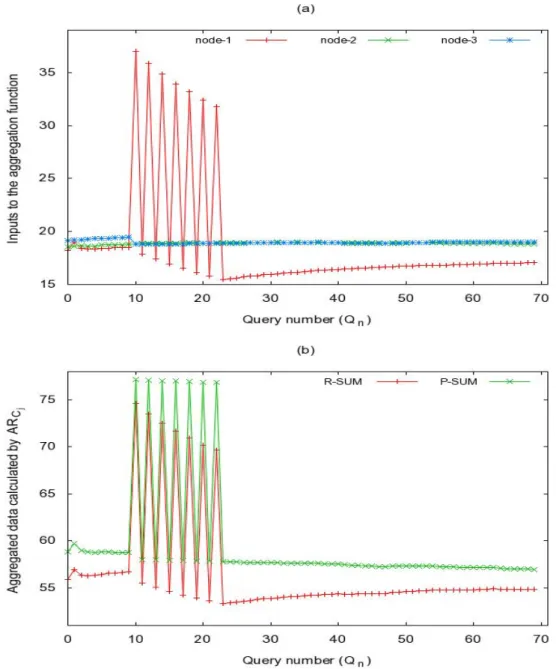
4.7 Reputation values ofCkrep during the third scenario of RSDAevaluation . . . 99
4.8 The third scenario ofRSDA evaluation in which dataset-4 is used . . . 100
5.1 A simplified estimation model for data aggregation in WSNs . . . 111
5.2 A simplified deployment area forE-RSDA . . . 115
5.3 A simplifiedE-RSDAmodel . . . 118
5.6 The second scenario of E-RSDA evaluation in which dataset-3 is used . . . 124
5.7 The third scenario ofE-RSDA evaluation in which dataset-4 is used . . . 126
5.8 Reputation values ofCkrep during the third scenario of E-RSDAevaluation . . . 127
5.9 The third scenario ofE-RSDA evaluation in which dataset-5 is used . . . 128
5.10 The fourth scenario of E-RSDA evaluation in which dataset-6 is used . . . 129
5.11 Reputation values of Ckrep during the fourth scenario of E-RSDAevaluation . . . 130
5.12 The fourth scenario of E-RSDA evaluation in which dataset-7 is used . . . 131
6.1 Classification of adversaries . . . 136
6.2 Key evolution in the proposed protocol . . . 142
6.3 State diagram of key disclosure . . . 146
6.4 Relations between keying materials and the significance of node compromise . . 147
1.1 Hardware’s specifications for three types of sensor nodes . . . 4
2.1 Security services provided in current secure data aggregation schemes . . . 41
2.2 Attacks vulnerabilities in current secure data aggregation schemes . . . 43
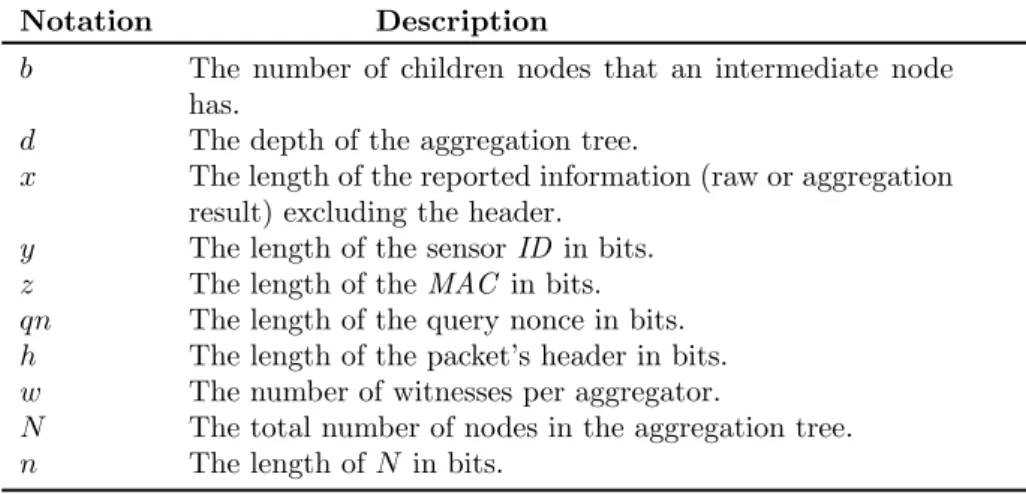
2.3 Description of notations used in the performance analysis section . . . 47
2.4 Number of bytes transmitted across the network to accomplish a single aggre-gation transaction . . . 51
3.1 Reputation components in current reputation-based trust systems . . . 74
3.2 Attacks vulnerabilities in current reputation-based trust systems . . . 75
4.1 Description of notations used in Chapter 4 . . . 84
4.2 Reputation table format as suggested inRSDA . . . 85
4.3 Datasets used in the experimental evaluation section . . . 92
4.4 Reputation components in current reputation-based trust systems . . . 102
4.5 Security services provided in current secure data aggregation protocols . . . 103
4.6 Attacks vulnerabilities in current reputation-based trust systems . . . 105
5.1 Description of notations used in Chapter 5 . . . 113
5.2 Data sets used in the experiment evaluation . . . 119
6.1 Description of notations used in Chapter 6 . . . 138
6.2 Memory overhead comparison . . . 149
6.3 Number of bits transmitted/received by a sensor . . . 151
6.4 Computation cost comparison . . . 153
The work contained in this thesis has not been previously submitted for a degree or diploma at any higher education institution. To the best of my knowledge and belief, the thesis contains no material previously published or written by another person except where due reference is made.
Signed:. . . Date:. . . .
The following papers have been published or presented, and contain material based on the content of this thesis.
Book Chapters:
– Hani Alzaid, Ernest Foo, Juan Manuel Gonz´alez Nieto, and DongGook Park. Secure Data Aggregation in Wireless Sensor Networks. In Anna Foerster and Alexander Foerster, editors,Emerging Communications for Wireless Sensor Networks,chapter 10, pages 183-228, InTech, Croatia. 2011.
– Hani Alzaid. Reputation-based Trust Systems in Wireless Sensor Networks. In Al-Sakib Khan Pathan, editor,Security of Self-Organizing Networks: MANET, WSN, WMN, VANET, chapter 20, pages 493-524, Auerbach Publications, CRC Press, Taylor & Francis Group, USA. 2010.
– Hani Alzaid, DongGook Park, Juan Manuel Gonz´alez Nieto, Colin Boyd, and Ernest Foo. A Forward & Backward Secure Key Management in Wireless Sensor Networks for PCS/SCADA. In Ra´ul Aquino Santos, Arthur Edwards, and Victor Rangel Licea, editors, Emerging Technologies in Wireless Ad Hoc Networks: Applications and Future Development, chapter 3, pages 41-60, IGI Global, USA. 2011.
Journal Articles:
– Hani Alzaid, Ernest Foo, Juan Manuel Gonz´alez Nieto, and DongGook Park. Secure Data Aggregation in Wireless Sensor Networks: A Comprehensive Review. Inter-national Journal of Communication Networks and Distributed Systems (IJCNDS), Invited Article, In press, InderScience Publishers.
– Hani Alzaid, Ernest Foo, Juan Manuel Gonz´alez Nieto, and Ejaz Ahmed. Mitigat-ing the On-Off Attacks in Reputation-based Secure Data Aggregation for Wireless Sensor Networks. Security and Communication Networks, In press.
Conference Papers:
– Hani Alzaid, DongGook Park, Juan Manuel Gonz´alez Nieto, and Ernest Foo. Miti-gating Sandwich Attacks against a Secure Key Management Scheme in Wireless Sen-sor Networks for PCS/SCADA.In Proceedings of the 24th IEEE International Con-ference on Advanced Information Networking and Applications, AINA’10, Perth, Australia, 20-13 April 2010, pages 859-865, IEEE Computer Society, 2010.
for PCS/SCADA.In Proceedings of the 1st International ICST Conference on Sen-sor Systems and Software, S-CUBE’09, 7-9 September 2009, Grand Hotel Duomo of Pisa, Pisa.
– Hani Alzaid, Ernest Foo, and Juan Manuel Gonz´alez Nieto. RSDA: Reputation-based Secure Data Aggregation in Wireless Sensor Networks. In Proceedings of the 9th International Conference on Parallel and Distributed Computing, Applications and Technologies, PDCAT’08, Dunedin, New Zealand, 1-4 December 2008, pages 419-424, IEEE Computer Society, 2008.
– Hani Alzaid, Ernest Foo, and Juan Manuel Gonz´alez Nieto. Secure Data Aggrega-tion in Wireless Sensor Networks: A Survey. In Proceedings of the 6th Australasian Information Security Conference: Conferences in Research and Practice in Infor-mation Technology, AISC’08, Wollongong, NSW, Australia, 22-25 January 2008, pages 93-105, Australian Computer Society Inc., 2008.
Introduction
A Wireless Sensor Network (WSN) is a highly distributed network of small wireless nodes deployed in large numbers to monitor the environment or other systems by the measurement of physical parameters such as temperature, pressure, or relative humidity [85, page 647]. Advancements in micro-electro-mechanical systems, digital electronics, and wireless commu-nications have enabled the development of a new generation of sensor nodes. These sensors are small in size and communicate in a multihop manner due to a short radio range, and are powered by a limited energy source. These sensor nodes collaborate to form an Ad Hoc Net-work capable of reporting netNet-work activities to a data collection sink. Recently, WSNs have been used in many promising applications, including habitat monitoring [76], military target tracking [55, 116], natural disaster relief [19], and health monitoring [82].
1.1
Background
WSN applications are classified into four classes [61]: (i) event detection, (ii) periodic reporting, (iii) base station querying, and (iv) tracking. These classes are briefly explained as follows:
Event Detection: The objective of sensor networks in this application class is to detect
rare events, such as forest fires or intrusions, and to promptly communicate a report of such an event to the sink.
Periodic Reporting: The objective of the sensor networks in this type of application is
to send periodic updates to the sink. Thus, there is regularity in terms of data gathering phases, and there is a steady flow of data from the sensor nodes to the sink. In-network data aggregation is useful in such applications because measurements of neighboring nodes are likely to be correlated, and could be used to reduce the amount of data that needs to be communicated to the sink. This in turn reduces communication energy expenditure of the nodes, and prolongs the lifetime of the network.
Figure 1.1: Main components of a sensor node
Base Station Querying: In several application classes, the sink is not interested in data
updates from all the nodes in the network. The sink may want updates from different regions at different times. Thus, requiring all the nodes to send their data to the sink at all times increases the energy consumption on communication as well as on computation. In such cases, the sink selectively queries a set of sensor nodes located in the region of interest. This results in a more energy-efficient use of resources.
Tracking: Tracking WSN applications are interested in detecting, localizing and
track-ing targets, and conveytrack-ing the relevant information to the sink, in a timely fashion. They combine some of the characteristics of the three application classes discussed earlier. The end device in WSNs, the sensor node, is composed of four basic units [123]: (i) sensing unit, (ii) processing unit, (iii) power unit, and (iv) transceiver unit as depicted in Figure 1.1. These four units are briefly explained as follows:
Sensing Unit: It consists of an array of sensors that can measure the physical
charac-teristics of its environment, like temperature, light, vibration, and others. Each sensor has the ability to sense environmental characteristics via the sensing unit and then use the Analog to Digital Converter (ADC) to convert the sensed analog data into digital.
Processing Unit: It is, in most cases, composed of an internal memory to store data and
application programs, and a microcontroller to process the data. The microcontroller can be considered as a highly constrained computer that contains the memory and interfaces required to create simple applications. This unit should be able to work with a limited resource of energy and process efficiently the digital data delivered by the sensing unit.
Power Unit: It provides the energy required by all the sensor components, and such
energy may come from either a battery or from renewable sources.
Transceiver Unit: It is able to send and receive messages through a wireless channel.
In other words, it gives the sensor the ability to talk to other sensor nodes and form an Ad Hoc Network.
Note that, the sensor node may have an external memory unit that works as a sec-ondary memory in order to keep a data log. Devising solutions for WSNs are not successfully accomplished by the simple adaptation of solutions designed for wired networks, or even for the more closely related, Ad Hoc Networks. This is due to the limitations and challenges that
WSNs have, which will be discussed in Section 1.2. A wireless Ad Hoc Network is a collection of wireless devices that can dynamically self-organize into an arbitrary and temporary topology to form a network without necessarily using any pre-existing infrastructure. In fact, wireless sensor networks could be considered as a specific subset of Ad Hoc Networks where end devices in wireless sensor networks are able to sense physical phenomena. However, there are great differences between Ad Hoc Networks and WSNs as listed in the following paragraphs [16, 18]:
Energy Source: Most WSNs are deployed in remote or hostile environments, whereas
Ad Hoc Networks are not. Consequently, replacing the batteries of these WSN nodes is more of a problem than it is for Ad Hoc Networks. As a result, the energy consumption of any solution designed for WSNs should be carefully considered at the design time.
Data Centric: Routing in WSNs is more likely to be querying attributes of the
phenomenon (attribute-based naming) rather than querying individual nodes addresses (IPs). For example, “what is the area where the temperature is over 70o celsius”? is more a common query in WSNs than the temperature read by a certain sensor node.
Node Density: The number of nodes in the WSN can be higher than the number
of nodes in the Ad Hoc Network. The nature of WSNs is that they are deployed in large scale environments, and each sensor has a limited transmission range. Therefore, dense deployment is necessary to achieve stable connectivity and to overcome the limited transmission coverage.
End Device: In Ad Hoc Networks, the end node device is less constrained than sensor
nodes. For example, the end device in Ad Hoc Networks, a laptop, has a larger memory and battery, and has a more powerful processor.
Network Structure: Whereas Ad Hoc networks are usually completely distributed
networks, WSNs have a central control system, which is the base station. Therefore, most traffic in WSNs is sent from the sensor nodes to the base station, and vice versa. Only in a few cases; one node will send information directly to another sensor node. However, it is normal for end devices of an Ad Hoc Network to communicate with other devices in the network as part of their normal functionality.
The rest of this chapter is organized as follows: Section 1.2 discusses limitations and chal-lenges in Wireless Sensor Networks. These limitations and chalchal-lenges affect the performance of any application intended to run on WSNs, especially data aggregation applications. Sec-tion 1.3 provides the motivaSec-tion for this thesis and highlights the importance of secure data aggregation. Then, the research objectives and contributions are stated in Section 1.4. Finally, the thesis structure is detailed in Section 1.5.
1.2
Challenges in Wireless Sensor Networks
As discussed above, WSNs have unique specifications and constraints as compared with Ad Hoc Networks, which makes the simple adaptation of existing solutions designed for traditional
Table 1.1: Hardware’s specifications for three types of sensor nodes
Specifications MICA2[30] FLECK[32] MICAZ[31]
Processor Atmega 128L Atmega 128L Atmega 128L
Memory
RAM 4 KB 4 KB 4 KB
ROM 128 KB 512 KB 128 KB
EPROM 512 KB 1 MB 512 KB
Power Supply 2AA 3AA & ISB 2AA
Data Rate 38.4 kbps 72 kbps 250 kbps Radio RR 152 m 500m 75m RF 868/916 MHz 913 MHz 2.4-2.48 GHz Current Draw Transmit∗ 27mA 5mA N/A Receive 10mA N/A 19.7mA
Sleep < 1µA 30uA 1µA
* Transmit with Maximum Power RR Radio Range
ISB Integrated Solar Board RF Radio Frequency
N/A Not Available
networks impractical. Thus, understanding the unique specifications of WSNs is highly rec-ommended to adapt any new idea with these specifications and make it feasible in the WSN real world [59]. These unique specifications and constraints are named challenges in the rest of this section, and classified into: (i) challenges in the end device (the sensor node), and (ii) challenges in the wireless sensor network, as follows [69, 107, 124, 129]:
1.2.1
Challenges in the End Device
All security approaches require a certain amount of resources for the implementation, including data memory, code space, and energy to power the sensor during the run of the approach. However, currently these resources are very limited in a tiny wireless sensor node. Table 1.1 lists the hardware specifications for three types of sensor node, namely MICA2 [30], FLECK [32], and MICAZ [31] and highlights the resource constraints in the end device of WSNs. We refer interested readers to the mini hardware survey done by Tatiana Bokareva for more information about the hardware specifications of more types of sensor node [10]. The challenges in the sensor’s hardware are discussed as follows:
Limited Memory: A sensor node is a tiny device with only a small amount of memory
and storage space for the code. In order to build an effective security mechanism, it is necessary to limit the code size of the security algorithm. For example, one common sensor type (MICA2) has 4K RAM, 128K program memory, and 512K flash storage [30]. The total code space of TinyOS, the de-facto standard operating system for wireless sensors, is approximately 4K [57], and the core scheduler occupies only 178 bytes. With
such a limitation, the code size for the proposed solution must be small.
Limited Energy Resource: The energy resource is the biggest challenge in WSNs.
It is assumed that once sensor nodes are deployed in a WSN, their batteries cannot be easily replaced due to the high operating costs of being deployed in remote areas. This will be discussed in Section 1.2.2. Some current versions of sensor nodes such as MICA2 are powered by 2AA batteries as shown in Table 1.1. Therefore, the battery charge taken with them to the field must be conserved to prolong the life of the individual sensor node and the entire sensor network. For example, when implementing a cryptographic function or protocol in a sensor node, the energy impact of the proposed solution should be considered.
Limited CPU Performance: The CPU used in MICA2 sensors, for example, is the
16 bit, 8MHz Texas Instruments MSP430 microcontroller [30]. Embedded processors are generally not as powerful as those in nodes of a wired network. As such, complex cryptographic algorithms should be avoided in WSNs.
Tamper-Resistant Hardware: The most obvious tamper-resistance strategies are
hardware-based ones, which involve extra cost to implement special ‘complex’ hardware circuits in the electronic device. To run these circuits, extra energy should be ensured. Due to the targeted low cost and the limited power resource existing in sensor nodes, the hardware-based tamper protection solutions are very limited [126].
1.2.2
Challenges in the Network
Sensor nodes are usually scattered randomly in the field to perform certain tasks. There is usually no infrastructure support for sensor networks. Sensor nodes self-organize to form a network. However, some network challenges exist. These challenges are discussed as follows:
Hostile & Remote Environment: Depending on the function of a particular sensor
network, the sensor nodes may be left unattended for long periods of time. Most WSNs are deployed in remote or hostile environments such as battlefields. Therefore, sensor nodes without tamper-resistant hardware cannot be protected from physical attacks since the deployment area accessible to anyone. An adversary could capture a sensor node or even introduce his own malicious nodes inside the network.
Random Topology: WSN is often deployed in random distribution since it is mostly
used in remote or hostile environments. Consequently, there is no chance to know its topology beforehand. Also, the topology after the deployment keeps changing because some sensors disappear due to drained resources, or for instance by being damaged, or faulty.
Latency: The communication range of most sensor nodes is limited in order to conserve
energy. According to Table 1.1, the MICA2, FLECK, and MICAZ sensor nodes have radio coverage area up to 152m, 500m, and 75m, respectively. To move a packet from one end of the network to another, a multi-hop routing approach is needed. In a congested wireless
sensor network, multi-hop routing and node processing can lead to great latency in the network, which makes synchronization among sensor nodes difficult. The synchronization issues can be critical to sensor security where the security mechanism relies on critical event reports and cryptographic key distribution.
Unreliable Communication: This challenge is inherited from Ad Hoc Networks, since
end devices in both WSNs and Ad Hoc Networks communicate with each other wirelessly. Packets may get damaged due to channel errors, lack of radio coverage, or by being dropped at highly congested nodes.
1.3
Data Aggregation and Security Challenges
In many WSN applications, a physical phenomenon is sensed by sensor nodes and then re-ported to the base station. To reduce the communication energy expenditure of sensor nodes, these applications should minimize the number of packets traveling across the network by elim-inating redundant data. Thus, these applications may employ in-network aggregation before the raw data reaches the base station.
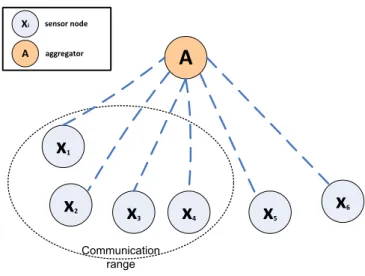
Typically, there are three types of nodes in WSN applications where in-network aggregation is implemented. These three types are: (i) normal sensor nodes, (ii) aggregators, and (iii) a querier (or queriers). The aggregators are intermediate nodes that collect raw data from down-stream sensor nodes, process the data and apply a suitable aggregation function. Then they transmit the processed data to an upper aggregator or to the querier who generated the query. The querier processes the received sensor data and derives meaningful information reflecting the events in the target field. It can be the base station or sometimes an external user who has permission to interact with the network, depending on the network architecture.
Let us consider the example depicted in Figure 1.2. The network topology contains 16 sensor nodes and performs the sum (SUM) as the aggregation function. Nodes N1, N2, ..., and N8 are normal sensor nodes that sense specific physical phenomena and report them back to upper nodes. Nodes N9, N10, ..., and N16 are aggregators that perform both sensing and aggregation activities. To answer a single aggregation query sent by the base station, every normal sensor node (nodes N1-N8) will report individually the sensed physical phenomena to the aggregators (nodes N9-N13). These aggregators add their sensed physical phenomena to the received raw data, and then apply the SUM aggregation function. Subsequently, they send the processed information to the upper aggregators (nodes N14-N15), which will do the same. At node N16, only one packet will be sent to the base station as an answer to its query. Thus, the total number of packets transmitted across the network is only 16 packets. If the in-network aggregation is not implemented in the example given in Figure 1.2, every node will respond to the received query and report its sensed information individually. Thus, the total number of packets, traveled across the network, would be 50 packets in order to deliver 16 packets to the base station. These 16 packets are the nodes’ responses to the base station’s query.
N16 N14 N15 N10 N9 N6 N5 N7 N8 N11 N12 N13 N1 N2 N3 N4 r1= 1 r2= 4 r3= 7 r4= 6 r5= 4 r6= 1 r7= 0 r8= 2 r9= 7 r10= 7 r11= 2 r12= 3 r13= 0 r15= 3 r14= 9 r16= 2 A@9= r7 + r8 + r9 =9 A@15= r15 + A@9 + A@10 =24 A@16= r16 + A@14 + A@15 =58
ri represents the reading from node i.
Ni represents the node i.
A@i represents the aggregation result
at node i.
Base Station
Nxx Aggregator
Normal Sensor Nxx
Figure 1.2: An aggregation scenario using the SUM aggregation function
Previous studies [72,96,128] show that data transmission consumes much more energy than computation. As illustrated in the two examples given above, data aggregation can greatly help to reduce this consumption by eliminating redundant data. This in turn helps prolong the network lifetime. Most existing schemes for data aggregation are under the threat of various types of attacks [128]. Among them, the node compromise is usually considered as one of the most challenging issues in the security of WSNs [8, 54, 69, 69, 95, 107, 135]. In a node compromise attack, an adversary tries to physically tamper with a node in order to extract the cryptographic secrets. This attack can be very harmful depending on the security architecture of the network. For example, when an aggregator node is compromised, it is easy for the adversary to change the aggregation result and inject false data into the WSNs. Because of this, the need for secure data aggregation is raised and its importance needs to be highlighted.
1.4
Research Objectives
According to the discussion in Section 1.3, the node compromise attack is the most challenging security threat. Simple adaptation of security solutions designed for the wired and Ad Hoc networks is impractical due to the unique characteristics of WSNs as discussed in Section 1.2. Two main directions exist to circumvent this important threat [36]. The first one involves in improving the tamper-resistance of the nodes in order to increase the effort of the attacker. However, tamper-resistant mechanisms are costly for small sensor nodes and are therefore usu-ally not present on these devices. The second alternative adopts a reputation-based approach, which monitors the network activities and tries to detect events related to the node compro-mise. It assumes that a node capture will provoke some noticeable events, such as inconsistent sensing or aggregation results, a displacement or removal of a node, and malicious routing
activities [71].
The objective of this thesis is to address the security issues of data aggregation in wireless sensor networks, and study the strengths and weaknesses of both the cryptographic-based and reputation-based secure data aggregation schemes found in the literature. Our goal is to design a robust secure data aggregation scheme that minimizes the use of heavy cryptographic mechanisms, defends against most security attacks, and securely computes the aggregation.
Our research contributions in this thesis are summarized as follows:
Define the security for data aggregation in wireless sensor networks. The thesis takes a step further and stipulate the main components of a robust secure data aggregation scheme as follows:
– Ability to provide fair approximations of the sensor readings even though a limited number of nodes are compromised.
– Dynamic response to attack activities by rejecting incorrect aggregation results as soon as possible, possibly by nodes in the neighborhood, not at the base station level.
These properties should work together to provide accurate aggregation results securely without exhausting the network’s limited resources. In contrast with existing secure data aggregation definitions, the proposed definition covers the unique characteristics that wireless sensor networks have.
Analyze the relationship between security services and the adversarial model considered in existing secure data aggregation schemes, in order to provide a general framework of required security services. This framework helps identify the minimum security services that a secure data aggregation design should provide to defend against specific types of adversaries.
Analyze both cryptographic-based and reputation-based secure data aggregation schemes. This analysis covers security services provided by these schemes and their robustness against security attacks. It is believed that this analysis can help to identify the security level in these schemes. Surprisingly, most of the examined data aggregation schemes are vulnerable to selective forwarding attacks.
Propose an efficient reputation-based secure data aggregation scheme that overcomes the weaknesses in other schemes found in the literature. The security advantages provided by this proposal are realized by integrating aggregation functionalities with: (i) a reputation system, (ii) an estimation theory, and (iii) a change point detection mechanism. The significance of the proposal is two-fold: (i) it mitigates the effect of On-Off attacks on aggregation results, and (ii) it distinguishes between an abrupt change and a temporary departure in heterogeneous environments. The proposal is tested in different scenarios to validate the superior performance of the proposal. The experiment results showed that the proposal is able to detect On-Off attacks as long as the attack frequency is
smaller than the buffer window size. The results showed that the proposal follows the reputation-based estimate behavior during the On-Off attack, but it has a better reaction once the attack was over. This proposal re-initializes the estimator as soon as the end of the On-Off attack has been recognized. This ensures a quick convergence afterwards with the reputation-based aggregation results. To the best of our knowledge, this proposal is the only secure data aggregation scheme in the literature that is able to mitigate the On-Off attack.
Propose a secure key management protocol in order to distribute essential pairwise and group keys among the sensor nodes. The protocols also helps to revoke misbehaved nodes and isolate them from the network. Importantly, the proposal provide backward & forward secrecy that are not provided by similar schemes such as Nilson et al.’s scheme [88]. The design idea of the proposed scheme is the combination between Lamport’s reverse hash chain as well as the usual hash chain to provide both past and future key secrecy. The proposal avoids the delivery of the whole value of a new group key for group key update; instead only the half of the value is transmitted from the base station to the sensor nodes. The performance analysis result shows that a sensor node in the proposal consumes approximately 52614.8µJ and 635.2µJ in order to update the pairwise key and the group key, respectively. This energy consumption includes the communication cost and the computation cost. The proposal’s energy consumption for the pairwise key update protocol is 287.6µJ more than Nilsson et al.’s scheme. This difference is due to the security enhancements that are required to overcome the weaknesses in Nilsson et al.’s scheme, as will be discussed in Section 6.2. To update the group key, the proposal consumes 308.8µJ more energy than Nilsson et al.’s scheme. These additional costs result from defeating the Sandwich attack and overcoming the weaknesses of Nilsson et al.’s scheme.
1.5
Outline
The organization of the thesis is as follows:
Chapter 2: This chapter is about cryptographic-based secure data aggregation. We first
give introductory information about secure data aggregation in WSNs, which defines the data aggregation security considering the unique characteristics of WSNs. Then, we highlight the security requirements for data aggregation in WSNs, since the thesis is centered on provid-ing security to data aggregation applications. We also discuss the security attacks against cryptographic-based secure data aggregation schemes. Then, we survey, in detail, some of the current secure data aggregation schemes and classify them into two models: (i) the single ag-gregator, and (ii) the multiple aggregator model. We also undertake security and performance analyses of current cryptographic-based secure data aggregation schemes. The security anal-ysis covers the security services the current schemes provide and their robustness against the security attacks discussed in this thesis. The performance analysis covers the number of bits transmitted in order to accomplish the aggregation phase in some selected schemes.
The contents of this chapter have appeared in the following publications:
Hani Alzaid, Ernest Foo, and Juan Manuel Gonz´alez Nieto. Secure Data Aggregation in Wireless Sensor Networks: A Survey. In Proceedings of the 6th Australasian Information Security Conference: Conferences in Research and Practice in Information Technology, AISC’08, Wollongong, NSW, Australia, 22-25 January 2008, pages 93-105, Australian Computer Society Inc., 2008.
Hani Alzaid, Ernest Foo, Juan Manuel Gonz´alez Nieto, and DongGook Park. Secure Data Aggregation in Wireless Sensor Networks: A Comprehensive Review. International Journal of Communication Networks and Distributed Systems (IJCNDS), Invited Article, In press, InderScience Publishers.
Hani Alzaid, Ernest Foo, Juan Manuel Gonz´alez Nieto, and DongGook Park. Secure Data Aggregation in Wireless Sensor Networks. In Anna Foerster and Alexander Foerster, editors,Emerging Communications for Wireless Sensor Networks,chapter 10, pages 183-228, InTech, Croatia. 2011.
Chapter 3: This chapter investigates the use of reputation-based systems to provide trust
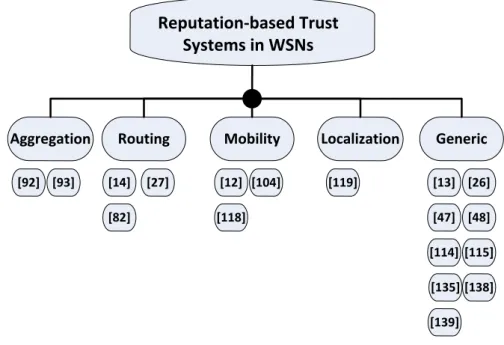
among sensors in WSNs. We first discuss security attacks against reputation-based trust sys-tems. Then, we present a comprehensive survey of the state-of-the-art in reputation-based trust systems for WSNs and classify these systems to five categories: (i) generic, (ii) local-ization, (iii) mobility, (iv) routing, and (v) aggregation. Finally, we compare in detail these reputation-based trust systems. The comparison includes: (i) investigating the visibility of the main components of the reputation systems, and (ii) studying the appearance of attacks, which is related either to WSNs or reputation systems, in existing reputation-based systems.
The contents of this chapter have appeared in the following publication:
Hani Alzaid. Reputation-based Trust Systems in Wireless Sensor Networks. In Al-Sakib Khan Pathan, editor, Security of Self-Organizing Networks: MANET, WSN, WMN, VANET,chapter 20, pages 493-524, Auerbach Publications, CRC Press, Taylor & Francis Group, USA. 2010.
Chapter 4: In this chapter, we propose a Reputation-based Secure Data Aggregation (RSDA)
for wireless sensor networks. RSDAminimizes the use of heavy cryptographic mechanisms, and integrates the aggregation functionalities with the advantages that are provided by a reputa-tion system in order to enhance the network lifetime and the accuracy of the aggregated data. The chapter also discusses performance and security analyses of RSDA. In the performance analysis,RSDAis tested in three scenarios, depending on the adversary capability to affect the aggregation results, as follows: (i) no attack on the data, (ii) abrupt change, and (iii) “1-per-2” strategy-based On-Off attacks. The security analysis of RSDA follows the same methodology used in Chapters 2 and 3.
The contents of this chapter have appeared in the following publication:
Hani Alzaid, Ernest Foo, and Juan Manuel Gonz´alez Nieto. RSDA: Reputation-based Secure Data Aggregation in Wireless Sensor Networks. In Proceedings of the 9th Interna-tional Conference on Parallel and Distributed Computing, Applications and Technologies, PDCAT’08, Dunedin, New Zealand, 1-4 December 2008,pages 419-424, IEEE Computer Society, 2008.
Chapter 5: This chapter focuses on investigating the ability to mitigate the On-Off attack
where the adversary aims to disrupt the system’s overall performance without being detected or excluded from the network. The proposal in this chapter extendsRSDA, the contribution of Chapter 4, by adding an estimation theory and a change point detection mechanism. Through extensive simulations, it can be shown that this addition helps defend against On-Off attacks and enhances the data accuracy in the aggregation results. We first provide a brief overview of some techniques used in the proposal, namely: the estimation theory, and the change detection mechanism. Then, we explain the damage caused by the On-Off attack onRSDA. Finally, we discuss in detail the proposed solution. The solution is tested in four scenarios, depending on the adversary’s capability to affect the aggregation results, as follows: (i) no attack on the data, (ii) abrupt and incipient change, (iii) “1-per-2” strategy-based On-Off attacks, and (iv) “1-per-3” strategy-based On-Off attacks.
The contents of this chapter have appeared in the following publication:
Hani Alzaid, Ernest Foo, Juan Manuel Gonz´alez Nieto, and Ejaz Ahmed. Mitigating the On-Off Attacks in Reputation-based Secure Data Aggregation for Wireless Sensor Networks. Security and Communication Networks,In press.
Chapter 6: This chapter proposes a secure key management scheme which helps distribute
and renew pairwise and group (cell) keys to sensor nodes. It also helps to revoke misbehaved nodes and isolate them from the network. The design idea of the proposed scheme is the com-bination of Lamport’s reverse hash chain and the usual hash chain to provide both past and future key secrecy. We first define the term “future & past secrecy” and then use it instead of the similar terminology “forward & backward secrecy”, which has always been quite confusing. Then, we discuss the motivation behind the proposal by analyzing the security strengths and weaknesses of current key management schemes. We then present two variants of the proposed key management scheme. Finally, a performance analysis of these two variants is discussed. This analysis covers: (i) memory overhead, (ii) communication cost, and (iii) computation cost.
The contents of this chapter have appeared in the following publications:
Hani Alzaid, DongGook Park, Juan Manuel Gonz´alez Nieto, Colin Boyd, and Ernest Foo. A Forward & Backward Secure Key Management in Wireless Sensor Networks for PCS/SCADA. In Proceedings of the 1st International ICST Conference on Sensor Systems and Software, S-CUBE’09, Grand Hotel Duomo of Pisa, Pisa, 7-9 September 2009,pages 66-82, Springer, 2010.
Hani Alzaid, DongGook Park, Juan Manuel Gonz´alez Nieto, and Ernest Foo. Mitigating Sandwich Attacks against a Secure Key Management Scheme in Wireless Sensor Networks for PCS/SCADA.In Proceedings of the 24th IEEE International Conference on Advanced Information Networking and Applications, AINA’10, Perth, Australia, 20-13 April 2010, pages 859-865, IEEE Computer Society, 2010.
Hani Alzaid, DongGook Park, Juan Manuel Gonz´alez Nieto, Colin Boyd, and Ernest Foo. A Forward & Backward Secure Key Management in Wireless Sensor Networks for PCS/SCADA. In Ra´ul Aquino Santos, Arthur Edwards, and Victor Rangel Licea, editors, Emerging Technologies in Wireless Ad Hoc Networks: Applications and Future Development,chapter 3, pages 41-60, IGI Global, USA. 2011.
Chapter 7: Finally the thesis contributions are summarized in this chapter. Several open
Secure Data Aggregation in
Wireless Sensor Networks
Studies by Wagner [128] and Krishnamachari et al. [72] showed that data transmission con-sumes much more energy than computation. Data transmission accounts for 70% of the en-ergy cost of computation and communication for the SNEP protocol [96]. Data aggregation can significantly help to reduce this consumption by eliminating redundant data. However, aggregators are vulnerable to attacks such as node compromise attacks, especially if they are not equipped with tamper-resistant hardware. When an aggregator node is compromised, it is easy for the adversary to change the aggregation result and inject false data into WSNs. Due to the WSNs unique characteristics discussed in Chapter 1, devising security protocols for WSNs is complicated and may not be successfully accomplished by the simple adaptation of security solutions designed for wired networks. Unfortunately, the security mechanisms used in other network environments are not appropriate for WSN domains, since they are typically based on public key cryptography, which is too expensive for sensor nodes.
There are two approaches to circumvent the node compromise threat. The first one, which is the focus of this chapter, involves in increasing the needed efforts of the adversary to succeed in launching the attack. This can be done by employing some cryptographic-based techniques. For example, the Merkle hash tree is used in Przydatek et al.’s Scheme in order to facilitate the verification process at the querier and ensure the correctness of the aggregation results (more details are given in Section 2.3). The second alternative mitigates node compromise attacks by adopting a reputation-based scheme to monitor the network activities and detect events related to the node compromise. A detailed discussion of the second approach is presented in Chapter 3.
Our contributions in this chapter are four-fold:
Define the security for data aggregation in WSNs. In contrast with existing secure data aggregation definitions, the proposed definition covers the unique characteristics that
WSNs have.
Present a survey of the “state-of-the-art” in secure data aggregation schemes. These schemes are then classified into two groups according to the number of aggregator nodes, and whether the verification phase of the aggregation result is considered or not.
Explore the relation between the security services and the adversarial model considered in existing secure data aggregation schemes for possible general framework. This framework helps identify the minimum security services that a secure data aggregation design should provide to defend against a specific type of adversary.
Evaluate current cryptographic-based secure data aggregation schemes. The evaluation is composed of: (i) security analysis, and (ii) performance analysis. The security analysis covers the robustness against security attacks discussed in this chapter, and the security services provided. The performance analysis focuses on calculating the number of bits transmitted within the network, in order to show which secure data aggregation scheme is more energy hungry and sends more information to accomplish the scheme objectives. The rest of the chapter is organized as follows: Section 2.1 gives introductory information about secure data aggregation in WSNs. Section 2.2 lists security concerns in data aggregation, and highlights different capabilities that an adversary may have against a secure data aggregation scheme. Section 2.3 surveys, in detail, some of the current cryptographic-based secure data aggregation schemes and classifies them into two models: (i) the single aggregator, and (ii) the multiple aggregator model. Then, a security analysis of these schemes is discussed in Sec-tion 2.4. The analysis covers the security services these schemes provide, and their robustness against the security attacks mentioned above. Section 2.5 discusses the performance analysis of some of these schemes. Finally, the chapter is concluded in Section 2.6.
2.1
Secure Data Aggregation in Wireless Sensor Networks
The motivation behind secure data aggregation in WSNs is explained in Section 1.3. Unfortu-nately, the design principles for secure data aggregation schemes are poorly understood. There is no clear definition of what secure data aggregation should mean, what security requirements a scheme should have, and what adversary capability a scheme should defend against. Existing schemes might have one or more of the security requirements, depending on how secure data aggregation has been addressed, and the strength of the expected adversary. For example, secure data aggregation has been addressed in Przydatek et al.’s scheme from the point of view of detecting forged data aggregation values [99]. This does not cover security issues such as how to elect aggregators, rotate aggregation functionality between nodes, or how to set up trust between aggregators and sensor nodes. Also, some schemes provide more security re-quirements than others, as discussed in Section 2.4, or send more bits than others, as discussed in Section 2.5. Generally speaking, there is no common ground that allows for a complete comparison between different aggregation schemes.
Secure data aggregation is defined as “the efficient delivery of the summary of sensor read-ings that are reported to an off-site user in such a way that ensures these reported readread-ings have not been altered” [21, 99]. This definition considers WSN applications where the querier is located outside the deployment area and a base station acts as an aggregator. Shi and Perrig [115] highlight error sources that affect the aggregated data, and define secure data aggregation as “the process of obtaining a relative estimate of the sensor readings with the ability to detect and reject reported data that is significantly distorted by corrupted nodes or injected by malicious nodes”. However, rejecting reported data injected by malicious nodes consumes the network resources, specifically the nodes’ batteries. The malicious packet will be processed by intermediate nodes until it reaches the verifier, which is normally the base station. The damage caused by malicious nodes or compromised nodes should be reduced by adding a self-healing property to the network. This property helps the network to learn how to handle new threats through extensive monitoring of network activities. Therefore, we take a step further and stipulate the main components of a robust secure data aggregation scheme as follows:
Ability to provide fair approximations of the sensor readings even though a limited num-ber of nodes are compromised.
Dynamic response to attack activities by rejecting incorrect aggregation results as soon as possible, possibly by nodes in the neighborhood, not at the base station level. These properties should work together to provide accurate aggregation results securely without exhausting the network’s limited resources.
2.1.1
Security Requirements for Data Aggregation Security
Since WSNs share some properties with traditional wireless networks, data security require-ments in WSNs are similar to those in traditional networks [96, 115]. This section discusses security requirements for strengthening attack-resistant data aggregation schemes for WSNs. These security requirements are as follows:
Data Confidentiality: ensures that information content is never revealed to
unau-thorized parties. In WSN applications where in-network aggregation is required, data confidentiality can be implemented in two ways: (i) a hop-by-hop basis and (ii) an end-to-end basis. In the hop-by-hop basis, any aggregator node needs to decrypt the received encrypted data, apply an aggregation function, encrypt the aggregated data, and send it to an upper aggregator point. This kind of confidentiality implementation requires extra computation, which leads to more delays in the network and increases the energy consumption. It also facilitates the adversary’s mission. For example, the secrecy of sensed data is disclosed once any intermediate node is compromised. In the end-to-end basis, an aggregator does not need to perform decrypting and encrypting on received data; it instead applies aggregation functions directly on encrypted data by using some techniques such as homomorphic encryption [131]. End-to-end confidentiality greatly reduces energy consumption since there is no need for decryption and encryption of the received encrypted data at intermediate nodes.
Data Integrity: ensures that a message has not been altered, either maliciously or accidentally, in transit. Even if the network provides data confidentiality, there is still a possibility that data integrity can be affected. In certain applications, data confidentiality is not as important as data integrity. It is sometimes acceptable for an adversary to eavesdrop and learn about aggregation results, but not to change them. Suppose a secure data aggregation scheme provides only data confidentiality in order to defend against an adversary that is capable of compromising an aggregator node. The adversary could then alter the aggregation result and mislead the base station. Moreover, even without the existence of an adversary, data might be damaged or corrupted due to the nature of the wireless environment.
Data Freshness: ensures that the data are recent and no old messages have been
replayed, thereby protecting data aggregation schemes against replay attacks. In this kind of attack, it is not enough that these schemes provide only data confidentiality and data integrity, because an adversary able to intercept even encrypted messages could later replay them to disrupt the data aggregation results. This requirement is important in real time applications or key management schemes. For example, an adversary could replay an old distributed shared key and mislead a sensor concerning the current cryptographic key used to secure sensing information or aggregation results.
Data Availability: ensures that the network is alive and data are accessible. In the
presence of malicious nodes, it is highly recommended that the network react to these bad (compromised) nodes and eliminate them. Once an adversary gets into the network by compromising some legitimate nodes, the adversary can affect network services, especially in those parts of the network where the attack was launched. It is preferable that a secure data aggregation scheme contains the following mechanism to ensure a reasonable level of data availability in the network:
– Self-healing: which can diagnose and react to an adversary’s activities, especially
when some legitimate nodes are compromised, and then start corrective actions based on defined policies to recover the network or isolate the compromised nodes. The reason for adding cryptographic mechanisms is to protect WSNs from adversaries whose goals may include decreasing WSN lifetime. However, adding these cryptographic mechanisms comes at cost. Thus, these mechanisms should be carefully implemented to fit WSNs characteristics.
Authentication: allows a receiver to verify whether a message is sent by the claimed
sender or not. An adversary would not be able to participate and inject data into the network without valid authentication keys. If entity authentication is not implemented, an adversary could impersonate other nodes and get access to sensitive data. In the aggregation context, without entity authentication, an adversary could masquerade as an aggregator and claim to a querier that an aggregation result isx′ instead ofx.
2.2
The Expected Adversarial Model and Security
Con-cerns
WSNs are vulnerable to different types of attack. The damage caused by these attacks varies from one scheme to another according to the adversarial model.
One of the potential vulnerabilities in WSNs results from compromising its sensor nodes, given the lack of tamper-resistant packaging [54, 135]. An adversary could gain control of one or more sensor nodes and readily access sensitive information. It is usually assumed that node capture is easy in WSNs due to a lack of physical restrictions that help control access to the de-ployment area in outdoor environments [8]. This attack is referred to as the supervision attack and sometimes the physical attack. Considering the data aggregation scenario, once a node has been taken over, all the secret information stored on it can be extracted and the adversary can then participate in aggregation activities. Even worse, the adversary may also inject their own commodity nodes into the network by fooling nodes into believing that these commodity nodes are legitimate members of the network, especially if there is no proper authentication scheme in place. A simulation study showed that network operation and maintenance can be easily jeopardized and network performance will severely degrade once a single node starts misbehaving [80].
The purpose of this section is to highlight different capabilities that an adversary may have against a secure data aggregation scheme. Before we classify expected adversaries, possible security attacks related to WSNs are discussed in the following section.
2.2.1
Security Attacks
This subsection studies how attacks related to WSNs (WSNs attacks) can affect any proposal to secure data aggregation in WSNs. WSNs attacks are discussed as follows:
Sybil Attack (SY)
The Sybil attack1 is a type of attacks where the adversary is able to present more than one identity (node) within the network to deceive other nodes [39]. A node that wishes to conduct the SY attack can affect an aggregation scheme in different ways: it can (i) create multiple identities to generate additional votes in the aggregator election phase to make a malicious node an aggregator instead of legitimate nodes, (ii) generate multiple entries to an aggregation function with different incorrect readings, or (iii) create multiple identities to affect reputation values of legitimate nodes in reputation-based applications by falsely degrading legitimate node reputation values.
Let us consider the example given in Figure 2.1 where an adversary creates fake IDs in order to affect the overall performance of the network. Figure 2.1-A shows a sketch of the normal scenario without any adversary. The real path starts from node A(D) and ends at
A
C
B
D
A
C
B
D
B
`
A. Normal Scenario
B. Modified Scenario
B
B
Adversary Compromised Sensor Genuine Sensor
Figure 2.1: Sybil Attack
node D(A). NodesB and C are adjacent neighbors. A simple form of the SY attack occurs when an adversary has the ability to compromise some sensor nodes. Suppose that an adversary succeeded in compromising nodeBand then manipulating the route discovery messages within the routing activities. Thus, the adversary can add another node to the network, which is nodeB′ in Figure 2.1-B. Now, the adversary can communicate with nodeAusing nodeBand communicate with nodeC using nodeB′. It can perform malicious activities in the network and trickily blame node B′ (or nodeB) for those activities and leave the reputation value of nodeB (or nodeB′) untouched.
Selective Forwarding Attack (SF)
It is sometimes assumed that each node will accurately forward received messages. However, a compromised node may refuse to do so. It is up to the adversary that is controlling the compromised node whether to forward received messages or not [67]. To put it in another way, the process of stopping the propagation of certain messages at the compromised node is under the control of the adversary. Once the adversary has succeeded in launching a SF attack, it can affect the propagation of the reputation information, such as direct observations across the network. Note that SF attacks are most effective when the attacking nodes are included in the path of the data flow.
Figure 2.2 depicts a simplified scenario of a SF attack. The scenario follows the single aggregator model [6], where node A acts as an aggregator. In Figure 2.2-A, an adversary succeeded in compromising nodeB but behaved well and forwarded the request message sent by nodeA. Later on, node B, which is still under the adversary control, drops the response from D as in Figure 2.2-B. Since the aggregator has not received any reply for its recent request, node A updates its reputation table and reduces the reputation value of node D
A
C
B
D
A
C
B
D
A. Request Path
B. Reply Path
X
B B Adversary Compromised Sensor Genuine SensorFigure 2.2: Selective Forwarding Attack
as in Figure 2.2-B. Note that the reputation table does not usually contain any reputation information for the node that maintains the table. For example, the reputation table which is maintained by nodeA in Figure 2.2 does not have reputation information for the node itself (nodeA).
Replay Attack (RE)
Some WSN applications are vulnerable to replay attacks where an adversary is able to eavesdrop on the traffic and replay old messages. Replay attacks are the easiest, because the adversary does not need to physically capture a sensor node and get access to its internal memory, or analyze intercepted encrypted data. In the reputation-based applications context, an adver-sary can record some reputation information, which has been exchanged wirelessly between sensor nodes, without even understanding its content and then replay them (with no changes) to mislead other nodes and make their reputation tables out-dated.
Figure 2.3 describes a simplified scenario of a RE attack in which the adversary has captured the reputation update message at a certain timet1 (see Figure 2.3-A), and then re-injected it
at timet2 wheret2 > t1(see Figure 2.3-B). With no proper verification, nodes B, C,andD
will accept this re-injection and end up being out-dated and thus potentially with incorrect reputation values.
Spoofed Data Attack (SD)
In this type of attack, an adversary alters intercepted data in order to inject false data into the network and affects the reputation values. This attack cannot be launched alone; the ad-versary needs to combine either a RE attack or node compromise attack with a SD attack. In
A
C
B
D
A
C
B
D
A. Reputation
Update at
t
1B. Reputation
Update at
t
2 B B Adversary Compromised Sensor Genuine SensorFigure 2.3: Replay Attack
A
C
B
D
A
C
B
D
A. Normal Scenario
B. Modified Scenario
B
B
Adversary Compromised Sensor Genuine Sensor
the former, the adversary first eavesdrops on the traffic, captures some reputation information in understandable format, performs some changes on the captured information, and then re-injects it into the network. In the latter, the adversary first needs to overtake a sensor node, and can then affect the reputation calculation by falsely claiming that his direct observation for node Ni is Ri
′
(instead of the correct Ri). Ri
′
is then propagated to neighboring nodes which are misled by the received indirect observation Ri
′
and thus their calculations for the reputation value ofNiare affected.
Figure 2.4 presents a simplified scenario of a SD attack once the adversary has succeeded in compromising nodeB. The adversary, in Figure 2.4-B, during the reputation update phase, claims that the reputation value for node A isRA
′
notRA and then sends it to neighboring nodesCandD. Therefore, nodesCandDwill useRA
′
as an indirect observation for nodeA
when they calculate the reputation value for nodeA.
2.2.2
Adversary Classification
Current cryptographic-based secure data aggregation schemes are threatened by adversaries with different capabilities. The following criteria are used to classify adversaries:
The adversary can take over a sensor node. The adversary can then read and modify all the software code and configurations, including secret keys, installed in the sensor node. For example, once the adversary has succeeded in compromising a sensor node, the ad-versary can then alter any software installed in this node. In other words, adversaries can be: passive oractive. Passive adversaries take advantage of the wireless communication nature (broadcasting) and eavesdrop on the traffic to obtain any important information about the sensed data. Active adversaries interact with WSNs by injecting packets, destroying or compromising nodes, extracting sensitive data, and stopping or delaying packets from being delivered to a querier, etc. They can launch any type of attack listed in Section 2.2.1.
The adversary has access to the whole network. As discussed in Section 1.3, there are three components in WSNs: sensor nodes, aggregators, and a base station with different functionalities and capabilities. The adversary’s ability to interact with these compo-nents is determined by the network access. Passive adversaries withtotal network access can listen to all communications between sensor nodes in the network; and active adver-saries can interact maliciously with all components in WSNs (nodes, aggregators, base stations) by launching any attack listed in Section 2.2.1. However, this type of access is not common in most WSN applications. Moving from thetotal network access capability to partial network access, passive adversaries can listen to communications between a subset of nodes in the network. Active adversaries can interact only with a subset of nodes in the WSN.
According to the above two criteria, adversaries are divided into four distinct types as shown in Figure 2.5. Type I is the weakest adversary: capable of eavesdropping on communications
Figure 2.5: Classification of adversaries
in some parts of the network in which it has access to, but not capable of interacting with the network. To the best of our knowledge, this type of adversary has never been considered in any secure data aggregation scheme. Type IV is the strongest. It refers to an active adversary that has total access to the network. This type of adversary is interested in affecting the data aggregation results by launching any attack listed in Section 2.2.1 against any network component (nodes, aggregators, base stations). We believe that this adversary classification can help to make better evaluation of new schemes and facilitate making decisions on which scheme is more suitable for specific conditions, as discussed in Section 2.4.3. In the following section, current cryptographic-based secure data aggregation schemes are discussed.
A. Single Aggregator
B. Multiple Aggregator
Base Station
Aggregator Sensor
Figure 2.6: A sketch of single and multiple aggregator models
2.3
Current Secure Data Aggregation Schemes
To the best of our knowledge, there have been four surveys in which current secure data aggre-gation schemes are compared. Setia et al. [112] discussed the security vulnerabilities of data